7.9. C4ISR |
Although information technology is today largely for the purpose of exercising civil (consumer) goals, one can not ignore its importance and the armed forces of some countries. In essence, the development of the armed forces and most of the knowledge acquired technology has come to the civilian area, of course, keeping the latest breakthroughs. So in all the armed forces command system as a subsystem of the entire combatants. Demands on the command of the armed forces are under increasing pressure, which reduces the ability to make optimal decisions with previous methods. Introducing commanding information system greatly enhances the ability to make optimal decisions.
The basic task of commanding information system is based on the collected data, communication channels transmit data to the computer, which will be a specific (military) software enable the display processed data is displayed in a form that allows the command situation assessment, decision making, issuing orders and supervision their execution. The system can be classified according to the following general principles:
Besides the listed divided their contents, during the development of combatants have used some more, but is currently often cited C4ISR, which operates on the principles shown in Figure 7.9.1a. Notebook in Figure 7.9.1b resembles some home kit, but my operating system and software are not even close to that, except for 'toys' characteristics.
|
|
| Figure* 7.9.1 Basic Principle of C4 system. ( + / - ) |
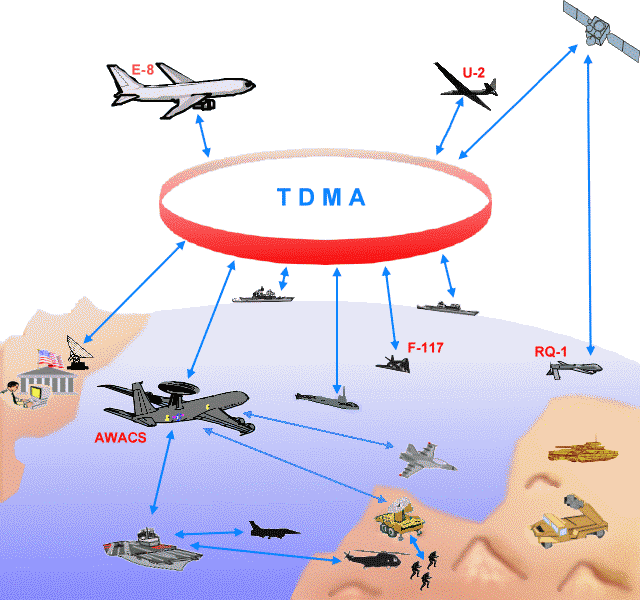
On the basis of intelligence, surveillance, reconnaissance, early warning systems in operation, may be made timely and valid decisions. The complexity of the whole system is best illustrated by a number of different resources shown in Figure 7.9.1a used, are, although in essence there are far more. Principle of operation of the communication system based on TDMA (Time Division Multiple Access) technology, which is a basic feature of the transmission of digital signals through the media (communication channel) in a way that each user has its own time 'slice' which is associated with the other participants in the group inside the same high-frequency range. Use the same communication channel and newsgroup participants do not interfere with each other, because each uses a different short time slots for communication. During each time a sequence is transmitted one part of the signal, which is received at the destination when all parts of 'draw' in the original signal. Inversely when transmitting, the signal is divided into small pieces that are sent when the time comes to send them - time division multiple access. Waiting time between two access rights TDMA cycle is so little so this time pattern of communicating end user does not notice. Red ring in the picture symbolizes the entire communications network designed to wired and wireless principles. The technology used by today's 'mobile phones', the user is assigned a unique time interval within the communication channel. Of course, almost all of the wireless communication that defines strict requirements of security and resilience of the system to interference and jamming.
C4ISR systems are based on the aircrafts (various versions of AWACS) or geostationary satellites. But even that should not make much difference because the unmanned aircraft 'RQ-1 Predator' or similar to an antenna through which it communicates with geostationary satellites and also sends its data in TDMA cycle or across it receives orders. Aircraft for surveillance and monitoring of ground targets (such as E-8 JSTARS) is more like a large passenger plane, not on some sort of weapon. Old 'U-2 Dragon Lady', known for investigative tasks of the onetime Soviet Union when he once shot down, he had countless revisions and is still used as a spy-reconnaissance aircraft. Unmanned aircraft 'RQ-1 Predator' in some segments work better than conventional aircraft with the pilot. New technologies make miracles. Radar reflection planes 'F-117 Nighthawk' is so small it looks like a bird, because it is basically made from carbon fiber and coated with special paints that absorb radar electromagnetic 'rays'. Unmanned aircraft, unmanned vehicles and robots are taking an increasing share of the combat systems, and their development is going in terms of the autonomous action. Satellite systems other than the above is used for GPS navigation and global system against jamming.
Of course, the system shown in the figure can not have, nor need, a small vassal states like Croatia. The presented system according to the principles of U.S. DoD (Department of Defense) and was developed by the structure of the JTA (Joint Technical Architecture). JTA defines the minimum set of elements and standards are important for interoperability. JTA specifies a set of primarily commercial specifications, standards, and guidelines in information processing, information transfer, message development, message format, user interface and security. All standards and guidelines in the JTA must be stable, technically ripened, and publicly available. From that part that goes to the military use and not available to the public is about 15%. JTA core of how to apply information technology to the basic standards and equipment, information processing standards (POSIX, SQL), data transfer standards (TCP / IP, HTTP), the model of functioning of the system, simulation models, user interfaces, and security standards (SSL). Elements in the C4 system, which rely on JTA core, is shown below.

|
| Figure 7.9.2 Architecture of C4 system. |
C4ISR backbone architecture must provide a link to each organizational operating system. There are three main aspects of the functioning of this observation architectures: operational (Operational Architecture - OA), systemic (Systems Architecture - SA) and technical (Technical Architecture - TA). In the latter will recognize all previously enumerated network and computing devices and protocols, from modem to IPv6. This global network for the exchange of information (Global Information Grid - GIG) by architecture was developed to provide 'end-to-end' flow of information with 'warrior' on the ground in the end. Transport information system must have the ability to include secure network environment, allowing DoD users to access, share, and use information in their application, regardless of location, all supported by a strong central network information infrastructure. Of course they are the most effective security mechanisms used are in the process of using information.
The backbone of the GIG is a powerful supercomputer, a cluster of computers and network of clusters (GRID), which in a general sense they form a super-computer. It is strategically important for any country, including our own, to have such a system, which in addition to the military, used for scientific purposes, or simply for economic purposes, among other tasks, the 'deal' as a web search system with support for the Croatian language and datacenter as backbone of institutions. What it was twenty years ago was the internet, and the web ten years ago, today it is a grid, the ability to create super-computers of many networked and unified 'regular' computers or computer clusters, for the purpose of the proposed technology, with the goal of obtaining a large computer power. Thus, the cluster is basically a collection of computers that are centrally managed and unified and that works and is recognized as one entity, and the grid is a set of technologies that allows the joint action of the same entity and different characteristics but not manage them. University Computing Center using grids, namely their cluster computers are actively involved in European projects ALICE and Euro DataGrid. DataGrid initiative launched CERN - European Organization for Nuclear Research, Geneva (Switzerland) with the goal of establishing a large network cluster that could mutually exchange, store and process (distributed processing), large amounts of data within the same scientific experiment and computer applications.
SUMMARY:
Regardless of the characteristics of the military industry, vehicle industry and other specific activities, applications of computers in general computer science is complex and diverse. For efficient use of a computer is necessary to connect to its network system. But the connection between the network system brings additional trouble, allowing malicious 'attacks' on the user's system, data theft, data damage and who knows what else. The worst possible situation for the user that his computer is used as 'Cuckoo egg' for a malicious program to be activated on a certain day, for instance choked traffic of a bank, and notifying the user does not know anything. Training of end users every day there are more imperative. Vast network of computers allows easy 'swelling' data, which requires PROTECTION DATA especially on portable devices and paths.
Hence the increasingly complex process of data processing and application of the results obtained, the computer is of fundamental importance for the whole of society. But there is not one kind of technique that requires so much effort and efforts in process of implementation as a computer, and can not be ignored and not so little funds. It is therefore understandable painstaking way of introducing IT knowledge and technology in education, and other segments of society, even if we're just talking about the information society - the home of users.
Advanced system shown will not use TDMA communication technology than a modern, which will allow higher throughput, more diverse services and greater security. However, the organizational chart will not change significantly compared to the Figure 7.9.1.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |