7.5.2. Wireless communication |
Once upon a time, we used the wireless communications, mainly for military purposes. So when you look at a war film about the Second World War inevitably will remember communication is ended with the word 'OVER'. This meant that the speaker releasing the button to switch modes of submission of the entrance. So device had a transmitter and the receiving part that the mechanical switch alternately joined to the antenna (HALF-DUPLEX). In everyday use the first breakthrough wireless communications to a wireless phone. Casing had a portable phone handset with battery and both were part of the receiving and transmitting device, but the very nature of the wireline telephone channels allowed for simultaneous talk and listen to each of the participants in communication (DUPLEX). Way to achieve simultaneous bidirectional communications over a single pair allows 'phantom line'. But modern wireless communications, have separate receiving and transmitting channels, similar to the receiving and the transmit pair UTP cable (FULL-DUPLEX) and transmission is increasingly used digital signal 'tailored' to the analog sample.
|
|
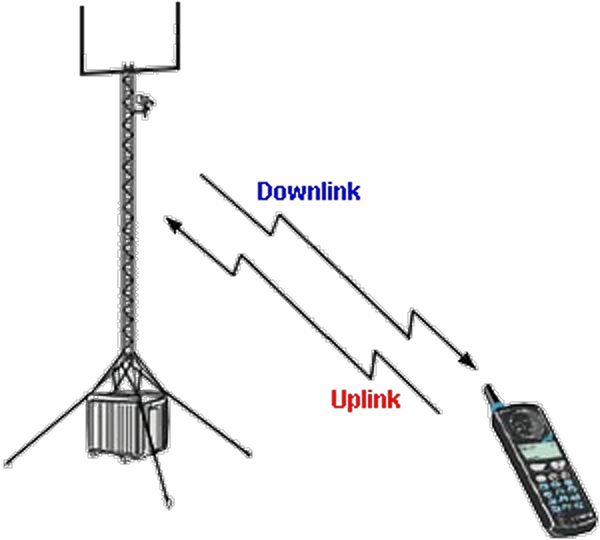
| Figure** 7.5.5 Wireless Communication. ( + / - ) |
The mobile device is more than a good example of this. Central hand-transmitter system located on the roof of a skyscraper enables simultaneous two-way communication with the mobile device and connects a single user in the same way in another remote location with another user. Communication channel has two separate 'subchannels' called UPLINK (from the user to the central antenna) and DOWNLINK (from the central antenna to the client). The communication channel is the frequency range of the high-frequency range that allows it to successfully transmit a signal message. For example, the TV signal requires 6 MHz channel width in the UHF (470 MHz-960 MHz) the numbered 21-69, a total of 48 channels, 48 for signal message. The signal is basically a form of high-frequency sine, modulated with an analog or digital signal, low frequency message. Low-frequency signal message 'imprinted' in the high-frequency signal which has the property of expansion space in some sense 'carry' low frequency signal message, but this is the subject of dealing with telecommunications. There are three basic principles of signal transmission in a communication system.
But mobile telephony is not the subject of this reading. Although terms like 'uplink' and 'downlink' are used to describe the relations linking the master and slave device is active in structured cabling.
Wireless communication in computer systems is very similar mobile telephony on the media that is used to transmit the signal. A common abbreviation for wireless computer network is a WLAN (Wireless Local Area Network), which points to its limited geographical presence in the system of a company or institution, which could not be said for mobile telephony. Not only that, but the offeror can provide telecommunication services and wireless computer communication over channels for mobile phone devices. Wireless computer network basically be seen as a very useful feature in the structure of LAN facilities. A key element that provides connectivity without wires is the classic wireless ACCESS POINT, and a possible version scheduled for installation inside the building displayed in the following figure.

|
|
| Figure 7.5.6 Wireless access point. |
Wireless access points within the facility must be carefully deployed. Each of the devices has a possible area of communication that can not have a circular shape because of obstacles (walls) that interferes with the propagation of electromagnetic waves. Arrangements access point general-purpose notebook for example, must be such that these areas overlap, while the access point that serves a printer that does not matter. That access points will each 'argued' because of overlapping areas in places where it is not desirable well each of them set to work on different operating frequencies - channels and adjust the power of the transmitter to the smallest value. Wireless communication mechanism is basically the opposite Ethernet communication mechanism. Ethernet uses collision detection mechanism signals (CSMA / CD - Carrier Sense Multiple Access / Collision Detect), and WLAN uses a mechanism to avoid the collision. Therefore, devices that access the network will not be competing who will first access the media rather than waiting when the media will be free (CSMA / CA - Carrier-Sense Multiple Access / Collision Avoidance), or waiting for the lack of communication signals (what kind of signal? - water, electric, electromagnetic, light, data, acoustic ...).
By its nature, the dispersion of electromagnetic waves can be channeled so that one part of the 'leak' out the desired area, which makes a big security problem. Safety problem is not just that someone will use the resources of the local network to freely access the Internet, but the fact that it is possible to steal other people's computers, or intentionally destroy them 'Cuckoo egg implant' that will be used to attack other people's resources . Methods of abuse are very diverse and before configuring a single wireless system to scrutinize his documents and examine all possible aspects of the abuse and protect as much as possible and ensure the quality of surveillance. The worst possible solution is unprotected or poorly protected wireless system, which unfortunately has. UTP-STP cable yet it is still the safest communication solution for small businesses and cheapest, if one looks at only the technical aspect. Human factor is still significant, 'no patched' computer operating system due to sheer laziness and irresponsibility of its users view can cause trouble. But it is already subject to SECURITY POLICIES.
For the safety of wireless communications is desirable to use the most advanced encryption mechanism available traffic and provide access only to authorized users. Authorization can be obtained through entering the MAC addresses of devices that access the list of allowed participants to some mechanism or network user login to the system (LDAP, RADIUS), and safety can be further enhanced surveillance hotspots strictly dedicated WLAN Control System (WCS - Wireless Control System) in conjunction with the accompanying its wireless access points, which is able to monitor. But these are a professional and expensive solutions. For a small business or home users enough solution described in the next chapter.
As an access point is essentially a tiny hand-transmitter must have a power source, it is very inconvenient solution to bring the power connector from the 110/220 V AC for his close to him. A better solution is to use dividers that allows us communication cabinets over UTP cable leads DC voltage to an access point that will be able to distinguish the useful signal from the power supply; mechanism Power over Ethernet (PoE). A very good solution is to use the switch that is able to power the access point, but the downside of this solution as the switch and access point must be from the same manufacturer to avoid possible differences in the supply voltage and the allowed energy consumption, which can ultimately be very expensive if this is not taken into account.
The concept of the wireless access point is no peculiarity that is used only for professional purposes. Every household now use some of the ADSL equipment (SOHO), were doing the 'bridge' or 'router' mode, which of the more advanced features it has Wi‑Fi (Wireless Fidelity) wireless communication network based on the IEEE 802.11 wireless protocol. The range of effective communication is achievable within 20-70 meters in diameter is used high-frequency signal of 2.4 GHz, 3.7 GHz or 5 GHz as the holder of a digital message signal, usually using OFDM (Orthogonal Frequency Division Multiplexing) modulation, similar to the DVB standard. Depending on the applied protocol revision (from 'a' to 'n' suffix) is different operating frequency used and the different types and speeds of data transfer (from 1-150 Mbps). SOHO devices usually have multiple Ethernet ports for wired communication and enables seamless communication between the wireless and wired connections.
Wi‑Fi communications uses MAC address as the basis of recognition of the device and can be identified by the fact whether the SOHO device may 'stray' a neighbor device. Access to the device is achieved by logging encrypted WEP (Wired Equivalent Privacy) and / or WPA (Wi‑Fi Protected Access) model. WEP uses 40-bit encryption and WPA nu 128-bit encryption necessary. WPA workflow dynamically changing access keys, and the way to control the error is different. WEP uses CRC (Cyclic Redundancy Check) and a WAP method uses MIC (Message Integrity Code). From the above it is clear that the type of access network safer, although basically every wireless communication potentially certainty 'hole'. How to use Wi‑Fi wireless in Windows XP and Windows 7 operating systems is described in sections 4.4.4 and 4.5.5.
The successor to Wi‑Fi technology, which is characterized by a far greater communication range is WiMax (Worldwide Interoperability for Microwave Access), IEEE 802.16 defined set of protocols. Supports communication speeds around 40 Mbps. The range is similar to mobile devices, depending on the conditions and over 10 km, and uses repeaters similar to them. So very convenient mechanism to communicate with inaccessible or less populated areas. WiMax is sometimes called 'Wi‑Fi on steroids' and can be used for a variety of applications including broadband connections, access points and more. In addition to a variety of services at the same time as Internet access, VoIP and TV (Triple Play Service). Communication antennas and devices are usually slightly larger than a USB stick, integrated into a unified whole is a simple signaling work. User owns the device (Subscriber Unit), which typically uses a USB port to communicate with a computer, a high-frequency signal communicates with the repeater. Uses the frequency range from 10 GHz to 66 GHz and SOFDMA (Scalable Orthogonal Frequency Division Multiple Access) modulation. To allow for simultaneous multi-user access, different high-frequency carrier signals within a single channel. Of course, the computer recognized the device and repeater via its MAC address that is monitored by the ISP (Internet Service Provider).
For small portable devices using the BLUETOOTH type of wireless communication between two or more devices. Unlike Wi‑Fi there is no encryption, and range is very small, up to 10 m, and used high-frequency signal in the range of 2.4 GHz to 2.48 GHz, with a bandwidth of approximately 1-2 Mbps. Most of today's modern computers, cell phones, MP3 players and similar devices have the ability to communicate using bluetooth, thus exclusively PAN networks. Use GFSK (Gaussian Frequency Shift Keying) modulation of the binary code which is a unit of a positive frequency deviation and a binary zero as a negative frequency deviation relative to the frequency of carrier signal, wherein the minimum deviation of 115 kHz. One feature of this technology is a small antenna that usually resembles a memory stick and is usually included in the USB port of your computer. For laptop antenna is incorporated into the base unit and the system is operated by pressing one of the keys to his work and usually indicates the indicator LED that emits blue light.
SUMMARY:
Microwave oven is a device in which the temperature is required to prepare or reheat food by exposure to food irradiation with electromagnetic waves. Transmitter power of about 1000 W inside the oven emits an electromagnetic wave at a frequency of 2450 MHz and causes oscillation of water molecules in the food and thus its heat. Due to the nature of electromagnetic waves that do not pass the metal barriers, food cooking is done in ceramic or plastic bowls (if the final cooking temperature is lower). Food is processed in its own juice with a bit of liquid so that it stays natural flavor, aroma, vitamins and minerals. This is done at a temperature of about 100°C and nothing can be burned, which is suitable especially for the preparation of dietary foods. Unfortunately there is no crispy crust.
Microwave oven is therefore dangerous to humans, and therefore it 'transparent' glass on the door has a metal grid and automatically turns off when the door is accidentally opened. It is not advisable to stand with the microwave oven where the doors are open and invalid or example to put your head in a microwave oven due to colds. Although mobile devices are not working at the specified frequency and its near environment (forbidden), because of this the author of these devices is not a fan of this technology. Especially not 'mobile' - do not use neither possesses mobile :-). But if the military applications are concerned, there is no problem, as the man in the war, ordinary soldier, is an significant factor?
To end an unusual comparison: Men are like BLUETOOTH - is associated with a partner while in the vicinity, but as soon as it there is no search for other devices. Women are like Wi‑Fi - see all available, but she is connected only with the strongest partner.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |