Users of the System |
Each user on the system has a user account. The account is basically the name with which the user logs in to the system and also the name of his initial corresponding folder where your data is in the form of various folders and files, and user login to the system and its associated contents are protected by password. Folder (directory, map) of all users are located in the [Documents and Settings], in which according to the above are the following directories and files:
Each of these folders has its subfolders and files that describe each of these users. How does that protect all data from the user, if they are not relocated outside the disc with the operating system, the amount of data in them can grow enormously because of the temporary files Internet Explorer, mailbox with a multitude of attachments, cookies and various types of temporary files that are hidden in a happy subfolder [Local Settings] that every user. Thus there remain a multitude of useless records created during installation of software or to work with. ZIP files and similar programs [Temp] subfolders in the [Local Settings] to use anything and use anything not automatically deleted. Hygiene computers, especially if it uses more than one user, it is not easy to implement, and even harder to restore the system in proper condition, if for some reason the damage. The vast amount of data collected during the operation of the user folders and difficulty of recovery in the event of damage, one of the reasons why a significant and most used folders user moves to another partition.
For one user-generated binds its IDentifier (ID) number that does not change regardless of whether it has changed the name of the user. If the user changes the name, basically creating a new 'nickname' for an existing user name and a name for the folder in the [Documents and Settings] remains the same. As already stated, the folders and files 'dislike' graphemes of the locality in names, and therefore not good that the user name that is specified in the installation procedure contains graphemes of locality.
addition to the above 'user' and there are people who do not have their own folders, which are defined in the {Start}-{Control Panel}-{Administrative Tools}-{Computer Management}-{Local Users and Groups}-{Users}. It will show all users that are created through an option in the {Local Users and Groups}-{Groups} can assign powers / rights on the system by placing them in one of the groups:
With each of these groups was accompanied by a description of the rights exercised on the system. In addition to already existing groups can be created and a new group. Regarding the rights of the users, it is not good that the system there is at least one user, who is not disabled and who has administrator privileges, because then some system tasks impossible. To abolish the administrative rights to all active users, no rights, no one who can make some systemic changes, and no way back. The situation reminds of the situation when she leaves the house without a key, and lock the door locks automatically. So now enter :-). Thus, one should be very cautious about termination the rights of individual users. Unfamiliar user is not advisable to give administrator privileges.
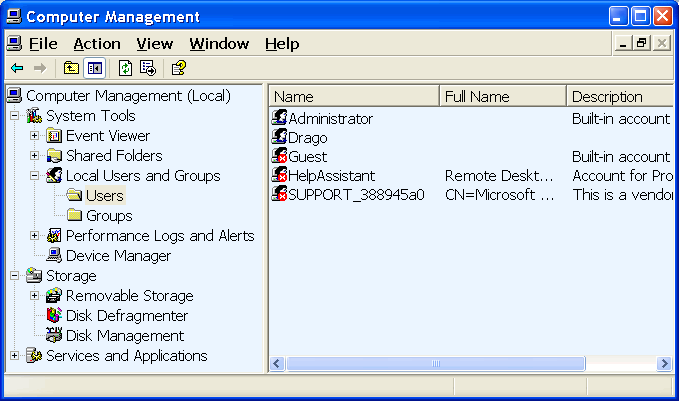
|
| Figure* 4.4.10 System users and their groups. ( + / - ) |
Users of the previous Figure :
Installation of software in this group may experience a few more specific user. If on the other hand use a combination of the <CTRL> + <ALT> + <DEL> in 'Windows Task Manager', in choosing ||Processes||, will appear with the current USER (Drago, for example) and the user SYSTEM, LOCAL SERVICE and NETWORK SERVICE. Thus it can be seen by anyone who start a service or process is responsible.
In addition to the above each of the users can change group membership, which is shown in Figure 4.4.10b. Group 'Administrators' has the greatest authority, or rather all the powers over the system, while others have limitations in terms of function. Possible through the settings of the policy to determine some other profile. When creating a user in the default installation process all defined users administrator group members, and subsequently placed in a desired group. This is done in a way to highlight the desired user and L1 D1 action and selecting {Properties} we get a window that has a card ||Member of|| which allows the user to change the group to which it belongs. Of course, if the user himself revoke administrative rights over them can not be returned except by another user who is a member of the Administrators group.
A quick way to restrict the new user does not have administrative rights to the L1 actions of users on the icon in the starting menu, 'Bob Dalton' as shown in Figure 4.4.5, and the offered window is selected |Cancel|, and on request what he wants to do with the user account should be chosen 'Change my account type' and we get the next image.
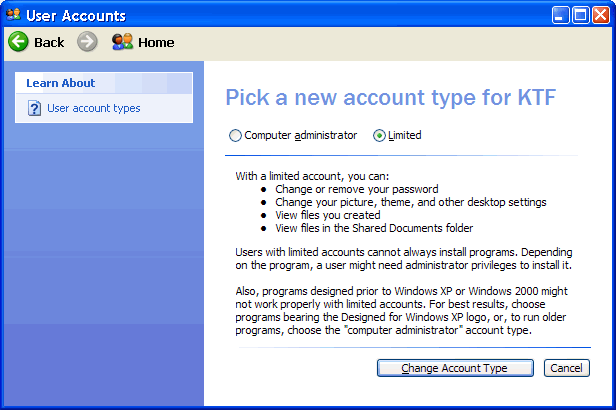
|
| Figure 4.4.11 Speed limit of users rights. |
When you select Options |Limited| opens the possibility |Change Account Type|, and if the same triggers a multitude of user loses the right to work in the system, change the IP address or a particular type of software installation, for example, and only he can change the administrator rights. To be mentioned are implemented must be activated at least two users, in addition to users 'administrator', and a user with administrator rights can reduce the powers of another user. Thus, users 'Daddy' has administrator rights, and the 'kids' and 'mom' have diminished rights granted to the previous Figure award a 'Daddy'. Very useful in terms of keeping the nerves regarding maintenance. Above operation is not the only thing you can do on the system. Pedantic Admin user will use additional tools such as GPEDIT.MSC. MSC tools are a subset of the MMC (Microsoft Management Console) program support.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |