4.4.2. Structure of OS (Folders and Files) |
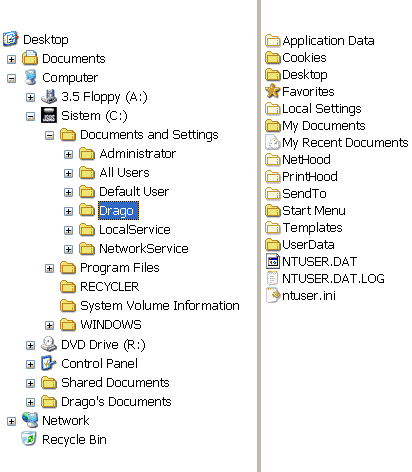
Noun (logical) structure of the Windows XP operating system by installing the following picture appears. Because everything starts with a drive letter and expands as the tree top leaves of each branch represents one path or folder-directory, a leaf of of branches are files in the folder, it is often used to display the name - TREE of OS. The tree, as displayed by Windows Explorer ga consists of four basic elements:
Desktop + Documents + Computer + Network Recycle bin |
DESKTOP (working screen) displays icons that are used on the desktop, NETWORK application includes the 'My Web Sites on MSN', and RECYCLE BIN is a bucket that contains deleted documents with action D1-Restore can return to their corresponding folder. Basically emptying no possibility of recovery of deleted documents. Elements in the preceding list have the ' + ' mark may be further branched into view as shown in the next picture.
|
| Figure** 4.4.7 File and Folders of Windows XP OS. ( + / - ) |
Bin is listed in a different file manager sees as a folder called [Recycler] as shown in Figure 4.4.7c. Figure shows the contents of the media in the device '[R:]' (DVD-RW) and the contents of the hard disk '[C:]'. Although the media data backup disk image is not the same. At no optical media map [Recycler] and [System Volume Information]. Folder on the disk are marked with an inscription <FOLDER>, and optical media have a size as files. The reason is the nature of the file system. Drive using NTFS (New Technology File System) is a software for writing data to optical media using the UDF (Universal Disk Format), which has the characteristics of the file folder. In the Windows XP operating system support for UDF file system is not supported by default, but it is supported by the client software to store data on optical media (Nero, Roxio ...) and made available to the entire operating system. The UDF file system is UNIX based and more about it in Chapter 5. For users of the most important folder [Documents and Settings]. How in the [Documents and Settings] has more users, created by 'the system', it is logical that neither the composition of preloaded data in registers editor is going to be the same. Users of the system and their associated folders are:
Created user (in this example Drago) and Administrator have the same folder structure as shown right sides. Folders and files hidden lighter color than the usual running, if otherwise provided in Figure 4.4.7b shows (Show hidden files and folders).
Map [Application Data] contains all the settings of software that a user can set according to your preferences, which means that the contents of this folder is not the same for each user. Common elements of program support all users are in the folder of the same name but with users [All Users]. What is not listed on the two maps recorded in the register, and a part of the file NTUSER.DAT visible in the previous picture. Map [Cookies] contains cookies that are created when you visit a web content such as seeking authorization, but it is possible that the same set and a 'bad' site in a completely different purpose. It is useful to this folder from time to time to check and delete cookies if that remained after deleting from IE (Internet Explorer) program support.
Map [Desktop] contains desktop icons. How common icons for all users are in the same named folder but the user [All Users], in a folder the user will not be all the icons that are on the desktop. Poorly defined installation of software (SETUP installation procedure some applications) can set the same icon in the folder of the user and shared folder, so it will not overlap although at first glance does not see. Same goes for the [Start Menu], which is nothing for a long time to display presented in Figure 4.4.5b folder where the shortcut to the appropriate program support. If the contents of these folders overlap, slowing the work with the user interface and is well after installation to check this folder there are no duplicate records.
With pictures 4.4.8b can be argued that at [D:] drive is a virtual memory file PAGEFILE.SYS, which is basically located on the second physical disk in the initial sectors. In this way the system is designed to work with two separate disks (no RAID arrays) to speed up the work when the operating system requirements to virtual memory frequent. The principle is that this file is in size two times larger than the physical presence of memory, but it does not have to be strictly observed if there is enough RAM. Additionally it is good to declare this file fixed in size so as not to change during operation the size and position on the disk and thereby prevent its fragmentation. If the operating system tasks automatically adjust the size of the file and its automatic deletion when you shut down your computer, the next time you turn your computer will create a new file that will certainly change the size and set it on another free disk space and can not be in one piece '. Linux servers, for example, be configured so that the virtual memory size is fixed by a separate disk partition to ensure good performance of the system. Fixing pagefile.sys file size and place it at the beginning of any disk partition allows better system performance if the balance between physical and virtual memory well estimated.
Map [Favorites] contains icons entered the URL addresses used by IE, map [SendTo] contains shortcuts used the menu that appears by D1 action on a folder or file, and if all desired no shortcuts should be placed here. The folder in which the intervention is beneficial [Local Settings], which among other things contains the [Temp] and [Temporary Internet Files] that can eventually filled with everything. Size of the [Temporary Internet Files] may be limited in the settings of IE, but map [Temp] is not to limit the content and is not emptied automatically. This author has moved this folder to another partition, and the [\Windows\Temp], [My Documents] and several others. Small 'batch' file runs at startup and deletes blank and true TEMP directories.
@echo off
RMDIR /S /Q F:\TEMP
MKDIR F:\TEMP
C:
cd \windows\temp
del /F /Q /S *.*
The file is not 'required by law and regulation' because should contain the ' IF ' elements to test that the specified directory or not, because if the content is not found, the option ' /F ' can begin to remove all of them in the root directory of the system. If it hits the nominal structure as shown in the previous Figure in the 'Command Prompt' window, then the list of files, with the key ' /x ' keys ' /ahs /x ' in the command to print the contents looks like this:
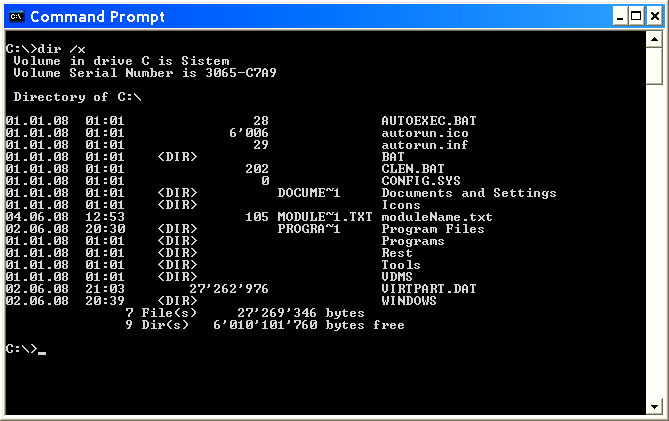
|
| Figure* 4.4.8 Tree of Windows XP OS in the 'command' window. ( + / - ) |
By the command window comes up through the START menu or by entering the command CMD in the form shown in Figure 4.4.5. The list shows that the system uses short names for files and directories under the system of 8 characters for the name and 3 characters for the type (8+3) as it uses the MS DOS operating system, which joins the long term. If you look at the composition of the directory [\Windows\system32\] can be observed that all the key files have no more than 8 characters as the key directories. So how does Windows XP do not rely on short file names, short names are indeed the foundation of their functioning.
Basic from Windows XP according to previous figures are directories:
Other files and directories are shown in the image are part of the subsequently installed software. Files that can not immediately see are the system and hidden files that is shown in Figure 4.4.8b. To this group belong to the following directories and files:
The first 512 bytes of hard disk data are entered in the disk is partitioned and address on the disk where the BOOT_LOADER, the initial program to run the operating system, which examines the partition table and asks for a bootable partition that is marked as active (mark-flag ' A '). When you find a BOOT mark active partition then the first sector of the active partition - boot sector, copied to the working memory where it is exercised. So, one partition must be marked as active. From the BOOT SECTOR of a retrieved NTLDR file that is responsible for loading the operating system kernel and run the entire operating system. NTLDR invokes to execute NTDETECT.COM file that identifies the basic units of the system and the information returned NTLDR. These data block is called the Master Boot Record (MBR), and if the records are lost, damaged all data. MBR is independent of the operating system, and the BOOT SECTOR of the active partition depends on the operating system and the file system. MBR records was first pronounced by the initial software (BOOTSTRAP) written in the BIOS.
If the Windows XP operating system can not run it, and follow the message 'DISK BOOT FAILURE, INSERT SYSTEM DISK AND PRESS ENTER', the reason may be due to a damaged BOOT SECTOR, or the NTLDR and NTDETECT.COM files. Replacement of damaged NTLDR and NTDETECT.COM files is done by being copied correctly with the Windows XP installation CD COPY command (from [CD_drive:\ i386] directory) to 'Recovery Console' mode, select ' R ' from the options available when running Windows XP installation CD when you start your computer, and command FIXBOOT fixes BOOT SECTOR. Damaged BOOT.INI file will automatically be repaired. If the above does not help following installing Windows XP from scratch. If the installation option is selected through the pre-installed Windows XP system will keep all installed.
If the disk partition is formatted in the NTFS file system, it is possible to file action D1 add another sort of properties as opposed to the FAT file system. XP has the good qualities that the file type .EXE can be declared as Windows 9X, NT or 2K compatible. Namely XP is a 32 bit operating system, which basically means to run 16-bit applications. But if you can not run, the file is declared compatible for the appropriate operating system and will be able to execute.
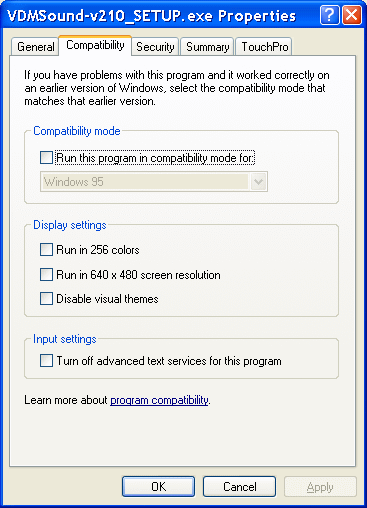
|
|
|
| |
| Figure** 4.4.9 Characteristics of folders and files. ( + / - ) |
Other views these pictures describe some additional features. Besides the aforementioned NTFS allows to determine the ownership of the files through the card ||security|| where is offered to determine what each user can and if it is a complement to the properties directory folders, it can be made available to other participants via the network card ||Shraing|| and where through elections |Permissions| comes to the part that allows the grant of a folder (onClick on the image 4.4.9). It is not good to give such rights to the folder can be accessed by each participant in the network (even if the Internet is a public network). Someone may be used as a warehouse. It's better to predict which users are allowed to access the folder and give them related rights. If the user has not created a system to do that.
Of course, there is the definition and attributes known from DOS: ' Read-only ' and ' Hidden '.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |