7.4. INTERNET |
Organizations around the world are forced daily to acquire new knowledge in order to perform their job well and successfully. Besides many other knowledge from different areas you need them, and technical knowledge in the field of new technologies. This area is very wide and includes a number of segments among which it stands out as one of the most important.
It is not superfluous to clarify the difference between three seemingly similar terms: internet, Internet i Ethernet.
The forerunner of the Internet is the ARPANET (Advanced Research Projects Agency NETwork) - Network project of the Ministry of Defense of the U.S. from the 60's for the military. Then the network connected computers becomes the plaything of scientists. 1991st was introduced Gopher service developed in the laboratories of the University of Minnesota (U.S.), which has greatly facilitated the use of the Internet. According to the ideas of Tim Berners-Lee 1993rd the first version is designed to present the WWW in The European Laboratory for Particle Physics in Switzerland (CERN) and the first graphically oriented browser - MOSAIC. Then launch NETSCAPE 1994. year, and INTERNET EXPLORERA in 1995. year and a new high-speed network architecture arise based Internet as we know it today.
Internet today represents millions of computers around the world connected in a single network in which the range of services are available. The Internet is not owned by any one company alone, but represents an open computer network, every day more and more. The idea of the Internet has stemmed from the design of local computer networks in businesses that have enabled sharing of computing resources and sharing of files and mail within the company or the provision of other services. This principle is easily extended to the whole world. So, it is based on a vast number of networked local systems for different purposes and sizes, interconnected like a huge spider web; and from the destination to the target can be reached via various routes. Indeed, even individual pieces of data - 'PACKAGES', in which the data are analyzed with regard to the source distribution along the network paths to the destination can be reached by various ways although some 'packages' an integral part of the same data as a unified whole. Vividly, as if the source of candy out of the box and individually transported to a destination, where each of them will be transported along the same or different path, but ultimately the destination we all gather and properly stacked to the contents of the box at the destination fully completed.
Speed of the Internet is growing day by day. With a dozen former kbps today in the developed countries of the world communication takes place in a 10 Mbps or more. Enormous effort has been made in the further development of the network infrastructure, and in particular the direction of security and increase the speed of communication, because it is realized enormous power of the Internet with regard to the overall development of society. Local area network (LAN) institutions today are already designed with an internal speed of 10 Gbps between key network devices that make up the BACKBONE of local network.
Ethernet is a response to the demand for fast LAN. Ethernet protocol accepts with the same speed of 3 Mbps in 1973. year and 10 Gbps today. Basically it is a multi-user access to the common medium of CSNA / CD principles. Ethernet specifications support different media, different throughput (bandwidth - BW) and different variants of hardware compared to the first and second layer of the OSI model. Ethernet standard is published in 1980. The consortium DIX (Digital, Intel, Xerox) implemented Ethernet as an open standard, or standard that does not require application for license rights. Published by the IEEE standard in 1985. year as local area networks called 802.3, which is basically the Ethernet standard with only minor differences. Although the original standard changed several times due to faster access to media compatibility is maintained between all the published version. Success Ethernet enable the following:
|
Definition of the Internet
A profusion of different definitions of the internet; 'network of networks', 'global network' and similar. The internet is a global network of computers of all kinds, which deliberately and logically combines thousands of different computer networks around the world that use the same technical standards in order to achieve mutual communication, and enable the use of a variety of different services, which puts this unique network in information system. If a home computer or local network, connect to the modem over a telephone line (or optical cable) to the internet provider, and through him to the 'global network', it becomes part of the internet.
There is no central authority that governs the internet. Participation in the work of the internet is based on the free and cooperative basis with the obligation to respect the technical standards in order to achieve a presence on the network. Internet company in Fairfax, Virginia, U.S., has an important role and recommends technical standards. This organization creates a relationship between the official government institutions in some countries and non-governmental institutions such as universities and companies.
Number of Internet users is growing continuously, but most experts agree that it would be a figure of around 500 million users during this decade. However, diverse applications, especially in the business world (banks, transport companies, etc.), leading to the unauthorized intrusion into computer systems in the various purposes or blocking their work, it becomes less and less nice environment. Security and privacy are all important aspects that must be considered when designing a network, especially local ones. Number of causes can lead to the unavailability or loss of information in electronic form: from natural disaster, equipment failure, errors in system support, to human actions. The human factor can act inside or outside, and the damage can be caused accidentally or intentionally. Especially today, we have witnessed many 'viruses', 'worms', huge amounts of advertising and other useless e-mail (spam), theft of software, music and movies and the like.
Even institutions or companies that believe that their systems do not contain valuable information concerns and additional investments are required to worry about the security of their computers would not be a launching pad for attacks on other people's systems. Let's block the bank's services overloading their resources using the resources of many other people's computers simultaneously, and that the owners of these computer nothing about it because they know their own ignorance and lack of protection. As soon as the computer is connected to the Internet ceases to be somebody's 'private' property and its user must take care of all aspects of security provided. Increasingly seeks regulate behavior on the Internet and allow prosecution of offenders, regardless of national boundaries.
Because of all that needs to be organized to prepare in case of incidents. Therefore, in the institutions and companies provides SECURITY POLICY, or acceptable USE POLICY which must respect all those who are connected to its computer network resources. Security policy in the business world are extremely restrictive, everything is prohibited except that which is explicitly allowed, permitted only what is necessary to do the job. Document that describes this policy will contain everything necessary to prevent incidents: the ways in which one can learn from such new administrative building, registration of entry and exit, handling of confidential information and documents to the way physical and software security, computer equipment or the entire local network. Description of policy implementation provides procedures for 'ordinary' people and the staff is required to monitor and performs. The key point in carrying out the security policy is that at any moment she knows exactly whose job it is and who is responsible for what.
Factors affecting the rapid growth of Internet users are:
After all this it can be defined as a global planetary communication system of interconnected computer networks for the exchange of information of all types.
Each state has its own Internet network solution on the principle of interconnected local area networks LAN (Local Area Network). So commonly associated local network branded WAN (Wide Area Network) as a term for computer network systems that include a larger geographic area. Usually the existence of several WANs different in purpose and mission. CARNet is one of WANs on Croatian territory intended to educational institutions.
Internet in Croatia
CARNet networks is a private WAN Croatian academic and research community. Network infrastructure has CARNet institutions, and copper and fiber connections are leased from the Croatian telecommunications or the act of self development. Ministry of Science and Technology was established by the Croatian CARNet as an institution where the activity is the development, construction, and maintenance and monitoring of the network which is the principle of cohesion in the first years of operation shown in the following figure.
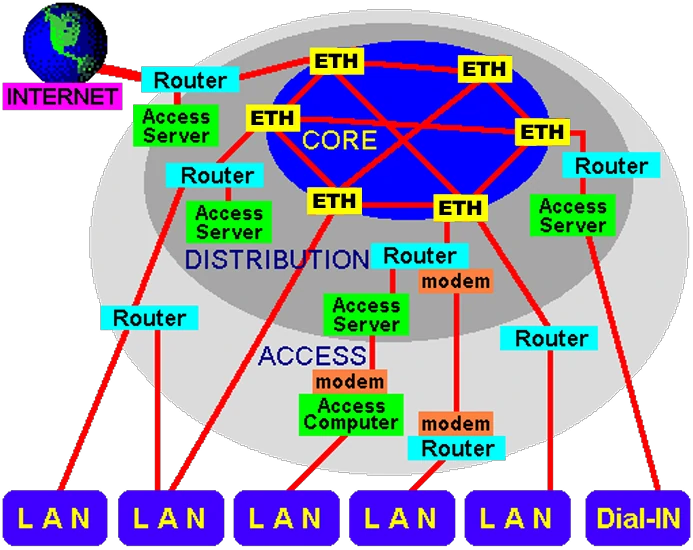
|
| Figure 7.4.1 Logical realization of Internet (CARNet) in Croatia 90'. |
TCP / IP is the dominant protocol in the network CARNet. Transmission technologies as ATM (Asynchronous Transfer Mode) and Ethernet, and serial links modems on leased lines. Except for the transmission of IP traffic over an ATM network technology is also used in applications such as video network designed for real-time transmission of remote lectures and tone of the television picture quality.
The core of the original WAN system of CARNet network are based on ATM technology. Transmission speeds within the core are 155 Mbps and 622 Mbps. Foldable network is implemented with ATM switches are physically connected via optical and wired cable. At the core of CARNet WAN are connected to distribution nodes. ATM switches are also the core ATM switches at distribution nodes. Specifically, part of the input ATM switches designed for the core, and part of the distribution nodes. At each node connected to the distribution of one or more access nodes. Access nodes are places access to LAN facilities CARNet WAN
The initial implementation of CARNet core covers the whole of Croatia connections to a main junction in Zagreb, with more than 100 institutions and the number of members in the regional nodes of up to several dozens of institutions, basically each with own local area network. The network is daily increasing, improving and upgrading, and the use of new technologies for core speeds up to 100 Gbps.
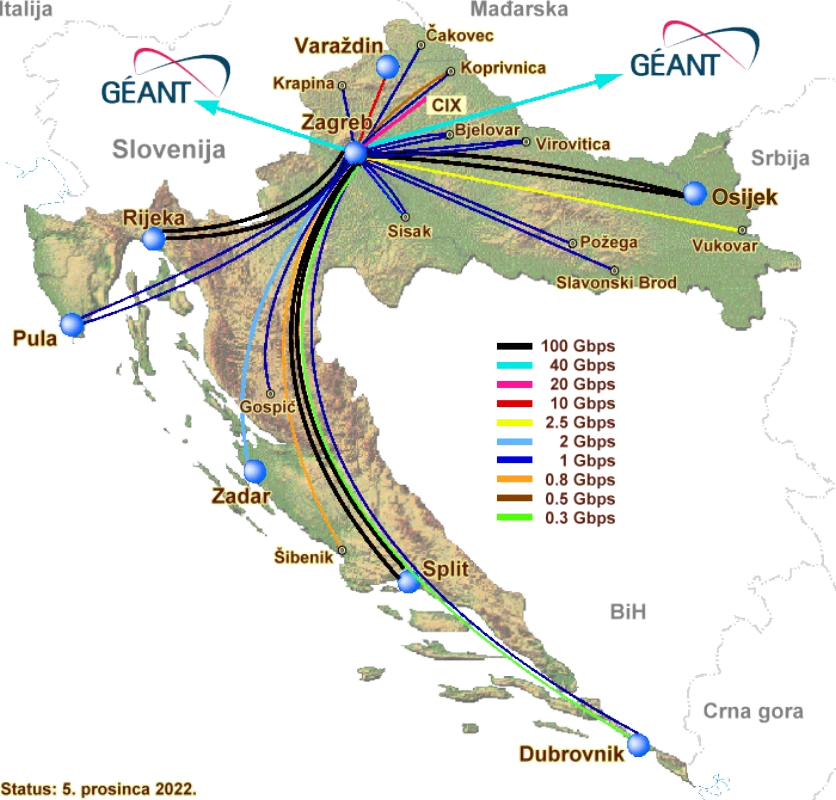
|
| Figure 7.4.2 Physical realization of the Internet (CARNet) in Croatia. |
For most of its users CARNet is modern computing and communications infrastructure, computer network that connects all Croatian universities and most university cities via a fast core of 1 Gbps and 100 Gbps. CARNet provides technical support and advisory assistance to member institutions. CARNet acts Croatia DNS service, responsible for editing and approval within the domain 'hr' national domain and CERT, a group for issues of computer security and computer networks.
From the smallest places in one country it is possible to communicate in seconds with a person who is in the completely opposite end of the planet. It is important to point out that this is a well-organized system based on high-quality technical standards continue to advance and complement the new capabilities.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |