3.6.2. Protocols - OSI Model |
Thoughtfully designed procedures that follow are called data exchange protocols. The protocol is implemented in terms of the process to be performed in order to preserve the integrity of the data. Each process is carried out on one of the layers of the protocol listed in Table 3.6.6.

|
| Figure 3.6.5 Frame protocol messages processed. |
Simplified; according to Figure 3.6.5, first the data is collected (level 1), with regard to forwarding faster transfer compressed, are added bits to control errors and the way (process) data compression and error control is described in the header 1 (level 2), then the data is grouped into groups (blocks) and marks the beginning and end of each group of data or more than one group, the procedure is described in the header 2 (level 3) which were added to the data about the sender and the recipient, and so on until the physical transfer a set of blocks of data over telecommunications lines in the form of electrical, electromagnetic or optical signals and ways to display information to the user (recipient). The structure of the message, wrapped headers as shown in the previous Figure, called the RAM protocol. Procedure accruing some header data is called ENCAPSULATION and individuality is the preparation of data for submission. Separation of individual headers in the proceedings before the name of the DECAPSULATION.
Thus, the messages when transmitting and receiving grouped into a sequence of data blocks, each of which is organized as a logical unit called 'FRAME' data in a network environment that would be a Token Ring (IEEE 802.5) and Ethernet (IEEE 802.3). The beginning and end of the frame is marked with a special combination of bits. Bits inside the frame are organized into fields that begin at the exact position inside the frame, and they are:
|
Control field contains the error control data sum (Cyclic Redundancy Checksum - CRC) before sending and if the receipt of the data finds a discrepancy in the sum of the received data with the sum written in transmitting required to resend the block. There are different methods of control to the error, and given the very commonly used.
All this is described in the form of documentation as part of the one laid down by the relevant organizations (e.g. ISO, DIN), or as recommended by the competent international organizations (e.g. CCITT), and can be recognized by the added names like HDLC (High Level Data Link Control) prescribed by ISO, CCITT recommendation X.25, IPX (Internet protocol) and TCP / IP (Transmission Control protocol / Internet Protocol) as part of the protocol relating to the network, etc.
The International Standards Organization (ISO - International Organization for Standardization) 1978th The standard is defined by the 7 levels (layers) to connect computers in a network called the OSI (Open System Interconnection) REFERENCE MODEL, where the level shown in Table 3.6.6. OSI model essentially describes how to manage the data during different stages of their transmission. Each layer provides services to the layer directly above it.
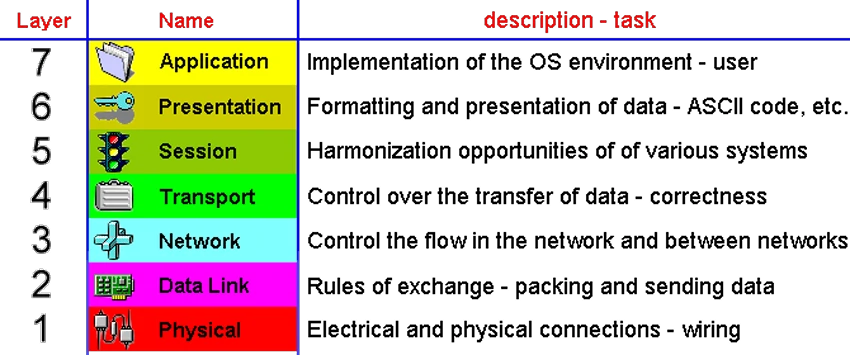
|
| Figure 3.6.6 Layers of the OSI network model established by ISO. |
Brief description of the individual layers is briefly described:
Why even layers? The purpose of it is true separation of specific functions in networking in a way that one layer has no effect on the adjacent. This has enabled the development of their individual components and changes in the device (computer) without affecting its functionality. For example, replacement of faulty network card will only require re-entry of a few parameters regardless of which manufacturer is a new program to read mail will work together in spite of the different manufacturers and more. So will the networks from different vendors to communicate with each other seamlessly.
Of course, the standard time updates and improves in line with technological development, communications and networks. This principled solution (model) which adhere to all manufacturers of network software and hardware support, although the names of the levels are often as different as shown in Table 3.6.7.
Relationship between different platforms and often implemented by manufacturers, and thus has developed NetWare TCP / IP support, which can be integrated into their system, or it is realized via special protocol to connect.

|
| Table 3.6.7 Layers of different platforms according to OSI model. |
The top three layers define how the exchange and processing of data in the network domain, and the next four layers are related to the processing of data in the user domain. As you can see from the picture the different communication platforms addressed in different ways. OSI model does not define specific standards and can not be viewed as a standard but as a recommended reference model. Abbreviations in some layers of the OSI model are L1 (layer 1), L2, L3, L4, L5, L6 and L7 according to figures in Figure 3.6.7. If a device says it is working on layer L3 default is to know the process and previous.
Example I
Principles of TCP / IP (Transmission Control Protocol / Internet Protocol) protocol stack.
It is a set of protocols that underpin the modern world of the Internet, intended for communication between computers connected in heterogeneous networks based on the connectivity node to node.
IP layer has the task of transferring data packets between network nodes without any acknowledgment, until the TCP layer by layer service IP achieves reliable connections with permanent connections between network nodes by performing constant communication between them and check them. The principle of communication on the TCP / IP model is graphically explained in Chapter 7.4.3.
Most important from this set of network protocols are:
|
Each node (computer) on the Internet has a unique IP address with 4 numbers separated by dots per template:
255.255.255.255
Of course, it is a 32 bit binary number that describes a convenience to decade. These are two groups of digits: the first group is related to the local network (for example 172.30.×××.××× or 192 168 255.×××) a group that follows the computer on the network (×××=1-254). These examples indicate that the number of networks and the number of computers in the network is not the same. Public class defines the network A, B, C, D, E, and a private class A, B, C according to the ISO (International Standards Organization), instructions, and, according to these two addresses of computers can be:
172.30.1.3 or 192.168.255.3
The class D and E are used for special purposes. If the ×××=0 it is the network address, if ×××>0, it is the address of the computer, and if the ×××=255 it is the network address masks or advertising. Computer 172.30.1.3 on the network 172.30.0.0. A network of more classes in Chapter 7.4.4. As such impractical for memory addresses were introduced special servers where each node in the local access network assigns a comprehensible name as:
marjan.spalato.hr
The terms in the title are separated by a period. The first term refers to the name of the computer, the other to his group affiliation (domain) and third in the state in which they are located (main domain). In fact, the number and the name refers to the same computer. But communication does not take place via the computer name and domain than its IP address, which means that the names should be translated. This is a system for caring hierarchical DNS (Domain Name Server) worldwide. It is special to the Name Service server that provides translation services of computers in his name, and vice versa - the symbolic addressing.
In order to define a group of computers belonging to the same local network, introduced the concept of a network mask (Subnet Mask). For local area network lowest level (C-class) specifies the mask:
255.255.255.0
which means that the previous example, all the computers that belong to the domain of 'spalato' be numbered 192.168.255.X, where X is a numerical value of 0-255 numbers except 0, 128 and 255, which have a special purpose, a total of up to 253 computing devices within the local network. IP addresses can be assigned to hubs, switches, routers and other network devices that you have.
So, basically the domain 'spalato.hr' (192.168.255.×××) can have 253 computers in the local network. It is also the lowest class of IP addressing, the C-class.
If the network mask types:
255.255.0.0
the network, defined in this way it is possible to define domains 65'534 computers and computing devices. So CARNet has specified mask with numbers 161.53.X.X, while T-Com has the same mask but with numbers 205.219.X.X. Such a class of IP addressing is called the B-class. They have the most Internet service providers (ISP).
Mask type 255.0.0.0, A-class, belongs particular purposes and very large companies, and is not present in Croatia.
SUMMARY:
A set of rules that prescribe the correct course of action of a system called the PROTOCOL. In the computer world these are the rules that define how smoothly transfer data between two computers (nodes) in the network.
The protocol defines the communication procedures, linking, synchronization, verification and transfer of data between processes on the same computer or on computers connected to the computer network. Besides, from the viewpoint of a supervisor defines sharing disks between computers network, printer sharing, e-mail, distribute news and other services.
As the number of Internet users increased significantly in recent years expressed a growing lack of available IP addresses. The project of the new generation of Internet protocol called IPng and IPv6, which has a number of enhancements provides 128 bits necessary IP address. Is it necessary to introduce IPv6 in all communications. In fact it is not, for example, to the SOHO devices will use IPv6 towards ISP, and SOHO device in its internal network to use IPv4.
Until his recent deployment is possible to use multiple solutions one of which is the dynamic change of IP addresses (DHCP - Dynamic Host Configuration Protocol) when the user each time re-connects to the network gets the first available IP address and the computer he has no permanent address defined in the list on the server or some of the methods of organizing sub-networks within the same local area network. DHCP is based on the assumption that not all computers in the network continuously work, and one is enough to satisfy the average number of network access. In the case of the utilization of all addresses in the range defined newly declared computer will be able to connect to the network only when connected to one of the existing check-out.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |