4.6.3. Security, VPN, Proxy |
At the time of the MAINFRAME computers that featured a closed system with the accompanying equipment, security was largely based on physical protection from data theft. It was at the time before PC computers and the Internet appeared. Portable media on a PC (floppy disk, USB Stick ...) and computer networks connected to the global computer network, when they have realized conditions for the 'exchange' of various data and programs between users through targeted written malware called - VIRUS, which of course works without knowledge of the user.
Viruses are programs that self-replicate recursively, meaning that infected systems spread the virus to other systems, which then propagate the virus further. While many viruses contain a destructive payload, it's quite common for viruses to do nothing more than spread from one system to another. That is a type of malicious software - MALWARE, which when is executed, replicates by reproducing itself or infecting other computer programs by modifying them. MALWARE encompasses all forms of malicious software, such as worms, ransomware, trojan horses, keyloggers, rootkits, spyware, adware, and other malicious software.
Basically computer virus consists of three parts:
Today, anti-virus software solutions have been greatly advanced, so the user does not even have to think about it. Of course, quality programs has to be paid. Windows 10 has incorporated in program support 'Windows Defender', sufficient for an ordinary (casual) users, which is constantly improved and enhanced in order to be as efficient as possible.
Well, in old ages there was one very nasty - RIPPER. Ripper is similar to most Boot Sector (MBR) viruses, it is located in MBR, and infecting with one major exception, it does not store a copy of the original partition sector elsewhere on the disk. The user may experience problems running programs requiring upper memory, and difficulty accessing disk drives. Once the virus is executed, it will infect the hard drive's MBR and may become memory resident. With every subsequent boot, the virus will be loaded into memory and will attempt to infect floppy diskettes accessed by the computer. It would make such a mess that without backups you could not rescue anything.
Viruses were written by hackers with different intentions. I remember the computer hack tool, named BEAST, for which the source code could buy for $ 1000. Serve is to take control of the computer (RAT - Remote Admin Tool) so hacker could make anything on the computer. Today, the primary goal is to get data (bank accounts, passwords, card numbers ...) to make money, or deny a server's resources by DOS attack (Deny Off Service) for some purpose. Exactly because of that the concept of security has been extended thanks to technological achievements, but also the prescribed way of using computers.
Today, your Internet Provider, Government and hackers can track your internet activity without any problems! Therefore hide your IP address and LOCATION with a VPN. Aditionaly, use all available tools to protect your computer, respectively data on its disks. The most important things which today can be used to protect the computer is described and further items.
BitLocker - Logical volume encryption system. Full disk encryption feature included with Windows Vista and later versions of this OS. It is designed to protect data by providing encryption for entire volumes. There are three authentication mechanisms that can be used as building blocks to implement BitLocker encryption:
|

Figure 4.6.84 TPM modul. |
BitLocker Drive Encryption is a data protection feature of Windows 10 that integrates with the operating system and addresses the threats of data theft or exposure from lost, stolen, or inappropriately decommissioned computers. BitLocker provides the most protection when used with a Trusted Platform Module (TPM) version 1.2 or later, and offers acceptable level of security.
VPN - Virtual Private Network is the name for computer networks that connect to each other using public network infrastructure, but use special communication protocols that allow content encryption. It can be understood as a protected tunnel through existing joining paths. They therefore allow network users to be safe from interception or 'incursion', intentionally or inhumanly, by other non-network users. The most common protocols used are:
That is the first part of security at data exchange.
OpenDNS - Mehanism to prevent a DNS leak refers to a security flaw that allows the true IP address of a connection to be revealed to websites, despite the use of a VPN service to conceal it. ISP settings, which content your IPV/4 SOHO settings and DNS of your ISP is shown as example at Figure 4.6.12. All what must be change is DNS source, so replace settings of ISP DNS with:
|
|
That is all!
NetSetMan - This program support is recommended at first page of Windows 10 OS. Now there is shown some possibilities how to quickly change NIC settings.
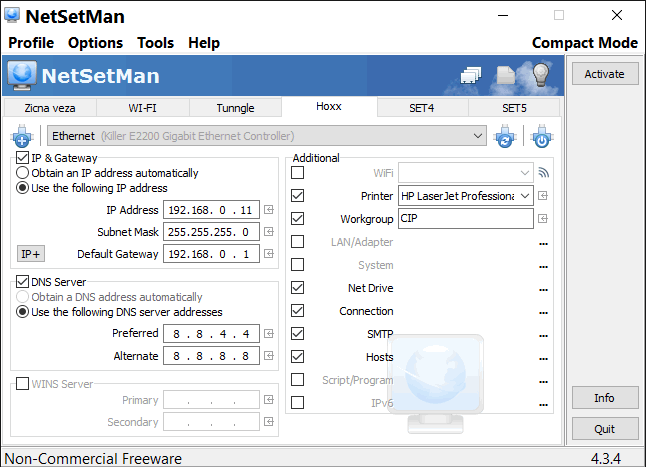
|
| Figure 4.6.85 Settings of NIC. |
Combination can be different than shown. This software is exactly what is need to work with next service.
Hoxx VPN Service - Bypass Internet Censorship & Access Blocked Websites using these 'Free Browser VPN addon' with no bandwidth restrictions. Use of this VPN service to unblock geo- or government blocked websites such as Netflix, Spofity, Hulu and many more. Installation is simple, a few clicks, and you´re ready to go. 100% safety comunication, anonymity and protection by using desire PROXY server. Nowadays the Internet is big threat nowadays, even for experts! Next video shows which benefits offer this service.
Did you know that public Internet at cafes or restaurants is dangerous for your personal data? Such public infrastructure can be used to capture all your personal details. Stay safe on public Wi‑Fi by using 4096-bit encryption from end-to-end for everyone. Hide your IP address and location to prevent any attacks. It is your right to surf anonymously whenever you want. This is part of the privacy policy you deserve. Enjoy this right with Hoxx.
![]() All you need is a valid Hoxx VPN account for free and browser add-on to get started. No complicated configuration or setup is required. Hoxx VPN uses special software to ensure the fastest service possible. Filters malicious or insecure advertising network cookies to prevent them from tracking you within your country of origin. Currently supported platforms with 'Chrome' and 'Firefox' browser included 'Android' smartphone devices. Also is aviliable faster and more safely 'Premium account', with little payment, ideal for daily and intensive usage of VPN service.
All you need is a valid Hoxx VPN account for free and browser add-on to get started. No complicated configuration or setup is required. Hoxx VPN uses special software to ensure the fastest service possible. Filters malicious or insecure advertising network cookies to prevent them from tracking you within your country of origin. Currently supported platforms with 'Chrome' and 'Firefox' browser included 'Android' smartphone devices. Also is aviliable faster and more safely 'Premium account', with little payment, ideal for daily and intensive usage of VPN service.
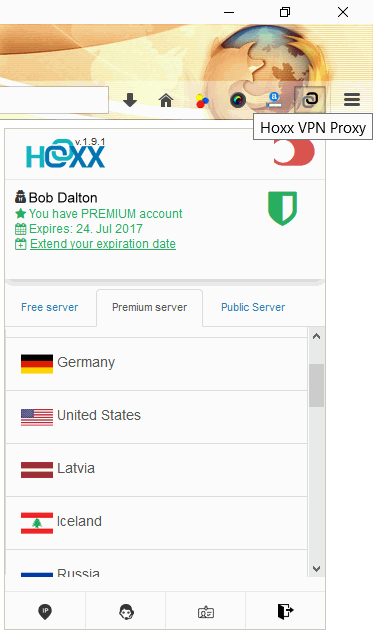
| |
| Figure 4.6.86 Menu of Hoxx service. |
Simply choice country of your interest and add-on will do rest. Symbol of red color switch will change position and become green when Hoxx become active.
SUMMARY:
What to say? Everything works perfectly!
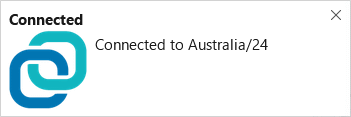 |
 |
I am not located in Australia! It's interesting to look for new location by IP address. But, do not change location when something buys from eBay or some other similar service.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |