7.5.3. Proxy server |
Not so long ago, in the age of relatively expensive modem communications as a link to the Internet world, where they are multiplied various useful and less useful facilities, a major problem was a theme to use identical content to the needs of users of local network. The more so as the use of Internet services paid ISP by the turnover realized. So if more people are using more identical contents, then why not use special computer that will keep pages of the most visited sites, as a temporary repository (cache) and serve as a substitute for the original site. Such a computer is called a PROXY (substitute) service is shown in Figure 7.5.1, first as a service that was part of a program of support on the WEB server designed for WEB content, which is essentially performing several tasks:
Basically, a proxy server is used as a temporary storage of data, and computer users are addressing him directly as data storage, not using direct communications to the outside (crossed connections). Referred to occurred in the composition of hardware web server or a separate server provided the aforementioned tasks. Hence, the scheme of communication took place is approximately as follows:

|
|
| Figure 7.5.7 Proxy server within the internal network. |
As illustrated, the proxy server must have two network cards, and as for the servicing of other services, is not only used for HTTP, but can serve users and via FTP, SMTP, POP3 and NNTP protocols through a SOCKS 4 or SOCKS 5 protocol protocol (using user authentication), which operate at higher layers of the OSI model. SOCKS protocol does not read the user's request to find out where the application needs to go, but it just passes where he tells the user that the application needs to go. Some also support TLS, SSL and HTTPS protocols. Most ISP in its own network environment uses this type of servers in order to reduce unnecessary repetition of traffic on the same claim. Using two network cards proxy server separates the internal and external traffic, which means that computer users have to configure the traffic going to the internal card server, and control traffic between the cards can provide:
Achieve certain principles of supervision, which significantly contributes to safety, which is not without significance. Although the basic principle of using a proxy server savings and accelerate Internet traffic, the possibility of filtering requirements and prohibitions set which is very interesting for the public institutions. But above provides another option to the user. Disregarding his own resources, resources can be accessed over the Internet using a proxy server somewhere in the world is shown below.
 |
|
| Figure 7.5.8 Proxy server outside internal network (anonymous). |
Anonymous proxy servers are used to hide the identity of users who are connected through them with servers available on the Internet. Then, the most commonly used open proxy servers which can be accessed like any Internet user via a web page of the proxy server site. These servers are interesting attackers (naughty) and users with the prosecuting authorities monitor access to the website, but also people who want to protect their privacy while surfing the Internet (to make it less exposed to attacks). Each user visits a web site is recorded, and this information can later be used in advertising or for establishing liability. Knowing the IP address of the computer operating system and can be exploited security holes in the PC operating system and set up malicious programs. Anonymous servers hide IP address of the user and thus protect it from possible abuse.
So, by way of a proxy server can be divided as follows:
It must be admitted that the last mentioned most interesting, especially if it is in the country on all sorts of laws about computer security does not care, and do not respond to the demands of 'damaged' on any issue. Newer software uses tunneling using SOCKS protocol, a method to circumvent the ban on access to certain websites or other services, while the use proxy servers to gain access to sites that are otherwise unavailable. Tunneling is a solution that user from one country access to web content in another state that prohibits foreigners use them. Tunneling is basically the process that involves a data transfer protocol that serves data transmission, and use of other protocols available on the physical network to distribute them. Thus, the data protocol and its associated facilities are transferred to the delivery protocol that other type in the relation to the data protocol and to serve him as a mere carrier.
Example I
Use of public PROXY server in order to ensure the safety of users regarding the monitoring capabilities of its turnover.
As for this, should take steps to communicate over the public proxy server was efficient.
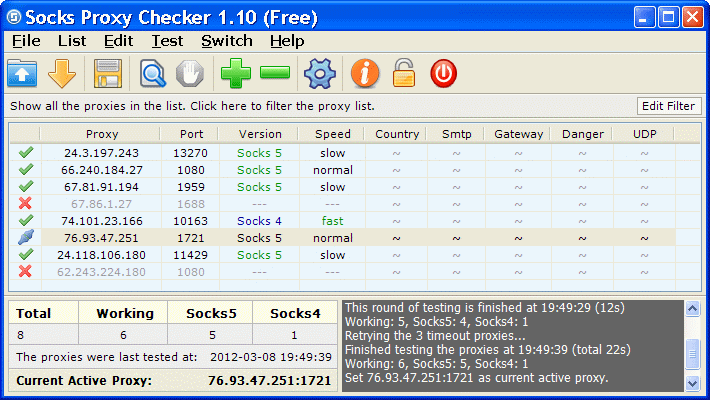
|
| Figure** 7.5.9 Creating connections through a public proxy server. ( + / - ) |
The system directory (Windows tray icon) will appear with icons of their respective menus which can perform various tasks, such as turning on and off access to the proxy server. When the proxy server is active, the user's IP address can not be seen, as shown in Figure 7.5.9c. Thus, the source is hidden destination.
SUMMARY:
The first thing to observe is that the network output goes through a proxy server network cards, and in that sense the user computer settings must be matched with the input network card of proxy server. If however the composition of proxy servers outside the local network is used in any other way, similar to the description in Example I.
Anonymous proxy servers are very easy to find with Google search keywords 'public proxy servers list', or find them with the help of a dedicated program for this purpose. But not the entire computer 'hide' behind an anonymous proxy server, but the same may be used in some settings, program support, as well as for 'µTorrent', as shown below.

|
| Figure* 7.5.10 Adjusting to an anonymous proxy server. ( + / - ) |
To make IP addresses are indeed remained hidden must shut down of the operating system the following functionality:
|
All of this can be turned off in the browser settings. For all described on this we can conclude that the proxy server is very useful. Because of their simplicity are very widespread and are used by almost all major businesses, schools, public facilities, and large Internet service providers (ISP). But for the ordinary user, usually hidden in a private ' C ' class through a SOHO device, it is sufficient to prohibit visible activity of a specific program support.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |