5.1.1. General features of Debian OS |
When the computer starts up, after loading procedures kernel, scripts are executed sequentially, which contain groups of commands in order to carry out tasks necessary to bring the operating system to the appropriate level of usability (runlevel). Mention 'single-user mode' is one of the 8 possible levels of usability, in which a computer can work as follows:
When you turn on the computer goes through a ' Single User Mode ' in which to test the integrity of the partition with ' fsck ' command. If you do not pass the test successful computer stays at that level. If the computer is used as a workstation user configurable to be activated so that the graphics support switch on, and if it works as a server is not essential to include graphics support to the computer, and service charges that are hardly used. To computer came to the fifth level of the work must be pre sequentially pass modes with a lower number. Who will be the last mode automatically achieved by the inclusion of a computer depends on its configuration, which can easily be changed because all ordinary text configuration files to ASCII code table. Therefore, the user should be familiar editor for this purpose (basically the Vi editor), although the graphical environment allows that some adjustments may be made through him, that looks like a Windows OS, but in essence once again intervene in the text configuration files.
Compared to the Windows XP system, for example, in Linux there is only one administrator (ROOT, SUPERUSER) and no user logged on it can not be declared for the administrator. Has been added to the system can not become ROOT but may only use powers that have ROOT. Can be define which users are allowed to get administrator privileges and with the safety aspect, this concept of the good. As the ROOT user system can be accessed only from the console.
If a user is accessing a computer in text mode, the intermediary between him and the operating system is a SHELL that is COMMAND INTERPRETER which are manifestations of view similar to those of DOS. The shell is not an operating system and can be necessary to install more than one system. Besides, it can be learned from one shell to another of the same or different characteristics and capabilities. Basically if you are working from the first shell starts to work in another shell first shell is inactive and waiting to return to her, or interruption in the second shell, leaving it and thus its extinction. Primary working Linux shell is BASH (Bourne Again SHell), and others if need appeared to be subsequently installed.
If you will be using console or terminal emulator to access the operating system regarding its monitoring and configuration should be able to use the operating system commands and know their syntax. The basic syntax of the command and its execution is identified by:
Based on the above, the FILE SPECIFICATIONS in the Linux operating system can be defined as follows:
| COMPUTER_NAME:/directory_1/directory_2/.../directory_N/FILE_NAME |
In contrast to the specifications in the DOS disk partitions are not relevant, separating directories is done with a ' / ' and the file may or may not have a label type. File_name should not have more than 100 characters, so you do not make a mistake with some commands. If the name of the file (or directory name) consists of several words instead of good spacing between them use the character ' _ '. Of compatibility with other operating systems are not recommended total length specification files larger than 255 characters. The file name (or folder name) must not be used to characterize uses file system ( /, :, *, ? ... ), And does not recommend the use of the grapheme of localities. The general recommendation is that the file names and directory names using only letters and numbers in the group of the first 128 characters of ASCII code.
Prompt and cursor, as well as command line syntax Windows system shown in Figure 4.5.28a are very similar to Linux. According to the above simplest syntax commands use the Linux operating system would be:
# KW -option argument |
How Linux OS distinguish between uppercase and lowercase letters, it should be about how is written KW and how to write options because there are a small and capital letters but with different effects and take account of the intervals by the syntax. Options are usually supplemented by a letter KW although there are multi-letter options as one word. Single-letter options can be strung together one after the other immediately after a ' - ' but only if used letters do not match with the name of multi-letter options. Then the single-letter options must be written individually. Multiple-letter options markets that precedes ' -- '. Sign ' + ' has reversed the effect of the ' - '.
One of the important features of the Linux OS that controls may CONCATENATE, so the result of one command to the other, which again received from the output of the first command can send your score to the third and so on. More on that in the analysis of log data, and analysis of files in which records everything that happens on the system.
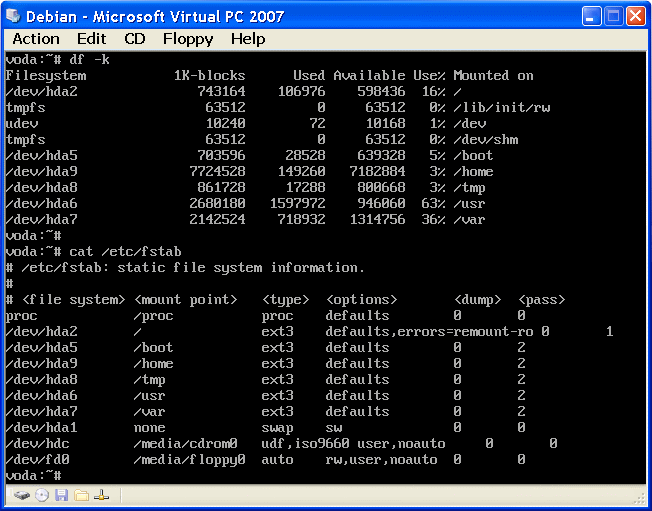
The following example is the default command ' df -k ', which gives an overview of the busy individual partitions corresponding to the planned table set in the installation process (if it is well planned?), And the command ' cat /etc/fstab ' displays the contents of the fstab file that describes that drive apart and the properties and the type of individual partitions, and are associated with anything (mount point) in order to be reachable.
|
| Figure 5.1.1 Shows the disk partition in two ways. |
It has already been stated, and with the previous image is evident that all the disks or their partitions 'hooked' directories, of course, with some of them associated subdirectories and files, and to 'move' the file system is done just by switching from one directory to another. Partition ' hda1 ' is virtual memory (swap), and after the first command does not display because it is not part of the file system. Partition ' hda3 ' primary partition which is 'container' for other logical partitions and neither it does not appear, as shown in Figure 5.1. In addition to the keywords section character ASCII table must not be used in placing the names of files and directories, as follows:
* ? < > / ; & ! | \ ` ' " [ ] ( ) { }
The names of files and directories usually are given to describe what they contain because it is possible to use up to 255 characters. One should bear in mind that instead of spaces between words using the character ' _ ' and that name does not begin with the characters ' + ' or ' - '. Uppercase and lowercase letters are different and hence the name 'Drago' and 'drago' are not the same concepts, and files starting with a dot ' . ' hidden meaning that they will not recognize any commands. Views that give the command ' dir ' and ' ls ', which are used to view the contents of the disc, best illustrate the diversity of views of certain controls and effect options for the same purpose.
More about each command can get quick help if it is provided by Form ' KW --help ', but much more to learn from the help pages per form ' man X KW '. Descriptions which can fetch command ' man ' is divided into nine sections that belong to the ' X ' in the above mentioned form:
|
Not all sections contain descriptions that refer to the command that is to be studied in greater depth. Additional very thorough description can be obtained by the command ' info ' pattern ' info KR '. In addition to the above documentation is available that describes some aspects of configuring an operating system that is located in the directory [/usr/share/doc/HOWTO/en-txt] in which the .gz format are text descriptions of specific procedures. But it would be very inconsiderate not to mention two important ways that enrich all of the user's understanding of the operating system in addition to the above, and that are INTERNET and GOOGLE, the inexhaustible source of new knowledge, not only in this matter but also in general.
So that users can access system resources and use them by default is that the system must be made-open USER_ACCOUNT (account), or otherwise called ACCESS (Log_IN), which will create an administrator, which consists of:
The system can not be two users with the same USER_ACCOUNT. Password protection mechanism is reliable as long as you wish, it should be changed often, and can be used once and mechanism usable passwords like 'token'. This mechanism should be required to use SUPERUSER (su). Except users USER_ACCOUNT have some services on the computer even though not included in the 'regular' users. Most of the services has its own user_name that operate using (as mail, news, IRC ...). We do not need to live in delusion, nothing is perfect and neither the protection of the 'intrusion' naughty, but at least they should make life difficult, maybe give up.
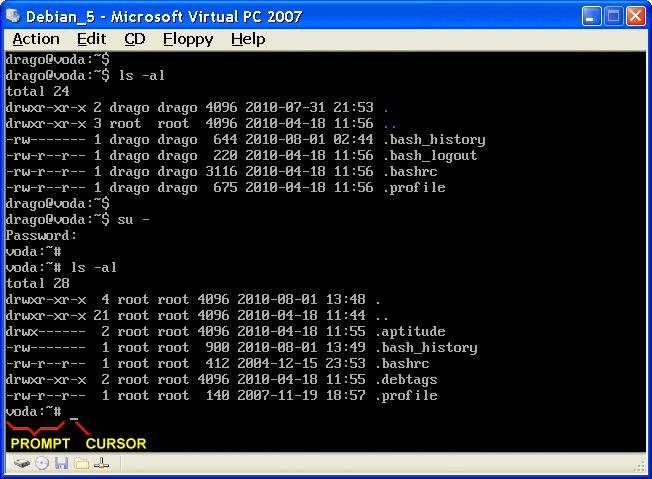
The following Figure 5.1.2a shows which contains the initial (home) directory ROOT users and to see the contents of the directory command to display the directory structure with and without options, and present the ways to get to the root directory (cd /), or to the 'top' of file system, or to the user's initial directory (cd -)), which is typically composed of [home] directory. Figure 5.1.2b shows all of which made the Linux operating system. Some of the directories are related to the partition, and the rest in one of them. More on that in the following chapters.
|
| Figure** 5.1.2 File list of user, ROOT and system / Graphical environment. ( + / - ) |
In Figure 5.1.2a shows the contents of the (home) directory of users 'drago' and ROOT. The command-line operation are two important concepts: PROMPT and CURSOR. The first shows where the user is currently located, and the other is flashing bars indicating willingness to accept (typing) controls. Figure 5.1.2b shows the composition system inspection from the roots of the tree structure of the operating system. Figure 5.1.2c not belong further described virtual machine has already been taken as an example of the virtual machine when you install all facilities labeled according to Figure 5.5c. Above leads to the conclusion that the installation of the graphics support significantly 'enriched' operating system, and if the server does not require graphics support does not need to even install it, but we should know the work in the command window.
Upon closer examination 5.1.2b image content can be seen that each file or directory name is preceded by 8 columns that describe the following:
Example I
What rights do users of system directory [/etc] from the image file and 5.1.2b [~/Xauthority] at picture 5.1.2c?
Directory [/etc] in the first column has the tag 'drwxr--xr-x'. The first letter represents a directory in question and the third and the fourth column shows that its owner a superuser (root) and belongs to the group 'root'. Superuser has the rights to write per file and read the contents of the directory to run the execution (the next three letters - drwxr--xr-x). With superuser in his group, which means there is no one that he was the undisputed master of this directory. How are the configuration files have the right to read the other groups (three letters after superuser rights - drwxr--xr-x) and the users (the last three letters - drwxr--xr-x), and that there needs to be a single file in the directory must be able to perform, certain contents of the directory will be allowed to perform any of the group and the individual and from any group, and from a user. User group, and other users can not write anything on these facilities.
Xauthority file has a tag-attributes '-rw-------'. The first character has no meaning in terms of files, the user is the owner of her and belongs to his group while all the rest have no rights to it. The file is created in the user's initial directory [/home/drago/] which recognizes and record the prompt. Since this is the configuration file does not need to be executed by the user, since it serves to a certain software only read. None other than the operator of this file is not exercised any rights. No user settings are written in it at the sole discretion may change. Of course, the superuser can work with this file whatever he wants.
Directory Linux as opposed to Windows system has its own size. Directory and files are identified by their identifier that creates a file system which assigns a file name or directory. Directory is nothing more than a file that contains a list of identifiers which is attached to the file description, and that coupling to the files that are in the list. The figure in front of the book is not the sum of sizes of all files in a directory, but the file size that contains the list. Similarly, the files for the drivers. They do not contain some binary files but indicate a place where they call from the kernel and possibly the fact that the module connected. Executable file is in turn a set of binary records which processor or command interpreter can execute. So, in the Linux operating system everything is files. Disk devices and partitions are identified with a name and a directory structure for hierarchical distribution uses a ' / '.
Debian filesystem in core contains support for multiple file systems that are not subject to copyright other manufacturers: ext3, reiser, xfs and jfs. File systems of the same type configured with different parameters or different file systems by type, again by adjusting certain parameters that allow each partition by peculiarities largely adapted to the task for which it was intended. In this way, the operating system becomes more efficient. Due to copyright in the core can not be incorporated support for Microsoft FAT 32 or NTFS file system or a third-party software, but available as external modules that enable you to work with them.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |