Encrypting - GnuPG (GNU Privacy Guard) |
|
|
 The usual exchange of electronic mail, or sending any data over a communication channel, and generally through the Internet service, is subject to the possibility of eavesdropping and abuse. Depending on the circumstances, the consequences can be devastating. Therefore, methods have been developed that are used to make content comprehensible to anyone unfamiliar to the particular algorithm - the KEY before sending the content, and that upon receipt of such facilities by the same algorithm in reverse procedure unintelligible content so friendly. Procedure 'hiding' original content is called ENCRYPTION, and the process 'discovery' of the original content from the 'hidden' is called DECRYPTION. Methods that permit it deals with CRYPTOGRAPHY - the science based on applied mathematics to protect the message from unauthorized use, and that can be transmitted in different ways, and thus as an electronic message via the communication channel. Special software (encrypts) the emails so that no one can decipher (decrypt) unless the person to whom it is intended, or adds a digital signature to understand arbitrary text messages about checking its authenticity.
The usual exchange of electronic mail, or sending any data over a communication channel, and generally through the Internet service, is subject to the possibility of eavesdropping and abuse. Depending on the circumstances, the consequences can be devastating. Therefore, methods have been developed that are used to make content comprehensible to anyone unfamiliar to the particular algorithm - the KEY before sending the content, and that upon receipt of such facilities by the same algorithm in reverse procedure unintelligible content so friendly. Procedure 'hiding' original content is called ENCRYPTION, and the process 'discovery' of the original content from the 'hidden' is called DECRYPTION. Methods that permit it deals with CRYPTOGRAPHY - the science based on applied mathematics to protect the message from unauthorized use, and that can be transmitted in different ways, and thus as an electronic message via the communication channel. Special software (encrypts) the emails so that no one can decipher (decrypt) unless the person to whom it is intended, or adds a digital signature to understand arbitrary text messages about checking its authenticity.
Since ancient times, people are using various cryptographic techniques to hide the original message so that it is completely incomprehensible to unauthorized persons who came into her possession. Eventually, the idea emerged display font other symbols, or simply mixed characters facing some legality. These and similar simple methods were used until the Middle Ages, when a need for better methods of hiding a secret, mostly because of the influence of politics and religion. Examples of which are still in use today as Morse's code, Braille and ASCII are not cryptography but encoding, encoding and decoding are an integral part of cryptography.
One of the first applications of encrypting messages dating back to the Roman empire that has been used very simple encryption algorithm so that the letters of the alphabet are shifted by three places to the right:
ABCDEFGHIJKLMNOPQRSTUVWXYZ - Drago
by shifting of three places to right gets the alternative alphabet:
DEFGHIJKLMNOPQRSTUVWXYZABC - Gudjr
According to the above D=>G, r=>u in onwards. From recent history, from World War II is known devices he used the German army called ENIGMA, electromechanical device like a typewriter that had the task of characters mix to by the specific key, regardless of whether the character is repeated or not.
 |
|
| Figure 1.1 Enigma. |
At that time the allies have committed significant material and human resources in order to decrypt messages encrypted with Enigma. One effective method was the 'theft' of this device, which was made into a movie 'U-571', which describes the entrapment of the Enigma from damaged German submarine. Today, in an era of rapid and efficient computing devices cryptography is significantly better performance except the encryption method enabled the successful 'break' code. On the Internet you can find sites that use 'Java Script' plug-in to successfully simulated the Enigma. At that time it was not the computer that it could be done quickly and successfully. Basically, a code must be safe from 'hacking' for as long as is necessary to carry out the task that successfully hides a coded message. A performance basically depends on the algorithm and complexity of KEY. Strong cryptographic tools and algorithms enjoy a status similar to nuclear armament and often are a state secret of the highest priority. However, confidential documents still carries a courier surrounded by an entourage.
In terms of the OSI model, encryption can be done at any layer that contains data, so either character or binary. If applied to content that is sent by e-mail, it's about encrypts characters, which is the theme of this pages.
Basically, two types of encryption algorithms are in the procedure:
Even this brief description shows which the mechanism is easier. Symmetric key is similar to password-protect the contents of the compressed file (.zip, .rar ...), but only password protects the contents of a key and its corresponding algorithm to change the content which is not the same. The principle of using symmetric and asymmetric key is shown below.
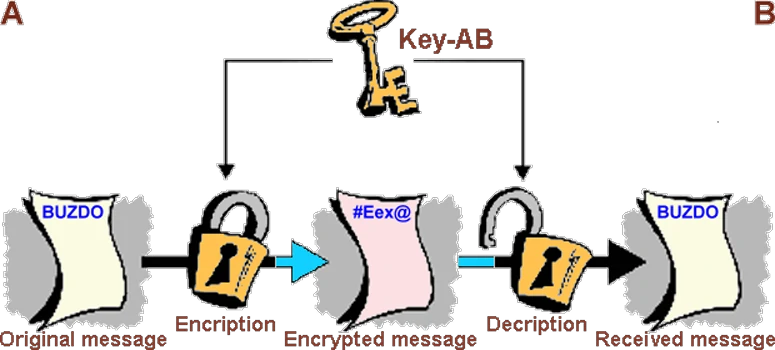
|
| Figure* 1.2 Symmetric / Asymmetric encryption of messages. ( + / - ) |
In symmetric encryption the recipient can read the message only if it receive the key that has the sender. A good feature is the ease, and bad traits is the inability to read messages from the sender and the receiver if the key is lost and the need for frequent change of key for security. Asymmetric algorithm increases safety analogously using two key of treasury, solves the problem of lost keys sender, but does not solve the problem of quick replacement of the existing key with new key. If you take into account of the user 'inertia' about updates of keys from the security point of view is presented solutions are not effective. The problem is solved Philip Zimmermann 1991st when published PGP (Pretty Good Privacy) software for encryption and digital signature. Takes the best features from the fields of symmetric and asymmetric encryption systems combining them into a powerful protocol. The mechanism is proved so good that he almost spent the rest of his life in prison for his public publication. The prosecution was based on the export of strong cryptography software outside the United States as per their laws prohibited.
PGP encryption mechanism uses symmetric and asymmetric encryption (hybrid cryptosystem) is shown below. Each user has a pair of asymmetric keys one of which is a PRIVATE (personal) and the other PUBLIC. Data is protected DISPOSABLE symmetric key that is automatically generated for each message (session), respectively, and the key to this is being done is sent to the sender of protected asymmetric encryption using the recipient's public key. One-time (session) key generated by PGP (GnuPG) software and the complexity of generation is a major safety factor in the process of encryption. What is the time period to generate the sequence of keys is that much more difficult to identify the way in which the sequence is generated based on 'interception' of its parts. If the importance of software and its application of large, repeat the sequence generated keys is measured in years, despite today's fast and powerful computing resource.
Parts of the PGP program support are:
For each message generates a new one-time 128-bit key size. Computer generated one of the possible 2128 = 340 282 366 920 938 463 463 374 607 431 768 211 456 different binary combinations (about 1039 combinations). But the computer is not able to create a real 'accidentally' generated binary numbers, but it uses a generator of pseudo-random numbers generated by a series of numbers that appear to be random, but the reality is that a number generated always in the same way. Therefore, it defines the initial state from which this generator begins operation and that is not always the same. The possibility of breaking the PGP system exists, but only if we know the initial state of the pseudo-random numbers, because only in this case it is possible to predict a series of numbers to be generated. The solution to this problem is well hide initial state generator which takes care of PGP software. Principle of operation of PGP encryption mechanism is shown below.
 |
| Figure 1.3 PGP encrypt messages using a one-time (session) key. |
Symmetric encryption, which refers to encrypt the message, use a one key during the process (session) of encrypting and decrypting messages. The following message is a new session with a new SESSION DISPOSABLE key (ONE-TIME key). Each new message requires a new DISPOSABLE key. DISPOSABLE key sender encrypts using the recipient's PUBLIC key and asymmetric algorithm. Once this is done, the encrypted message is sent along with the encrypted key to her decrypt. Unless otherwise ordered by the PGP will perform the first step in the message data compression algorithm, ZIP, no password, which essentially does not change the message, but it makes it less volume and more resistant to find duplicate samples about 'intrusion'.
To read the message recipient must use his PRIVATE and PUBLIC key to decrypt the DISPOSABLE key of message. Then with DISPOSABLE key decrypts the message. The public key is incorporated into the message sender that he was the recipient ga personally given or the recipient's public key is stored on a PGP public server from the Internet. Therefore, the public key and the person people are mathematically linked inseparable pair in the community with a single key to encrypt and decrypt messages. The message can be encrypted with a single public key, which means that it is geared towards a single user to simultaneously send messages to multiple addresses is not possible.
For keeping the public key is used PKS server on the Internet (Public Key Server) that allows receiving and sharing them and PGP PUBLIC compatible keys, for example 'pks.aaiedu.hr' is PKS public network server of CARNet which is in synchronization with other servers of PGPNet worldwide network. Public key published in any of the servers in the world are identified and through this server, whether it is through the post or not. On each of the servers on the synchronization procedure with the others to form a redundant copy of the key to the world in a decentralized network structure, and the key is continuously available. Once published public key can not be cleared, only to be declared invalid, but only if the private key is available and if the password is not forgotten :-).
How to verify that the private key corresponding to the public key of the person who sent the message? If the recipient wants to check who the sender of the message, the sender has to 'SIGN', which makes using its own private key. Recipient using the sender's public key along with the fact that the personal and public key uniquely mathematically related, it checks whether the signature is valid. If the signature is valid, it means that the sender is also listed and the actual sender of the message, because by definition, only the sender knows your private key, so no one's signature can be forged. DIGITAL SIGNATURE is realized in the following way.
 |
| Figure 1.4 Signature of unencrypted message. |
Sender real message summary with oritmom to compute summary (hash function) that encrypts the private key and a summary sent along with the message, or separately from the message. Hash functions from small or very large messages are always right truncated form of constant size (message digest). Such an encrypted message is summary message signature (fingerprint) that will match the received message if the signature or messages are not tampered with, or if the person who sent the message is really the person to whom it is issued.
When the recipient receives the message and its signature, it decrypts the sender's public key summary. After decrypts abstract, summary account the messages and compares it with the decrypted summary. If the summaries are the same, the message is authentic. The signature can be used by itself in case the message is not confidential and should not be encrypted, but of great importance is its authenticity and integrity. The message can be signed only one private key, which means that the simultaneous sending unencrypted signed messages to multiple addresses possible. Signature verification is performed senders public key.
According to the previously described logical that the message can simultaneously encrypt and sign, and since then the recipient is sure that the message is sent to the right of the person who claims to have sent a message and that message sure nobody except him can not be read. The analysis of previous images 1.3 and 1.4, according to the above can be simultaneous encryption and signing using public and private key are records within them are interrelated. The message is first signed by the sender's private key, and then encrypts the recipient's public key and then sends, without the use of one-time (session) key. The message is then treated as a DIGITAL STAMP.
For encryption shown schemes, the blue color-coded arrows describe the direction of unfolding processes of encryption and decryption keys denote messages or communications channel that connects the two endpoints of communication, users ' A ' and customers ' B '.
And what's the key? If the specific page of a specific book donated a piece of paper with holes that will on the specific page cover most of the signs and allow the reading of specific characters, then this paper is the key to reading that page, and schedule a hole is algorithm. For the entire book should key for each page, and encryption methods used today are a group of letters which applies to the entire message as shown in the following example.
Example I
Example of generated key pair necessary for the PGP encryption method.
************************************************************************
* WARNING: This file is a backup of your secret key. Please keep it in *
* a safe place. *
************************************************************************
The key backed up in this file is:
pub 1024D/3D0C8FF8 2009-04-26
(key_size_in_bits/IDENTIFIER Creation-date-key)
Key fingerprint = 98FF 763A 6AF6 AEF6 1B33 C8BC F719 447B 3D0C 8FF8
(checksum of certain parameters of the public key)
uid Drago Radic (For the purposes of 'alphabet') <tupko@buzdo.com>
sub 1024g/A133AFBD 2009-04-26
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: GnuPG v2.0.10 (MingW32)
mQGiBEn0MvMRBACg5QL4VYjutTntcz0Xgnvy4MdF7yXofTJsg5faGVkWsEW/ZwNe
QoVIZrWdls2wiXHkxLQ/1ehcMeo5bJdkthJYuw1jr2noDsC9zdhtw68X9vDbQdwi
A7S+FLB88HsNbXfueKgeyhGXh5qlmBOzXNdwi/MR5X8hft1iimem4JaMhwCgynHq
j+cndNIcTH9meQ4c1R2XPAUD/2719NBSUtfJ8vY7SVNXW24mkd5s+pAn/zS4pzcU
BZA0sjxa83I+D r1AXosnNrIkQ4v2E7m
oiy45v01UsnAI tU8/nZDmGCCZoFg1NU
3Ur2A/9LQrM9S The public key XJEjY2cF/Fwx/Gw+bq
wQCusWoWg7Vsq basically 9mla+Z/tYt16qI8cWh
kR804faea5ygp publishes wlELQ0RHJhZ28gUmFk
aWMgKFphIHBvd on the server V6ZG8uY29tPohgBBMR
AgAgBQJJ9DLzA of public keys. AACgkQ9xlEez0Mj/iO
EQCfVOAUmkQud It can not be misused H9h5HIAeCS3EuquQEN
BEn0MvMQBAClr without the private key. UCIbEXCxgK1uRvFNYR
WvEv90oGzom/h brg5HhphXXljl5exVY
IG7L/7HWGXbF/ V1fttdvwADBQQAgyY1
UhHji2w/D/UCq3L6MWiUq7vUX74R12Fp0CoJYnZnuVwaaMlGy/Iip1DROGaE5evG
uyRE/z+M2flsdDvn10ENRRAknK1MQFdFpnxoPCW29Gd1ASuCLuSnAtlQ2CKMc8VR
7GMx3gSsVjXvK8tnavLP2aXTUK2HFsdaIVEr7TiISQQYEQIACQUCSfQy8wIbDAAK
CRD3GUR7PQyP+NuBAKCvFmvZ3lkNYFg4LpLn83RgjahUwwCfU1PrT7QmZfBEVfxY
Jcu68U5HmZg=
=EbV+
-----END PGP PUBLIC KEY BLOCK-----
-----BEGIN PGP PRIVATE KEY BLOCK-----
Version: GnuPG v2.0.10 (MingW32)
lQHhBEn0MvMRBACg5QL4VYjutTntcz0Xgnvy4MdF7yXofTJsg5faGVkWsEW/ZwNe
QoVIZrWdls2wiXHkxLQ/1ehcMeo5bJdkthJYuw1jr2noDsC9zdhtw68X9vDbQdwi
A7S+FLB88HsNbXfueKgeyhGXh5qlmBOzXNdwi/MR5X8hft1iimem4JaMhwCgynHq
j+cndNIcTH9meQ4c1R2XPAUD/2719NBSUtfJ8vY7SVNXW24mkd5s+pAn/zS4pzcU
BZA0sjxa83I+D r1AXosnNrIkQ4v2E7m
oiy45v01UsnAI tU8/nZDmGCCZoFg1NU
3Ur2A/9LQrM9S This private key XJEjY2cF/Fwx/Gw+bq
wQCusWoWg7Vsq kept in the form of 9mla+Z/tYt16qI8cWh
kR804faea5ygp file on the storage wlEP4CAwKwpLUMFYL2
1GCCLOHtvvE7n medium or printed, pbs5+RgTEs4mRx3r7N
yhqgerQ0RHJhZ and must be unavailable NlZGUnKSA8dHVwa29A
YnV6ZG8uY29tP to other persons in QVAggDBBYCAwECHgEC
F4AACgkQ9xlEe respect preventing LWdRsAn034hClIJqR6
kJH9h5HIAeCS3 its misuse. dk2L5Vxhab6eLDPhED
rEUCIbEXCxgK1 ORNIX8IoLMLPj+9aRc
U9brg5HhphXXl 2MBA7k8DRy9ktgvpUG
FCV1fttdvwADB 4R12Fp0CoJYnZnuVwa
aMlGy/Iip1DROGaE5evGuyRE/z+M2flsdDvn10ENRRAknK1MQFdFpnxoPCW29Gd1
ASuCLuSnAtlQ2CKMc8VR7GMx3gSsVjXvK8tnavLP2aXTUK2HFsdaIVEr7Tj+AgMC
sKS1DBWC9tRgY4xuob6P+A8mTt+muSuHShZwODekDIP2ZTIAA7WdtJqGSSHn5sm+
IohczFFz2L4pYfvmGvuw1a9MO1zSElGISQQYEQIACQUCSfQy8wIbDAAKCRD3GUR7
PQyP+NuBAJ4m0c1vfiiVVy96quvbDrq/ajgLJgCZAWgQ/jC7wB4Hd3XGWiGuysE2
j6M=
=eYIR
-----END PGP PRIVATE KEY BLOCK-----
Displayed content is backup asymmetric keys stored in the file secret-key-3D0C8FF8.asc. When generating a displayed pair of keys, public and private (personal), seeks to define security PHRASE that is used to generate the key, and as a kind of password, the longer the key to a more diverse and allows to incorporate the changes in the key, for example 'Buzdo is stupid' . This file should be kept in more secure places, but can not be so sure that it can not find the later :-). By changing the content of the phrase private key. It has been said that the personal and public key uniquely mathematically related so that one can not be disclosed without the other.
Public and / or private keys are added to .gpg file called ring of keys (keyring), base - a collection of keys in which the keys can be added or deleted from it. So there are two rings of keys: public and private (secret). Each key pair has its own unique code regarding recognition - an identifier (8 characters; 64 bits).
Each block of the key concepts mentioned PGP and GnuPGP in the header block. OpenPGP is the most widely used standard for encrypting e-mail messages to the world. It is defined by the OpenPGP Working Group of the Internet Engineering Task Force (IETF) standard RFC 4880. OpenPGP standard was originally derived from PGP (Pretty Good Privacy) template that was originally created by the 1991. by Phil Zimmermann. But the product is commercialized and the only thing is it's free to download demos of software and do not pay the license rights (hence the word 'Open'). On its foundation community has responded with Free 'GNU Privacy Guard' project on which more can be found on the pages to which leads-coupling logo at the top of this page (basic GNU is described in the dictionary).
 Project is basically about developing the software for Linux and Windows platform, although the compiled source code works on other platforms. 'Gpg4win' is a free computer software for Windows operating systems (2000 / XP / 2003 / Vista) which allows encryption of email and files. Both relevant cryptography standards are supported, OpenPGP and S / MIME (the latter is currently working within the 'Claws Mail' program support). Both are based on the use of the MIME (Multipurpose Internet Mail Extensions) structure of messages using electronic mail. Software consists of the following software components:
Project is basically about developing the software for Linux and Windows platform, although the compiled source code works on other platforms. 'Gpg4win' is a free computer software for Windows operating systems (2000 / XP / 2003 / Vista) which allows encryption of email and files. Both relevant cryptography standards are supported, OpenPGP and S / MIME (the latter is currently working within the 'Claws Mail' program support). Both are based on the use of the MIME (Multipurpose Internet Mail Extensions) structure of messages using electronic mail. Software consists of the following software components:
Free software for the Windows platform, composed of GnuPG project (GPG) is available at the site at: https://www.gpg4win.org/download.html. Windows platform has been chosen to describe the fact that it uses approximately 90% of the readers of these pages. The following pages describe how to use the above.
Complicated? It really is, but the software 'EssentialPIM', whose logo is the image in the header of the paragraph (the image is also a link to the site of the company ASTONSOFT that made it), solves all of the above in a very simple way. 'EssentialPIM' has evolved over many years to be a flexible, yet very intuitive application that gets user can started within minutes. All its features ensure that the user is truly the true master of users data. And a good product has to be paid for, right?
|
|
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/specific/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |