Encrypt & Decrypt Message Keys |
|
|
PKS (Public Key Server) servers have already been mentioned and their working 'port' is the 11371. The list should be added to the existing servers that you want to apply the key, although their content generally synchronized. But on this occasion were selected servers 'CARNet' i 'uBuntu' sites, while the others deleted is shown below.
 |
 |
| Figure* 3.1 Adding a new server to the list of PKS. | |
Choice /Keyserver/ at Figure 2.7b offering previously shown window and highlight the desired server with L1, than D1 action /Remove/ delete a registered server, and D1 action on an empty window without labeling server allows selection /Add/ type the URL of the new server and add it to list.
Once the keys are generated, and the registered servers which are believed to be properly maintained and synchronized with other servers in the network such purposes, the public part of the key to be published. This is done by selecting the desired key with L1 and choice of action at D1 /Send to keyserver/-/ URL of required server/. A safer way to sign the public key to the PKS server is to copying the contents of the public key together with header and footer in the form of PKS server, and after the completion of registration server addresses like 'URL_of_PKS_server:port_number' by which follows a page that contains the following forms.
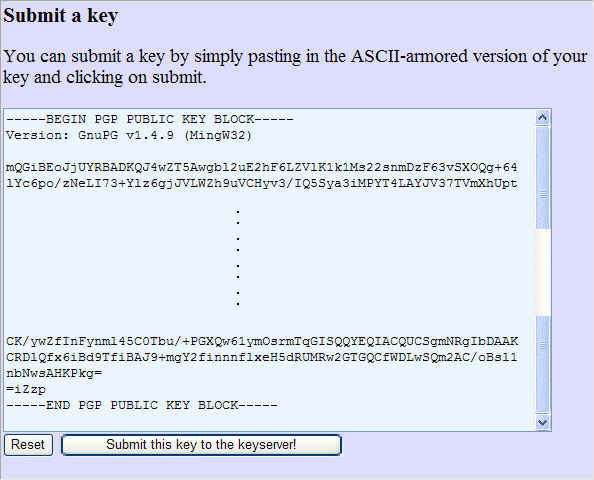 |
| Figure 3.2 Sign the public key to the server. |
When a block of ASCII characters of the public key is copied into the given form and application by selecting (Submit this key to keyserver!) key is forever written, it can not be deleted and can only be repealed.
User identification to PKS server is done by entering its name and last name (watch out for localities graphemes) or Key ID in the form and will get the information about the user and is available to his public key.
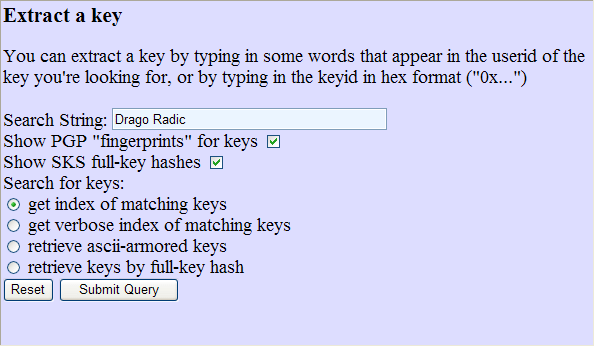 |
| Figure 3.3 Find the key and information about the user. |
Reply PKS server on the data entered in the previous form is:
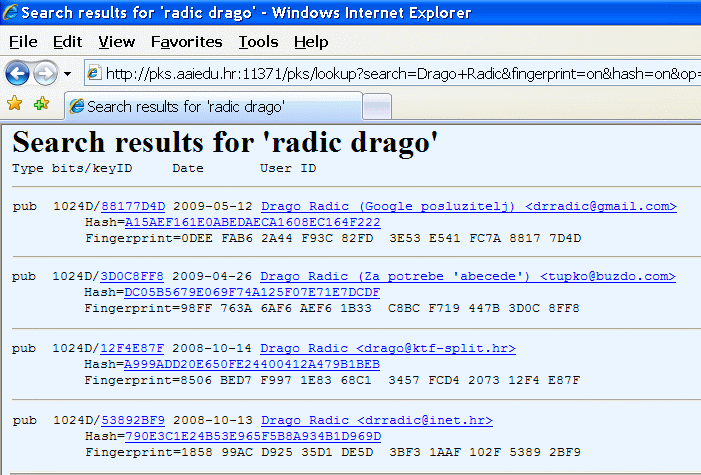 |
| Figure 3.4 An overview of all public keys of user at PKS server. |
Obtain all the information about the user (name, comment, Key ID ...) which means that all you need to sign the public key is contained in the data block of public key.
The last thing they have to do is create a new storage location of the keys work out of the system partition disk or directory [Documents and Settings\Drago\Application Data\gnupg\ ...].
|
|
| Figure* 3.5 Directory with keys. ( + / - ) |
The new directory is copied files already entered keys (pubring.gpg, secring.gpg and trustdb.gpg), or change the location to do this before entering the keys. As is customary for Windows, useful data are scattered 'everywhere' (installation directory of software, All Users, User ...). Content of place with keys at the new created directory is shown in Figure 2.8.
Additional assistance in working with keys enables /GPA/ (GNU Privacy Assistant) program support which the main working window is shown in the following figure.
 |
| Figure 3.6 Alternative handler of keys. |
Marking the desired key, and selection /Backup.../ action D1 on the key to saving both keys, key identifiers and general data in one file, such as secret-key-3D0C8FF8.asc, which is very convenient as it is all combined in one place for only one set of keys and is perfect for storing. All facilities are in ASCII format (plain text with no formatting) to Example I.
The former features describing the principles of encryption keys making their announcement on the PKS server for PGP / GnuPG program support. This should be used at least for the simplest task: encrypting files and its association signed message to the possibilities of software as shown in Figure 2.9.
Action D1 at designated file, for example 'Beast-v2.07.txt', size of 3885 B and choice /GPGee/-/Encrypt (PG)/, and selecting the public key users to Figure 3.7a, is automatically created in the same directory file 'Beast-v2.07.txt.gpg' size of 1973 B, then compressed and encrypted file.
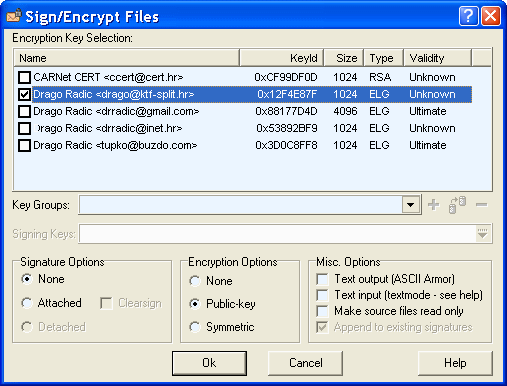
|
| Figure* 3.7 Selection of key for the encryption. ( + / - ) |
Of course, one should choose a public key users to whom the message is sent (recipient), whether it is the recipient submitted by electronic mail or otherwise, or in downloading ring set with PKS server (blue key at Figure 2.7b). From the menu, and you can see in the figure above, it can be executed with a symmetric key, but then it is not by the principles of PGP.
Choice of /GPGee/-/Sign/ at the file 'Beast-v2.07.txt' requires the use of a private key the sender, according to Figure 3.7b, to sign a message, and automatically creates the file 'Beast-v2.07.txt. asc' size of 202 B in the same directory where the original 'Beast-v2.07.txt' file, which is a summary (hash) of the original message and contains information such as the following:
-----BEGIN PGP SIGNATURE-----
Version: GnuPG v1.4.9 (MingW32)
iEYEABECAAYFAkoJucAACgkQ/NQgcxL06H/73ACfVZFQthv0zm/q0J0SLQY/g8eY
pWEAn0htfqI31DqfPwP46jkg71pBFquZ
=+C9D
-----END PGP SIGNATURE-----
Ultimately is sent to e-mail in which an arbitrary text attachment 'Beast-v2.07.txt.gpg' and attachment (not text messages) has been signed with the above-mentioned items that are simply copied to an electronic message to any location . Since the signature of the 'Beast-v2.07.txt.asc' files with its own extension, and it can be sent as an additional attachment. Therefore, the content of e-mail attachments that is added to send, is encrypted content and digital signature. If you want to decrypt the message received from the already used the menu to select /GPGee/-/Verify-Decript/. In the process of encrypting and decrypting messages in different stages to enter the security phrase, and it is nice that the phrase is long enough and that is easy to remember, such as a phrase in the introduction to this topic. With the described procedure can send confidential messages by any software for electronic mail.
SUMMARY:
Of all the goals in the attainment of security of message transmission through the communication channel, the following four are the backbone of all activities during the implementation process protections can occur:
 For ease of use of software described can be used addition 'GNU Privacy Guard - Outlook Express Plugin' (GPGoe) which works with versions of Outlook Express 6.x or higher for both Windows 2000 and Windows XP. An earlier version of this plugin (v0.7) is shown to be stable. First initiated by addition and then start OE program support Then in the menu to create a new message, use election /Sign/ and /Encrypt/. For Outlook 2003 GPG support (GPGol) but is incorporated in the software package described by these sites. Way to use the Outlook program support is not the topic of this site, and whether the designation of their availability. But there is something important to mention, one of the best e-mail programs on the market is 'EssentialPIM'. It contains the following basic features: use of several different user accounts, common or separate directories for user accounts, selection of different security protocols for logging in to the account, full support for PGP and many other possibilities. Google considers it completely reliable. The image at the beginning of this paragraph is link which leads to the site of this software.
For ease of use of software described can be used addition 'GNU Privacy Guard - Outlook Express Plugin' (GPGoe) which works with versions of Outlook Express 6.x or higher for both Windows 2000 and Windows XP. An earlier version of this plugin (v0.7) is shown to be stable. First initiated by addition and then start OE program support Then in the menu to create a new message, use election /Sign/ and /Encrypt/. For Outlook 2003 GPG support (GPGol) but is incorporated in the software package described by these sites. Way to use the Outlook program support is not the topic of this site, and whether the designation of their availability. But there is something important to mention, one of the best e-mail programs on the market is 'EssentialPIM'. It contains the following basic features: use of several different user accounts, common or separate directories for user accounts, selection of different security protocols for logging in to the account, full support for PGP and many other possibilities. Google considers it completely reliable. The image at the beginning of this paragraph is link which leads to the site of this software.
And if someone steals the key? A person using the key must proclaim it as invalid because the key can not be canceled (deleted) which can only be if it is still available private key. Otherwise, as soon as possible make known to customers that the key was stolen. Except for the exchange and protection of e-mails and their attachments described mechanism of protection can be used to encrypt data on disk or USB stick. The most interesting application of practical validation of default actions in the process of performing financial transactions through Internet services - INTERNET BANKING.
|
|

|
|
| Figure 3.8 Token. |
Small generator (token) one-time password that is generated for the user by a complex sequence of numbers where the initial place of use specified PIN (Personal Identification Number) which the user must first be changed, because initially all the same, then it can be further change at the discretion and thus affect the initial site using the generator sequences. The serial number of the token has the role of the public key of user, the number knows bank and user.
|
|
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/specific/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |