GNU Privacy Guard for Windows |
|
|
The PGP mechanism data is encrypted in a way that is divided into 64-bit blocks and each block is then encrypted using a single key generated for a symmetric algorithms. PGP uses a symmetric algorithm IDEA (International Data Encryption Algorithm) which uses a 128-bit key. IDEA is used 52 subkeys length of 16 bits for encryption. The algorithm is executed in 8 iterations, and procedures that are repeated. Block of plain text is decomposed into four 16-bit parts. The transformation of the input text in the output, IDEA uses three types of operations: addition (+), the logical XOR operation (x) and multiplication (*) is shown below.
 |
|
| Figure 2.1 IDEA encryption algorithm. |
From the 128-bit key are generated 52 subkeys contains 16 bits. In the first iteration, the previous figure, a 16-bit message (txt) and 16 bits of individual subkeys (PK) processes for mathematical and logical operations. In one iteration is used 6 subkeys. After 8 iterations used is 48 subkeys is last 4 subkeys performs the final encryption of messages. From the the presented algorithm shows that it is based on the processing of bits in the message and not the characters, which means that it is applicable to any content in the message. Can use some other symmetric algorithm. IDEA is a patented algorithm and therefore not applicable in the GNU project, but the module can be used, along with meeting the licensing rights, which GNU software may be used. GnuPG software can decrypt and verify PGP 5, 6 and 7 messages, and algorithms used are: ElGamal, DSA, RSA, AES, 3DES, Blowfish, Twofish, CAST5, MD5, SHA-1, RIPE-MD-160 and TIGER with the possibility of module implementation with some other algorithms.
![]() GnuPG originally designed for Linux operating systems, and the like systems. 'Gpg4win' is only part of the project relating to the software package for Windows operating systems (2000 / XP / 2003 / Vista), which includes computer software for encrypting e-mail messages and files along with their manuals. Supported the OpenPGP standard, and with him and the S / MIME standard, but only with the 'Claws Mail' program support for e-mail. Free for use by the GNU principles. Main purpose GPG4win (GnuPG for Windows platform) is the use of computer programs as follows:
GnuPG originally designed for Linux operating systems, and the like systems. 'Gpg4win' is only part of the project relating to the software package for Windows operating systems (2000 / XP / 2003 / Vista), which includes computer software for encrypting e-mail messages and files along with their manuals. Supported the OpenPGP standard, and with him and the S / MIME standard, but only with the 'Claws Mail' program support for e-mail. Free for use by the GNU principles. Main purpose GPG4win (GnuPG for Windows platform) is the use of computer programs as follows:
Combinations of these methods to use are possible according to user needs :). Unencrypted and unauthenticated combination serves the majority of email users, probably because they feel that they have nothing to guard against unauthorized reading. To order any of the above should have used the locking mechanism - PGP / GnuPG, and make a key that will know how to work with locks. Better to say a couple of keys, similar to two keys of treasury, which allow the use of all the benefits that locking mechanism offers.
When installed 'Gpg4win' program support, in the start menu are created in addition to other icons with names /WinPT/ (Windows Privacy Tray) and /GPA/ (GNU Privacy Assistant). The first listed software further written, and the other is listed alternative program support for key management. When activated icons /WinPT/ system menu (tray menu) icon appears in the form of a key action that D1 offers a menu that shows the next image.
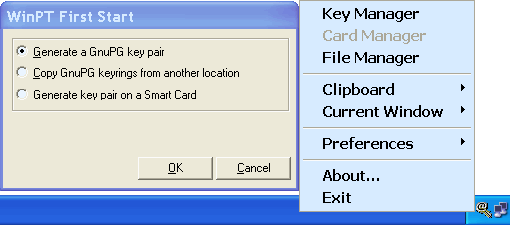 |
| Figure 2.2 Generating a key pair. |
Choice /Key Manager/ can not be activated until after the at least one key pair, indeed automatically provides a window to the previous image to produce a first key, copying existing keys from a location with a ring of keys or generate keys for the card (smart card) . Other choices are not relevant while not making keys. Well immediately, selection /Preferences/-/GPG/ that offers a window to Figure 3.5 in order to instantly change location 'Rings'. Creation of the first pair of keys also means making rings for keys (keyring). Storage location for the new rings to choose a place that is not part of the system software or disk partitions, and possibly to restore the image of the system partition drive without destroying the actual data.
Rings' is a term that is used analogously Round Arrangement of split rings and are on one of the keys for example, home and vehicle (personal-private keys) on the second ring of the keys to the front door of the building and the parking garage for the vehicle. These two rings are connected with another ring, then paired. In this sense, kept the keys that are generated by this program support and must be at least one pair of keys that will be valid. Namely additional keys analogy described example can be the key one room in the home and lock to start the vehicle, or a new set of keys from the vacation home.
The first couple of keys to make it, the window in Figure 2.2 and opens the window to the next picturewhich asks you to enter personal data; elections |Real name:| and |Email address:|.
 |
| Figure 2.3 Record information about keys. |
For this data is not good to enter some incoherent content when that they intend to publish on PKS server, because then it is doubtful that the person behind these data and whether the recipient of the message to be of importance. The displayed text in the image should be seen only as an illustration. Choice |Prefer RSA keys| gives the possibility of generating a set of keys to the 'Rivest-Shamir-Adleman' encryption algorithm that is different from default DSA / ELG algorithm (Digital Signature Algorithm / ELGamal), which became an international standard and is used for the digital signature in the U.S.
 |
| Figure 2.4 Entry of phrase. |
Following completion of the basic data entry will be prompted to phrase that as a longer, offers diverse key and repeat queries to input phrases regarding its verification follows generate keys with a graphic showing generation of signs of progress as illustrated by the next image.
 |
| Figure 2.5 Procedure of generating keys. |
Then we need to confirm that everything is done right choice | OK | as shown in the next window.
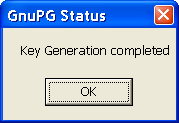 |
|
| Figure 2.6 Status. |
When the key generation is completed, saved in .gpg files, one of which is 'carrier' of private key and the other of public. Follows immediately offer to save the backup copy of your keys, and you can choose a new directory or device (floppy, stick ...) to store data.
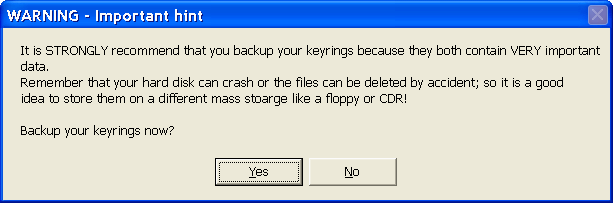
|
| Figure** 2.7 Backup of key rings / Key management. ( + / - ) |
Figure 2.7b shows an example of generated keys of which are by generating their public keys published. From left to right shows everything that has a pair of keys shown in Example I on the first page:
It has already been stated that the keys can be loaded, which is a choice /Key/-/Import.../ as shown in Figure 2.7b the form of reading the content .asc (one key) or .gpg (Keyring) files relating to public and personal content separately. Analogously select /Key/-/Export.../ keys to save the file to them as necessary to make available to their associates, or to keep from losing.
Keys can be generated from a choice /Key/-/New/-/Normal | Expert | SmartCard/ under Figure 2.7b. The first option is the default configuration but described previously, while the selection /Expert/ interesting because it offers the ability to change the algorithm for generating keys and key size. One of the keys to be declared for trusting that the whole 'ring' keys to relevance (selection /Set Implicit Trust/ per D1 action on the selected key Figure 2.7b). Confidential key change is easiest to do by deleting files and repeating trustdb.gpg described the election.
Default file storage location in the directory group [Documents and Settings], in the directory that contains the directories of users and one of them is about to ring, so a lot of the 'hidden place', and it is better to move the working directory as shown in the following figure. In the present directory can be found .gpg files, small database that is the ring of public and private key and a list of sensitive key ring.
 |
| Figure 2.8 Files of ring. |
In the example in Figure rings are kept in the directory [E:\PGP\#Ring]. Rather, it is the working directory where the client software uses, and a backup of this data should be stored on a different (not the same) device.
The drop-down menu with a choice Figure 2.2 |File Manager| opens a window which method L3 or D3 and drop selected file when not type .pgp encryption is possible, and if dropped selected file is of type .pgp decryption is done if there is a matching key ring. The following Figure 2.9a shows the software allows choice of .pgp files; regarding signature verification and decryption of encrypted content.
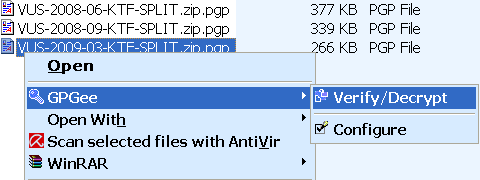
|
| Figure* 2.9 Menu for decryption / encryption of files. ( + / - ) |
With encrypted contents above actions are not necessary but the action with the opposite effect and select other types of files, as shown in Figure 2.9b shows that it is possible to do with the file regarding its protection or authorization. To sign a message that is sent is required senders private key, and to encrypt the message needed to be sent to the recipient's public key. Sender's public key of the recipient receives a personal recipient to removable media or deliver it to him by e-mail recipient as well .asc file or is the recipient's public key published on the PKS server, as described on the next page.
But given the key valid, or whether a person who represents that it has just made it? Key in this regard should be reported to an institution that plays a role of authority - Certification Authorities (CA) and we all believe, that gives CERTIFICATION. Certificate to be given assurance that the public key and the user specified in it are connected with each other, it is a confirmation that a specific key assigned to the correct person. If the sender can not confirm that he had written a message then you must trust someone else about his identity. Trust model by which to determine the authenticity of the sender can be direct, hierarchical or network. Direct model assumes knowledge of a person who has signed and before sending the message, it was agreed to use the key. Hierarchical model implies that the user group relies on superior supervisor (Trusted Introducer - CA) that oversees the supreme overseer again (meta Introducer - root CA). The network model is a mix of previously described in a way that the user chooses how to use them and use it either. In support of the model program described confidentiality is based on a database (trustdb.gpg) in which the keys are added persons / institutions which are believed (trusted keys), which fall into one of the group.
EssentialPIM software by 'Astonsoft Ltd.', which is basically 'Personal Information Manager' that lets you manage appointments, tasks, notes, contacts, password entries and email messages across multiple platforms and cloud applications, one off the best e-mail client, has these PGP capabilities integrated into their product.
|
|
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/specific/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |