System protection - Firewall |
Viruses, worms, and other programming hardest hits are from yesterday. At a time when it was not yet widespread, there is a 'program' that were passed on a self-copying the disk and which could destroy data (cancerous), or sporadic user on screen display some message or play without any damage (benign). Antivirus programs, along with samples of the virus code could fit on a single floppy. Cleaning mechanism was restricted to the computer to boot from a floppy disk and view the content. The most dangerous species were those that would destroy the records of disk partitions with FAT file system records. Formerly, while some such software product 'jump across the pond' know they take months.
Even today, the situation has not changed significantly with respect to their effect, but the patterns of spread drastically changed. Very fast Internet connection, the ability to browse, and sending e-mail, and now invasion sticks enabled the malicious programs spread rapidly (order of seconds). Programs for the protection of sophisticated computers are enormously compared to their originals. And installing the mechanisms of such malicious programs are different. On the computer 'locks' mali some code that silently installs a miracle after downloading it from the Internet without the user even noticing. The war in this domain is unremitting, the user still lag behind the ingenuity of the makers of these new works, continuously loses a step, maybe an occasional battle and win, but surely losing the war.
All categories are widespread RAT (Remote Access Trojan) programs that are essentially malignant developed that works on the principle of client-server architecture, when an attacker (naughty participant network) manages to get control of the infected computer, it installs a small program on it is often hidden under a system name, such as AVG or SVCHOST etc, allowing to use the user's computer remotely. As part of the installed server establishes a connection to the Internet is the outgoing traffic to the striker-user often does not control, and thus allowing the attacker to monitor all actions on the user's computer or use it as a proxy for an attack on a third computer. In the first case, interesting as passwords and bank accounts in the second case by a group of infected computers makes network (BOTNET) which was used in a given time can overwhelm traffic, for example a bank and thus prevent her business (DoS attack).
Luck is the antivirus industry mutual exchange data on the newly discovered 'temptations' defense and relatively quick and has some sort of sense. One of the very naughty works to the detriment of the ordinary user is a DIALER, which many Internet users 'shoved' huge bills, in a way to make a modem connection instantly switched from a local connection to the international connection. It would not be strange to have this product in their infancy ordered postal companies.
Two main reasons of computer protection are:
Today's computers have large disk resources and the user often does not notice the extent to which they filled. 'Break' on the computer may not be malicious, but the 'attacker' may, for example disk resources used as a warehouse. Theft of data and its abuse not to mention, credit card numbers, for example. Another example is the more dangerous. Let's take an example that is installed on thousands of computers 'gadget' that on the day of ' D ' attacking e-mail server, or something else of a bank, to the extent that it will not be able to communicate with their customers. The real culprit is unknown, and be responsible to the owner of the computer and for his negligence can suffer the consequences.
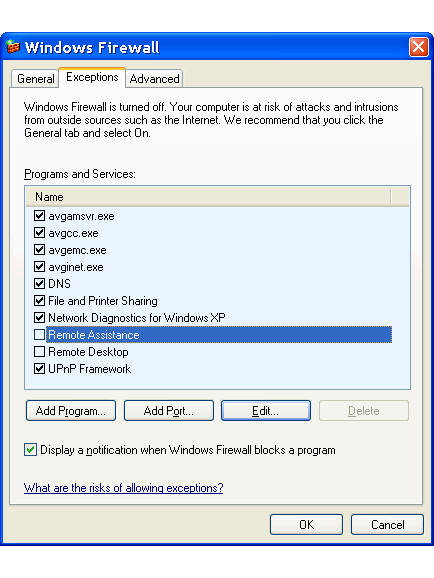
One of the program works to protect the system from unauthorized use of a firewall, which is with SP2 (Service Pack 2) implemented in the operating system and offers basic protection functions. Will not allow any inbound traffic initiated from the outside that is not approved, but allows most outgoing traffic. However, this is somewhat adjustable. When installing the OS firewall will set all 'acceptable' software that may communicate with the Internet. What we want to disable just turns off or completely erase as shown in the next picture. Individual records can also be deleted.
|
| Figure* 4.4.41 Configure Firewall. ( + / - ) |
With pictures 4.4.41a shows that the permissible communications antivirus program while resource sharing and remote access is disabled. But that's not all there is to do. The upper part of the image 4.4.41b shows how to get the window when selecting |Edit...| if labeled choices |File and Printer Sharing| where to be seen to stand for a port's, and for which the network is valid and changes network setting can make a choice |Change scope...| when you get the lower part of the picture 4.4.41b. It may be instead of the whole network or subnet defined only individual computers. Confirmation OK means that accept entered. There is a lot of options for each program offers support for the election is different. You need to know what each element means, otherwise it is not advisable to change.
Useful to include the firewall alert the user that a program wants to support 'out', so that it could decide whether to allow or not. This little peculiarity allows the user to more easily find his way and to have better control. As soon as some weird program grants wishes to contact outside of the network, it is possible that your computer is compromised.
A very important element of the anti-virus protection in general. But the task is not given only reading mail, but also an overview of all the files that are running, as content downloaded or uploaded web content and compares them with the samples in the database antivirus program. If it is found in a detrimental offers a choice of what to do. Because of the diversity of functions specified program support is often offered as an 'INTERNET SECURITY' solution, which is the main feature that must be followed to pay their monthly subscriptions in order to safeguard the client software successfully worked. For occasional users of this solution is expensive, and some companies allow users to make free less powerful versions of the same software (usually called LITE), in order to placate customers with time to decide on the purchase of their professional products.
When you buy a set of reputable companies, such as the motherboard, or the preinstalled version of the OS on the laptop, it usually gets the full version of a manufacturer with a lengthy duration, usually a little older than the currently available, but effective. Solution is acceptable as long as the subscription. It is unfortunate that these programs are entering 'deep' in the OS, and sometimes it is difficult to uninstall and install new versions of the same or any other products is almost impossible.
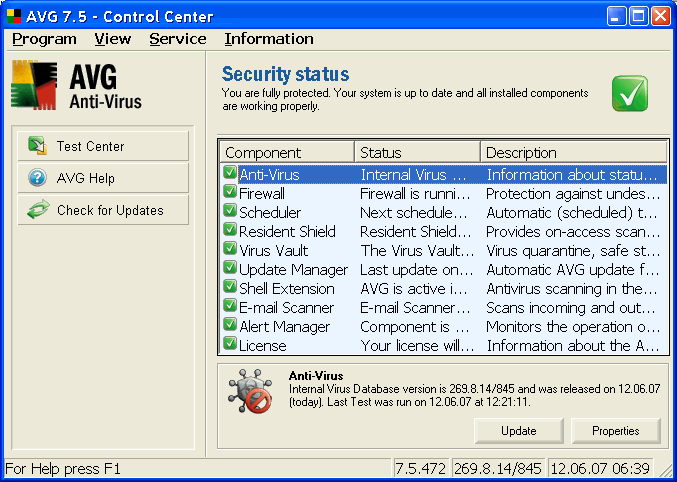
The following Figure shows what it should contain an 'INTERNET SECURITY' products: anti-virus detection, advanced firewall that will replace the existing Windows XP system, organizer with certain times of the system and download new definitions of safety from the manufacturer, available at all times a protective shield that will detect 'Attack', storage and isolation of infected files (which could be from a system that is good to know the 'hand' repair), a system for the automatic implementation of the downloads and more.
|
| Figure 4.4.42 INTERNET SECURITY program support and its components. |
The specified version of the company GRISOFT weakened in free version, which includes only part of the above, but more than that it works well, it can be downloaded at the address contains a link: AVG Anti-Virus Free, AVG Anti-Spyware Free and AVG Anti-Rootkit Free. Reliable software of this kind is the free version of Comodo Internet Security. Basically, the software components that support the protection features consist of the following software tools and tasks:
Free software will of course be used in the absence of commercial protection, but it should be keep in mind that in relation to professional opportunities mostly weaker and serve as advertising (hook) to buy a professional program support. But what is most important is: PROPER USE YOUR HEAD. Mandatory checks for new programs that run in the OS, disabling 'autorun' or autostart program support with stick or optical media, not allow ActiveX controls and licenses to run scripts on the web pages, except for those necessary as the 'Microsoft Update', 'Adobe Flash', 'Java Runtime Environment' and the like.
When choosing a system of care to one peculiarity should be noted: OS should never be left in a state with no protection when supplementing base protection system, even at the cost of the necessary reboot of the computer. Specifically not happen to be when upgrading databases via the Internet protection system for a moment stop and release all approaches. Such software solutions should be avoided. Despite all the above, and still is the first defense against attacks NAT (Network Address Translation), carefully planned and regularly monitored network scheme.
SUMMARY:
To facilitate the retrieval of shared network resources in the Firewall option ||Exsceptions||-|File and Printer Sharing| should be included. To improve access and advertising of shared resources in the network is useful for the above option to define one as a shared directory (share) on which it will exercise the right of access by all members of the selected subnet or IP address of your computer to the firewall know who to miss (choice ||Exceptions||-|File and Printer Sharing|-|Edit|-|Change Scope...|). It is useful to all of the services that are running while adjusting the options set to 'Auto' (for example, Network Connections, COM+ and some other) in order to advance the network and identifying resources in a PC. Namely, how to set connection settings are kept for several days, during extended periods computers can follow unavailability message, which will be avoided if these services independently engage and 'listened' environment. Stated enough when all computers are the same family (for example, XP Professional), but if you want to connect disparate systems (Windows XP and Windows 2K or Windows 98), the computer that provides resources to be opened with the same user name and password that the user has to another computer that is running, or the computer seeks resources.
Firewall and anti-virus programs are not sufficient, if the user does not care about the computer regularly 'PATCH' with periodic revision of parts of the operating system or software (hotfix), which is the Windows XP OS automatically. The user of this must constantly take care. No vendor software or operating system support and protect themselves. If during this process determines that the computer is running a pirated copy of OS or software can to not protect their product or suspend their patching them unusable.
What is the best way to protect? If something important and serious work, this computer must be independent and not connected to the Internet or a network that does not have this connection. This in itself is not enough. No passing laptops from home or removal of the same house where they can restore infected and do damage in the local area network that is not connected anywhere. The following story was on TV: Dad borrowed to his son a laptop and when tomorrow came to work in a nuclear power station, soon half the day part of New Yorker had no electricity. Statistics indicate that more than half of the damage caused by recklessness within a company or institution in relation to the direct damage from the Internet. All of the above means: To introduce to the company or institution security policy that describes who does what the gatekeepers to the system engineers, and policy of acceptable behavior that defines what is permissible and what is not. Safety is an aspect that is no longer in any way can not be avoided.
A small note at the end. Windows server has no firewall implemented as XP system because it is not needed. Everything is forbidden by default until otherwise determined by the administrator. Best protected computer is a computer that is not connected to the network. Not so long ago it was common practice that the major systems, only a computer administrator can 'get', but what is not in the network with others. For the testing of some computer programs served another separate computer while it should not be 'proven'. However, all of the protections are in vain if 'Dad' brings his laptop home and gave him 'Junior' to have a little play with. When 'Dad' return to work as questionable with a notebook 'donated'. Do you use Google? Find out how one afternoon, part of New York remained without power because they are a nuclear power plant reactors had to 'manually shut down' after it's over they lost control.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |