4.4.5. Registry |
Registry is a large complex structure is essential for the correct operation of the operating system. It has already been mentioned in Chapter 4.3 for Windows 9X OS. You need a good understanding of its composition and organization, because the use of the editor (regedit) is the same as opening a Pandora's box. Everything that whatever is in the computer, the names and parameters of hardware and software, configuration files and records still recorded in this unique base, and for content with no certain knowledge of what to do is very critical. All of these records an operating system that could successfully work with hardware and software.
All versions of Windows OS with a powerful editor to view and edit this information - REGEDIT (Microsoft Registry Editor), which is run by entering the keywords in the choice of {START}-{Run...}.
 |
|
| Figure 4.4.43 Call registry editor. |
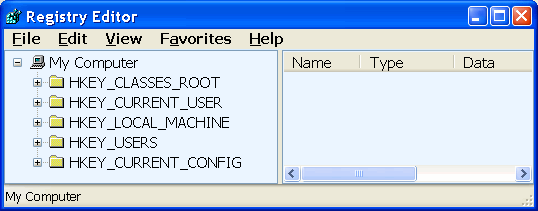
Followed by frame of editor, which allows you to view and modify the contents into five groups, called HivesKey (swarm of keys), shown in the following Figure:
|
| Figure 4.4.44 The basic composition of Windows system registry. |
Groups shown in the Figure represent the following:
The data shown in the image is located in the directory-map-folder [Windows\System32\Config] to the file with the name DEFAULT, SAM, SECURITY, SOFTWARE, SYSTEM and USERDIFF. In this directory there is a directory [systemprofile]. But that's not all. Each user has an environment that is kept in the directory [Documents and Settings\CREATED_USER], where in addition to the folders in which they are kept local user preferences almost every software (Word, IE, Windows Media Player ...), and the files are NTUSER.DAT and NTUSER.INI, where bills that amend the records from the above folder or set them according to user needs.
The function of individual files is different:
Each of the files 'belongs' her .LOG file in which records all system activity and user. Most tracks have a group SOFTWARE, then in groups SYSTEM and NTuser.dat. Other groups have ten times less voluminous records.
Each of the keys is a set of folders in which the names of the keys where values can be given as text, binary, hexadecimal or the decade record. So, without knowing the numeric system until now, all these can not be used. These are:
Data from the registry can be made or entered using the file type file_name.REG which is very handy for storing information about user accounts, site address or a list of TV channels and the like. Example two records displayed on.
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\Internet Account Manager\Accounts]
"AssociatedID"=hex:36,dc,1e,52,53,98,db,45,88,b1,99,f7,d8,cf,28,34
"PreConfigVer"=dword:00000004
"PreConfigVerNTDS"=dword:00000001
"ConnectionSettingsMigrated"=dword:00000001
[HKEY_CURRENT_USER\Software\Microsoft\Internet Account Manager\Accounts\00000001]
"Account Name"="T-Com"
"Connection Type"=dword:00000003
"POP3 Server"="pop.t-com.hr"
"POP3 User Name"="drago"
"POP3 Password2"=hex:01,02, .......
"POP3 Use Sicily"=dword:00000000
"POP3 Prompt for Password"=dword:00000000
"SMTP Server"="mail.t-com.hr"
.
.
.
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\WAB\WAB4\Wab File Name]
@="E:\\mail\\drago\\addresses\\Drago.wab"
The first of these records relating to accounts and others indicates that the address located on the hard drive [E:] in the [mail\drago\addresses] in the file Drago.wab. So that when reinstalling would not again be setting all of this, important user keys are stored (Export...) in the corresponding .REG file, and after a new installation enter (Import...) using the menu editor registry.
The basically for these bases should not be touched. It is good when the system configures and installs all the software for BACKUP of the entire operating system, not just the registry. In fact, when you install new software or support some of the new probe of software or something, all duly recorded in the registry, but the 'unload', and numerous files in the operating system folder. Just delete (uninstall) program support does not lead to a complete and proper cleaning the registry, especially to delete files. Thus, over time, build up a lot of 'excess' that is not easily removed. The most effective solution is the return of 'pure' backup, though for 'cleaning' registry there are many tools, most of which are commercial. But they need to learn is to do it and they know to delete something you should not. Good tools must include a mechanism for backup and the ability to define the base of keys that can not be touched. The basically of tools should check:
This last paragraph may contain a lot of unreliable data due to deletion of files or moving them, which can significantly slow down the system if it is necessary to look for something that does not exist.
But there are times when you need to intervene. For example, if you replace the network card but not before its removal erases all settings (IP address) and uninstalled the drivers, installed the new card will not be able to configure the same IP address is the same as 'busy'. Before changing the assembly to uninstall and delete all of its existing settings. Particular problem occurs when the network card failure, the hardware is not listed, there's nothing to uninstall, and all records in the registry. Then be 'on hand' to delete everything on the faulty network card related and then insert a new one. We should therefore be careful not to erase something you did not need, which can easily happen if, for example networking and graphics cards of the same manufacturer, so records for both starts with the same name.
Register and his records a single point of failure (One point of failer). Damage to the registry can leave the system in a stationary state, in extreme situations and irreversible condition and in need of reinstalling Windows. User settings usually remain in the registry for two reasons: the user can be on a Windows domain with a server profile, where the setting move with the user from computer to computer. Deleting applications on one computer, does not mean that the user wishes to use the same application on another computer in the domain. Often applications are written so that you do not care to clean the data after deletion. Validating entries in the registry and deleting those that are found to be guilty may contribute to the stability and speed of your computer. As the volume of data over time in the registry increases and reaches a considerable size, the result is slower to start the operating system and the instability in the operation.
To end the need to write about something commendable register; computer environment is separate from user configuration, and user settings easily transferred from computer to computer in a network environment. Group Policy allows administrators on a Windows computer network to centrally manage applications and permits. There is a possibility of adjusting the content registry for all the computers in the network, and the impact on virtually every program installed that permit a user or program must do. It is easily stored in the backup. Some parts of the registry can be saved in .REG files are plain text files that can be edited with any text editor.
SUMMARY:
Registry is a prodigy. Remembers everything like a sponge and never forgets anything, which practically means that the time saved by running the installation files from the directory [Temp], whose content is periodically deleted manually or automatically via a script. When the boot records of this type, especially if they are in part related to the initial settings of the system, can lead to a significant slowdown of the system. So the registry should take care. A variety of tools to set, from commercial solely for this purpose, integrated tools for the protection and maintenance (like 'Norton SystemWorks') to free. A good tool should have as many options available such as the distinction really unnecessary and obsolete entries from potentially dangerous to delete records and records that can not be identified. With these characteristics, the possibility of tagging individual records as correct (that is in the following table are not displayed), backing up the deleted records as well as backing up the entire registry, one such tool are complete.
It has been said that in the base register write everything for the computer and user. This can lead to big problems if it installs and uninstalls of software too. Computer operation becomes unstable and is therefore necessary to take measures to facilitate the reconstruction of data stored somewhere. These are the BACKUP and RESTORE POINT.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |