Users and Devices |
User created in the installation process belongs to the group of system administrators. User 'Adminstrator' is not created by default and is inactive. If users 'Adminstrator' making and enabling passwords, previously created by the user query confirmed by the system automatically loses administrative privileges (change group), and if he wants to re-lock the user 'Adminstrator', prior to another user should allow administrator rights to avoid blocking access to the system as an administrator.
All created users on the system have their data in the [Users], which contains the following directories and files:
Each of these folders has its subfolders and files that describe each of these users. How does that protect all data from the user, if they are not relocated outside the disc with the operating system, the amount of data in them can grow enormously because of the temporary files Internet Explorer, mailbox with a multitude of attachments, cookies and various types of temporary files that are hidden in a happy subfolder [AppData\Local] that every user. Thus there remain a multitude of useless records created during installation of software or to work with ZIP files, reading PDF documents and similar programs [Temp] subfolder in the [Local] used for anything and use anything not automatically deleted. Hygiene computers, especially if it uses more than one user, it is not easy to implement, and even harder to restore the system in proper condition, if for some reason the damage. The vast amount of data collected during the operation of the user folders and difficulty of recovery in the event of damage, one of the reasons why a significant and most used folders user moves to another partition.
Users of the system according to the following picture:
According to the example in Figures 4.5.31a and 4.5.31b shows that the user 'Administrator' is disabled by default and does not set a password.
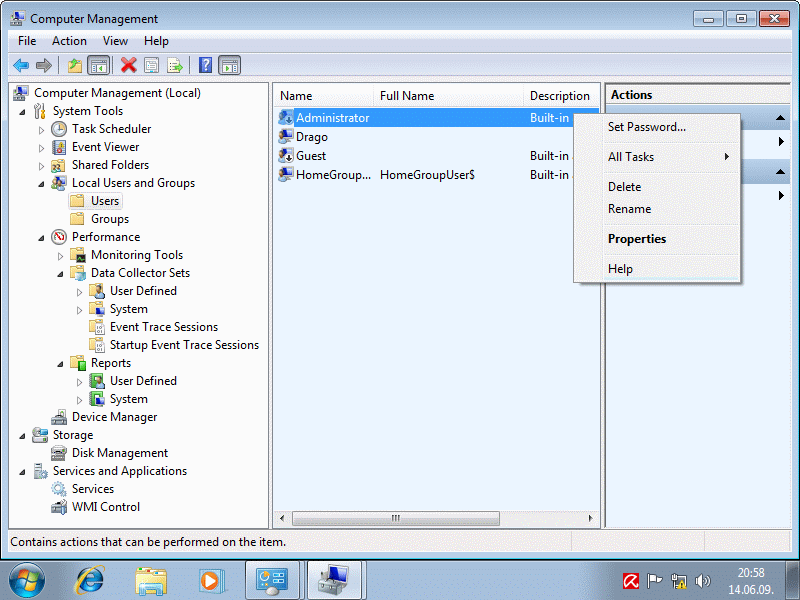
|
| Figure** 4.5.31 Users of operating system and their groups. ( + / - ) |
In addition to the above users can create and 'users' who do not have their own folders, which are defined in the {Start}-{Control Panel}-/Administrative Tools/-/Computer Management/-/Local Users and Groups/-/Users/. These are the users who access grows mainly through the network. Folders should be created on the basis of the [Default] templates when users are directly applied to the system. All users are created through an option in the /Local Users and Groups/-/Groups/ rights on the system by placing them in one of the groups is shown in Figure 4.5.31c. Using a combination of the <CTRL> + <ALT> + <DEL> in 'Windows Task Manager' in the choice of ||Processes|| will appear with the user (for example Drago) and the user SYSTEM, LOCAL SERVICE and NETWORK SERVICE. Thus it can be seen by anyone who start a service or process is responsible.
Each of the users can change group membership choice |Add...| In Figure 4.5.31b. Group 'Administrators' has the greatest authority, or rather all the powers over the system, while others have limitations in terms of function. Possible through the settings of the policy to determine some other profile. When creating a user in the default installation procedure is just a first initial user created member administrators group, but not in full all administrative privileges by default excluded as 'Administrator'. This is reflected in the manner used by the UAC mechanism. This is reflected in the manner used by the UAC mechanism. For each installation of software whose penetration into the system UAC asks for permission to ordinary administrators (users), while these queries as an application on the system as user 'Administrator' no. Of course the user 'Administrator' should be previously enabled. If the user himself revoke administrative rights over them, you can not return, except by another user who is a member of the Administrators group. Therefore, the system should be open to at least one active administrator, how to avoid the situation that the system becomes unavailable for any changes.
A quick way to restrict the user does not have administrative rights to the L1 actions of users on the icon in the initial menu, 'Bob Dalton' as shown in Figure 4.5.2b, and then opens the window shown in Figure 4.5.32a. The advertised window is selected |Change your account type| and obtain the image 4.5.32b.
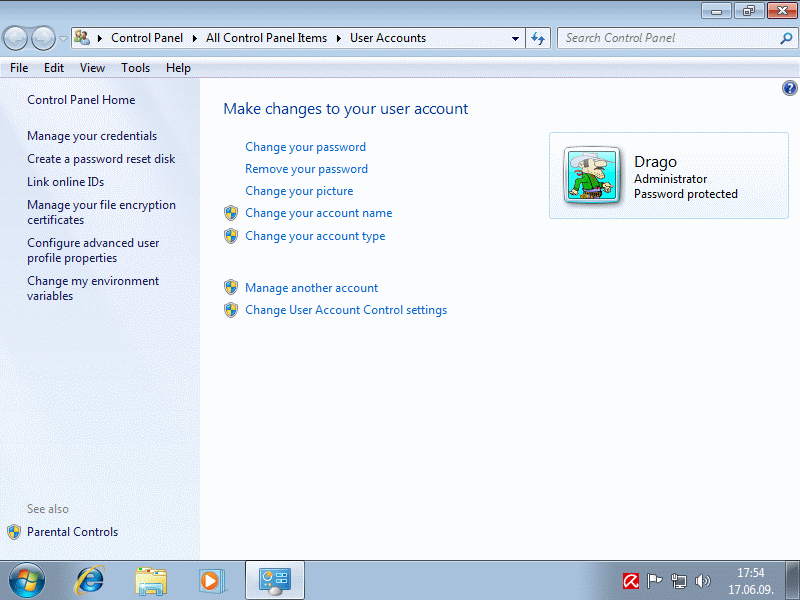
|
| Figure* 4.5.32 Characteristics of users. ( + / - ) |
Choice |Standard| abolishes multitude of rights to operate the system, change the IP address or some kind of software installation, for example, and only the permissions can be changed by the administrator. According to this figure this change is not possible because the system there is still an active administrator. Procedure described above is not the only thing you can do on the system. Meticulous users will use additional tools such as GPEDIT.MSC, by typing this command in the requested form the main menu, from which follows the display as shown in Figure 4.5.46c. MSC tools are a subset of the MMC (Microsoft Management Console) program support. A variety description is very similar to XP system described in the previous chapter.
Another important novelty is a quick overview of the possibilities of connected devices. The example in the following figure shows how the system detects VPC computer it is installed on, and offers a menu that allows actions on the device as possible.
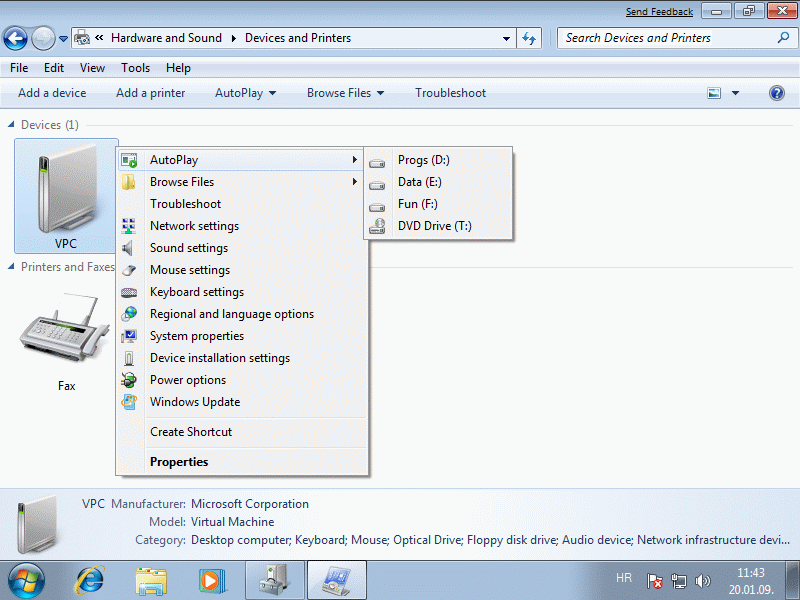
|
| Figure* 4.5.33 Characteristics of devices. ( + / - ) |
In the bottom of the window changes automatically further description that the device belongs. Stated has great significance in the era of the growing number of devices connected to the computer via the USB interface or via Bluetooth wireless, which the above image is not seen because VPC does not know recognize these devices. If the device is not in the list is added to the selection /Add a device/, followed by: the search for new devices and the requirement to install the driver, if the device is found, or device to be added from a list provided. True, the picture 4.5.33b does not reflect the actual state of a virtual machine, because it can not recognize directly USB devices or monitor, but belongs to installing the operating system on the 'real' computer.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |