General Settingss of the System |
System
Initial System Setup window shown in Figure 4.5.25a. Initial System Setup window shown in Figure shows the General Settingss window computer system (processor type and the amount of RAM), the general features of the operating system (type and edition) and basic networking features (the computer name and workgroup). The menu on the left offers additional setting options, a basic setup by the selection /Change settings/ where it is possible to change the computer name and affiliation workgroup (or domain) according to Figure 4.5.20c. At the same time, by a request for a reboot in order to properly accept the change.
The most important choice on the left side of the window is /DeviceManager/, which is a working window shown in Figure 4.5.11. All devices in it must have the correct drivers in order to achieve an effective link between the hardware and the operating system. If the list of devices, some of them associated with a circle with a QUESTION mark means that the device is not assigned to one driver, and if it is associated with a circle with an EXCLAMATION point that means that the driver associated with the device (pre-installed in the system) is not correct. In both cases, the deficiencies must be removed.
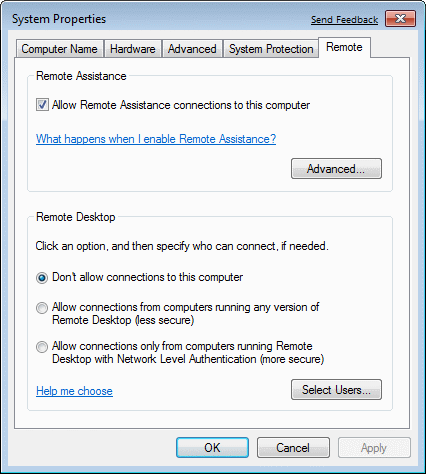
Settings relating to the remote computer control and overall system protection, selection /Remote settings/ and /System protection/, showing the next two pictures. Remote control has two components. If it is on choice |Remote Assistance| basically allows another computer in the network and remote user that can access the system through the firewall, which undermines security. Developed that allows these drives to the remote user's computer by choosing from the main menu {All programs}-{Accessories}-{Remote Desktop Connection} where the following form to enter the computer name and its capture by request USER_NAME and PASSWORD, as shown Figure 4.5.41c showing the reach of one of the computers in the network with the Windows XP operating system. Thus, the remote user has a computer that monitors have access, and must have their USER_NAME. In order to achieve remote access to choice |Remote Desktop| should be allowed or available at the two levels of security with the choice |Select Users...| need to choose which user on the system has the right to access. It is very dangerous, therefore user 'Adminstrator' left unprotected without a password and give it to remotely access. Indeed, the user 'Administrator' for security needs to change the name (Figure 4.5.46c).
|
|
|
| |
|
| |
| Figure** 4.5.41 Remote access / System protection. ( + / - ) |
/System protection/ allows each partition to determine whether it is possible to create a picture of the current situation, which is then stored in a hidden directory [System Volume Information]. Basically make the save system state through election |System Restore...| where is not saved status for a user's data (images, for example), but changes regarding drivers and the like. The procedure is similar to the XP system, and is described in more detail in a separate chapter.
Advanced settings adjustments are possible through choice /Advanced System Settings/ that is already displayed in Figure 4.5.20. Settings can be changed only by 'Administrator', and most importantly for the user's virtual memory setup and environment variables.
Windows Update
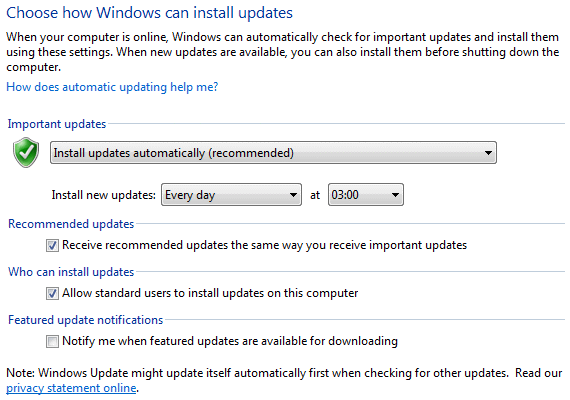
A useful feature is the automatic checking for patches on the Microsoft servers, which can be set in a way that presents the user. If there is some kind of an upgrade, the user of this report through the system menu. It can be set for automatic update or disable the first choice of the following picture settings.
|
| Figure 4.5.42 Set-up automatic updates. |
Setting times during the night is very useful distinction, if the computer does not shut down. with respect to the quality of PC hardware, it is not advisable to leave it for days (though home computer is not a server) and the time of this update should be set to perform when working on the computer at least, time brunch, for example.
Power Options
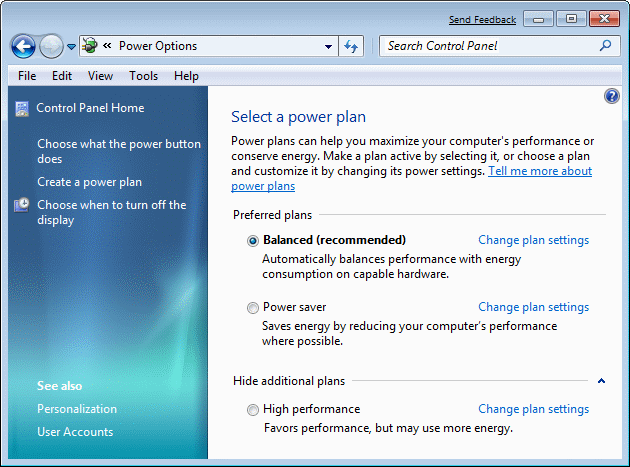
The option of saving settings to the individual circuits computer after some time off, or that the computer is completely off due to inactivity.
|
| Figure* 4.5.43 Setting savings. ( + / - ) |
These adjustments make sense with regard to savings in an environment with a huge number of computers, but in the household budget items do not contribute because they have other costs far higher. Besides devices suffer the most precisely when connecting or disconnecting, and the author of these lines has this peculiarity is not used. And much can be set indicates selection /Change advanced power settings/ shown in Figure 4.5.43b.
Backup and Restore
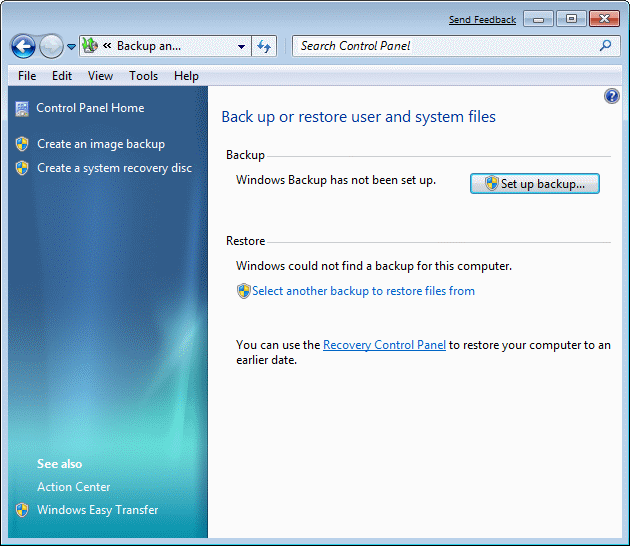
Basically 'Backup' is the storage of data from the disk partitions, and 'Restore' mechanism to store the state of the system without the user's data in a given time. Choice with images /Create an image backup/ according to the following set of image-storage system partition to another partition, and program support automatically selects the most appropriate site. Even warns that it is not a good backup on the same physical disk.
|
| Figure** 4.5.44 Enable Backup / OS image creation. ( + / - ) |
Although [Temp] directory on the partition [F:], it was proposed to be listed partition backup, which means that the specified directory is not considered problematic for backup. Backup data deals with a separate chapter. 'Backup' and 'Restore' mechanism have a lot of features like the Windows XP operating system. Of course, for this purpose can be used and software tools from other manufacturers, such as 'Symantec Ghost Solution Suite - v2.5.1' software described in the chapter of the Windows XP operating system, although it is also applicable to other Windows platforms, including for Windows 7 and Windows 8.
BitLocker Drive Encryption
Security mechanism regarding encryption of data on disk, so that they would not be able to abuse another person. The following figure shows that each of the partitions on the disks can independently provide this protection.
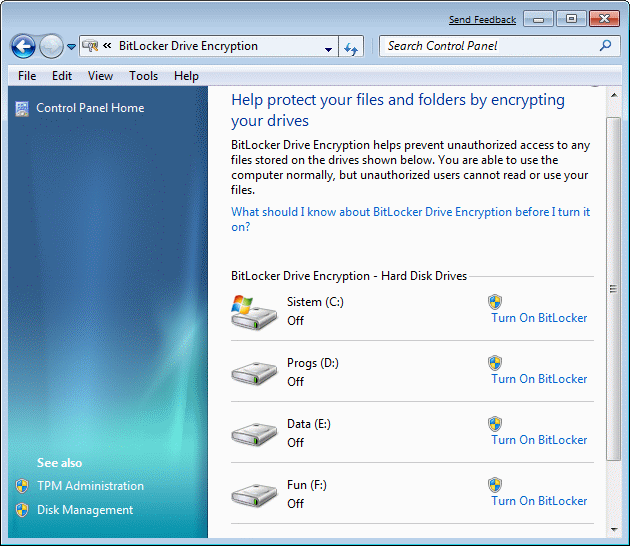
|
| Figure 4.5.45 Setting drive encryption. |
This peculiarity should be immediately included in the partition which provides storage of user data. Then it can happen that after you take the computer out of service to the public 'leak' some of your video or image intimate performances.
Device Manager
A method of managing devices larger preceding description of the picture 4.5.11. A method of managing devices larger preceding description of the picture. The devices, about the questionnaires and exclamation points, but was told at the beginning of this page. Short note, the new driver is not necessarily better than the existing one. We should always carefully examine what bring change, and unless it's something important you should not rush to upgrade the driver and it is good to wait a while and keep track of forums that relate to the product and its drivers.
In any case of before you upgrade to the new driver needs to define a point of return (RESTORE POINT), to be returned to its previous state, if you install new drivers go wrong. The operating system will be possible when installing a new driver or rollback written condition execute 'restart'. The process is essentially a very simple and it should be used on every system upgrade, any drivers or software.
Administrative Tools
Computer administrative tools are a set of programs essential to successful adjustment and monitoring of the operating system. Access to the tools already described in Figures 4.5.18. In the previous sections explain how to work with devices and users, but is not listed very important part - the event log on the system, as shown below.
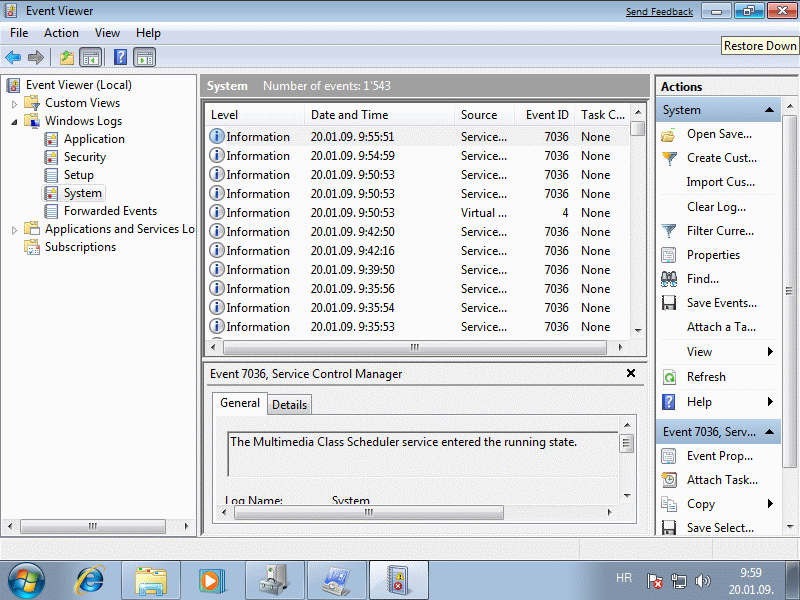
|
| Figure** 4.5.46 Events / Service / System policies. ( + / - ) |
From these records can be accurately established that irregularities occurred in the system, and thus help the user to locate the possible cause of adversity. Round icon with the letter ' i ' indicates that an action was a success, while in case of of malfunction icon to change the format and displayed as a warning or an error, similar to Figure 4.4.55 describes. As shown in Figure 4.5.46b possible to monitor the status of individual services or make additional adjustments to the image security 4.5.46c. For computers in the network, where it is essential constant connection (shared printer), after adjusting the printer and the rights of individual users on it, all services that are activated at the same time should be set to 'Automatic' as the connection at the next turn on your computer should not be lost. Always first involves a computer that provides a service and then only one that is used.
Feedback
During the development of a complex product such as an operating system, with all this attention of developers, errors are always present. Therefore, the manufacturer provides interested users to use free development version for a fixed period of time, so that, with their cooperation eliminate as many defects before the final version of the product offers.
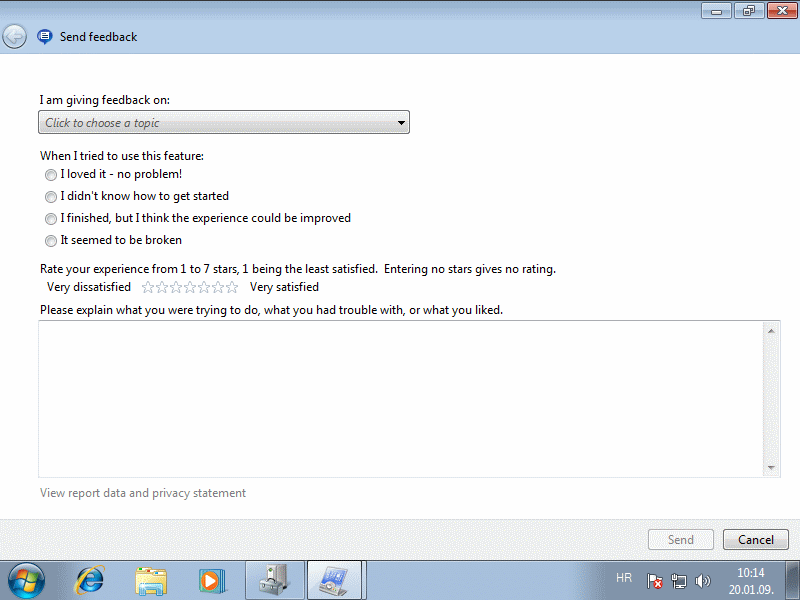
|
| Figure 4.5.47 Sending a message to Microsoft. |
So in this case this 'Beta' version is valid until 01.08.2009. year, and adopted as an ISO file from the Microsoft server, which is made from the installation DVD. Manufacturer's definitely interested in feedback from the user, so that with every action related to this peculiarity in the form shown in Figure could describe the possible problem or defect. So who likes ... The 'RC' version of the operating system and further versions does not have these characteristics. In almost every window in the upper right corner of the clip that has led to the 'Feedback' window. The images in these facilities that do not have the links obtained from the review of belonging 'RC' version of the operating system.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |