System and Security |
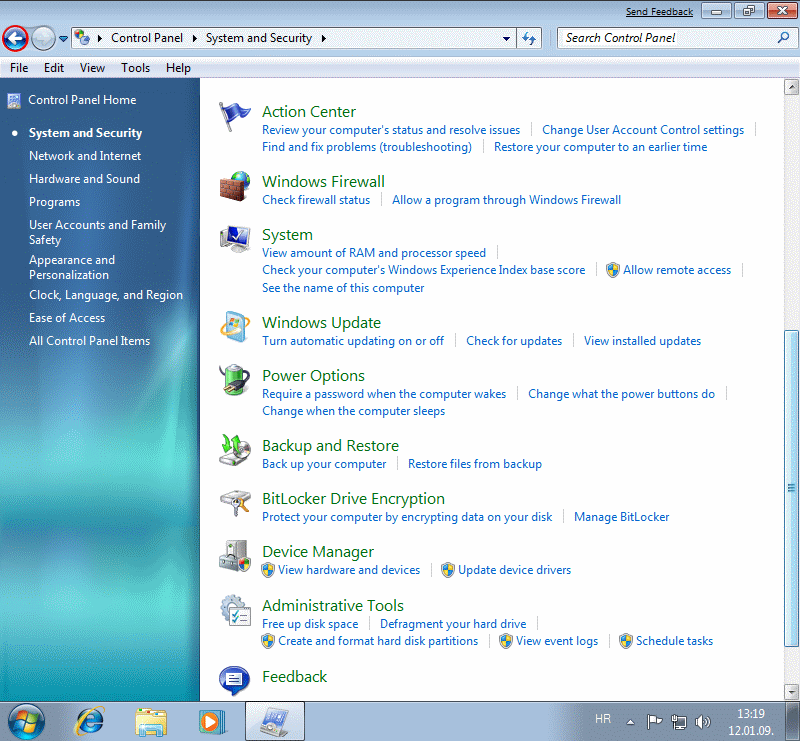
Security is one of the most important properties of operating systems of today. Almost continuous connection to the Internet and more widespread and more diverse forms of computer abuse is one of the major problems of today's generation of PC computers, and the battle against intruders prompts the user for a growing understanding of the ways of protection. It is not surprising that this particular group has the most of items to be set. The following figure represents the composition of the initial presentation in this group setting, and as a larger set, blue button with an arrow to the left and is mapped to the link of the page to descriptions of system configurations.
|
| Figure 4.5.35 System set-up and security. |
Rectangular form, circled in red in Figure 4.5.18, along with round button labeled with arrows drawn to 'FORWARD' and 'BACK' and form a line to search for navigation menu (hereafter LNI) window. Previous and next Figure shows clearly how the two are in regular navigation menu changes depending on which window is active. Names in the LNI are also links in the operating system to the facilities that belong to the title. The following is a description of certain elements of this window.
Action center
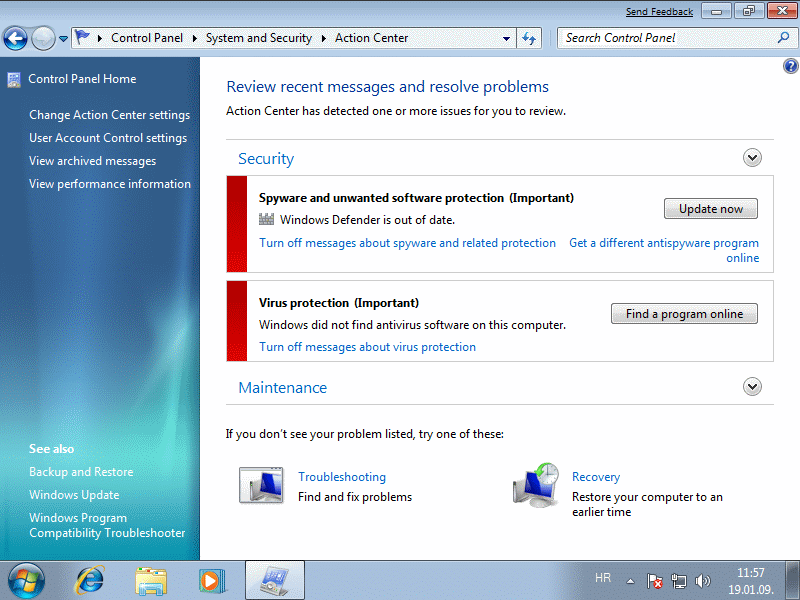
Action Center is developed that controls all aspects of security systems and the established status automatically makes corrections regarding the removal of uncertainty or user is warned that they must take some action to show next Figure.
|
| Figure 4.5.36 Setting the security and maintenance. |
In Figure above shows the first message a user to a system for monitoring the possible presence of malicious applications like 'spyware', intended to intercept communications or partially take control of the computer without the user's knowledge, there is no date definitions regarding detecting the presence of these malicious creations. Program support 'Windows Defender' is able to make itself update and browse system files and if everything is okay alert window automatically disappears. 'Windows Defender' in their options should not be adjusted unless a special time automatic browsing. Browsing time should be set to start at the point when the computer is the least used, during brunch, for example.
The second message is much more important and indicates that the system is not installed antivirus software. Windows 7 operating system does not have built-in support for this type of program. There are very different, and sufficient for the average user is some free version, which in any case can not offer quality commercial solutions. Which solution to choose? Should carefully read the reviews of professional journals and how to choose the most appropriate solution. If the user is connected to the internal over NAT (some SOHO device), the existing firewall system and some kind of free anti-virus protection is sufficient if the sites visited that by their nature do not spread malicious content. And this message will disappear if the antivirus software is installed and grant date. Verification system to infection should be adjusted in the options of the program support by criteria similar to the previous case.
It should be borne in mind that the Internet is not the only possible source of infection. Mobile USB devices, like 'Memory Stick', all the more dangerous deliverer malicious programs, largely due to negligence and ignorance of most users home computer systems that are not under the control of some professional services. Internet service providers (ISP), their ignorance is basically not interested, and there is no penalty regarding possible abuses of computer systems.
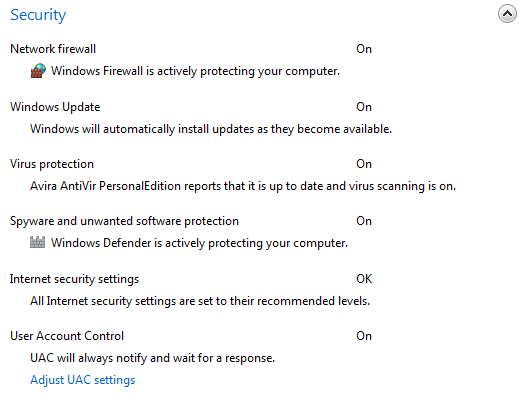
What does all this center monitors shows the next Figure 4.5.37a, and you can see that all the activities of the individual elements performed correctly by default options. Figure 4.5.37b continuation Figure 4.5.37a.
|
| Figure* 4.5.37 Security settings and maintenance. ( + / - ) |
In Figure 4.5.37a shows hinge that activates UAC monitoring window, described below, and below in Figure 4.5.37b very important item 'Windows Backup' is not defined. Regardless of whether the Windows tools or other commercial tools, backup SYSTEM and DATA needs regular work, especially in front of some changes or system upgrades. Much easier and faster to return the correct image of the system partition is it simply 'overwrite' damaged or infected system partition rather than correcting the wrong thing installed or 'clean' infected. The importance of protecting the user's data themselves do not even need to speak. If the user's data is of great importance to keep them in different places, and NAS system with RAID array then is necessity. Because of its importance this part is processed in one of the following separate chapters. How the UAC set shown in Figure 4.5.37, the chosen {Start}-{Control Panel}-/System and Security/-/Action Center/-/User Account Control settings/ (Beta and RC distribution), wherein last choice made on the left side of the window 'Action Center, shown in Figure 4.5.36.
Windows Firewall
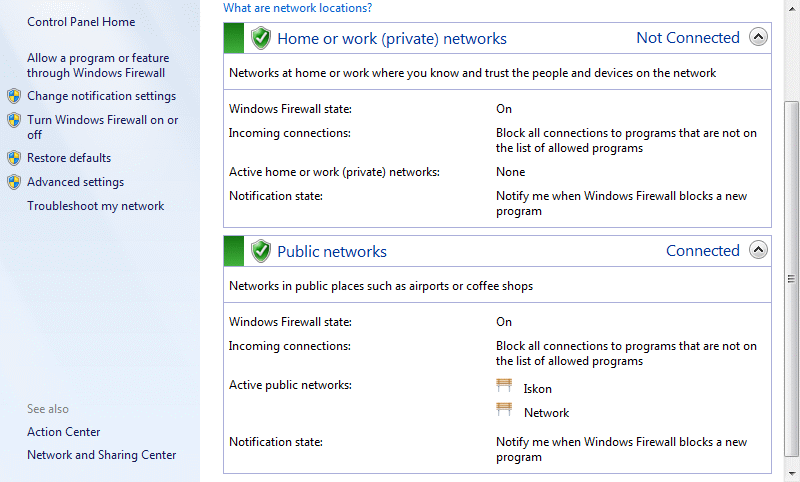
Windows Firewall was introduced in Windows XP system. Before SP2 was turned off by default, and with SP2 has received additional improvements as well as an option that comes standard with the need for increased security increasingly more frequent malicious activity according to users. In the version of Windows 7 this part of the operating system has significantly improved in the supervision and incoming traffic. The following figure shows how the firewall functions are separated into two separate monitoring system: home and business networks and public networks.
|
| Figure 4.5.38 Network locations and protection about them. |
Home and business networks are usually better controlled, while the notion of a public network mess for themselves. The notebook can be wirelessly connected to anything and there is a need really great caution. Because of its complexity, this part was processed separately in a later chapter.
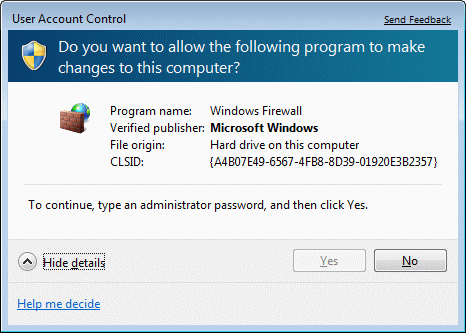
That a normal user would not notice without changing system settings cares UAC (User Account Control), which the ordinary user, who is not in the Administrators group, seeks to type an administrator password if you want to make some changes in the parameters and system settings.
|
|
| Figure* 4.5.39 UAC in action / Set-up UAC. ( + / - ) |
UAC does not answer users 'Administrator'. If the user is 'Administrator' activated, changing the group initially created users in the 'Users'. So lost 'Administrator' rights, and if then the system login as user 'Administrator', either the current user or logout action 'Switch User' as shown in Figure 4.5.14b will make his profile (created files and directories) that do had not been present. Care should be as user 'Administrator' does not prevent the same and that some of the previously active users does not allow administrator rights, because it will be unable to login to the UAC. System becomes blocked for any changes.
UAC is set choice {Start}-{Control Panel}-/System and Security/-/Action Center/-/Change User Account Control settings/ (RTM distribution) on the left side of the window 'Action Center', and selecting one of the various levels monitoring as shown in Figure 4.5.39b. From a user depends on what level will use. As essentially prevents unauthorized and unverified installations, levels of well-matched with the place of work, at home and in firms where control of access to the network a little more give in, and when working in the public network, set the most stringent level. From the example in the figure, the firewall 'does not like' modifications to its settings.
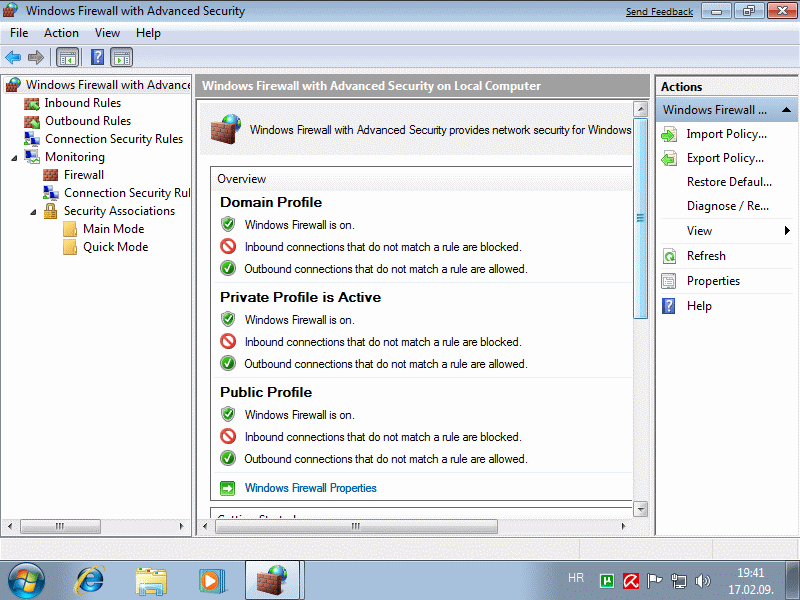
What all firewall can shown below, and a complete description of the firewall is in a separate Chapter 4.5.6.
|
| Figure* 4.5.40 Firewall settings. ( + / - ) |
It should be noted the ability to define rules for incoming and outgoing traffic, and that the safety performance settings - POLICIES can save (export) or policy settings already saved use (import). This means that they can be stored for rapid change various settings of the firewall, which is a great relief in respect of adjustments to work in private and public network. But, as has already been said about this in a separate chapter.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |