4.5.6. System protection - Firewall |
The general task of a firewall is to protect your PC against attacks via the network. But also provides secure communication between two computers that would seek to ensure the identification and protection of data. Firewall this operating system has an integrated advanced protection technology, which in addition to the usual security technologies marking off aid program to access Internet resources (such as the prohibition of exit), used IPSec (Internet Protocol Security), which is part of the TCP / IP stack for security (AH, ESP, TLS) in terms of identifying the encryption. Due to the complexity of managing firewall functions, its use possible in two ways:
With integrated firewall protection technique is using a sending complete information about the connection status and data (stateful) participants in the connections that will add value to data during their processing through the layers of the OSI model. Monitor and filter all packets for IPv4 and IPv6 protocol version. Under filtering is meant to permit or block network traffic according to predefined rules. Internet traffic is defined as:
In Figure 4.5.38 shows that were prepared defaults firewall for home and public network, and Figure 4.5.40 shows that the set of rules defined as the monitors incoming and outgoing traffic. Default incoming traffic is blocked unless no response to the request made by the computer or is explicitly allowed by default rules. For users familiar with the work of the firewall is not recommended to change its settings, because it can be so that embroil himself banned.
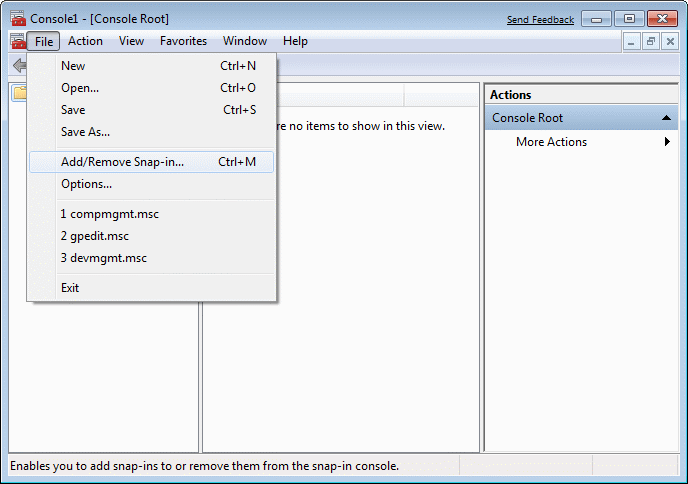
Surveillance systems for security is a very complex task. Basically system protection is achieved by using a set of tools called MMC (Microsoft Management Console), with which, as a small part of the available options, 'introducing' and defines all the firewall settings and monitors the behavior of the system as a whole. Typing the command in the form of MMC main menu |Search programs and files| get the following welcome screen. MMC is used to administer networks, computers, services, and other system components, and one of the tools identified in the menu; gpedit.msc, which is the method of use is shown in Figure 4.4.13.
|
| Figure* 4.5.103 Initial window of MMC (Microsoft Management Console). ( + / - ) |
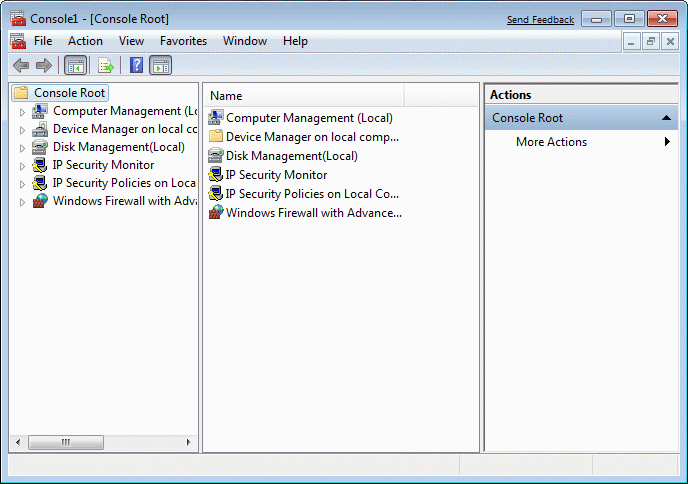
Choice /File/-/Add/Remove Snap-In.../ added to the list of templates that want to configure (remake) for all the major functions of the system. These templates can also refer to software products that are installed on the system written by independent developers. 'Windows Firewall' is just one of them.
|
| Figure* 4.5.104 Using MMC created configuration. ( + / - ) |
In this manner, the settings for the individual components of the system, which will direct the operation of the system according to user preference and can be saved selection /File/-/Save as.../, but some kind of load existing configuration or create entirely new. But for this it is necessary to adjust the system quite some knowledge (MOC for example), and are not recommended for the average user.
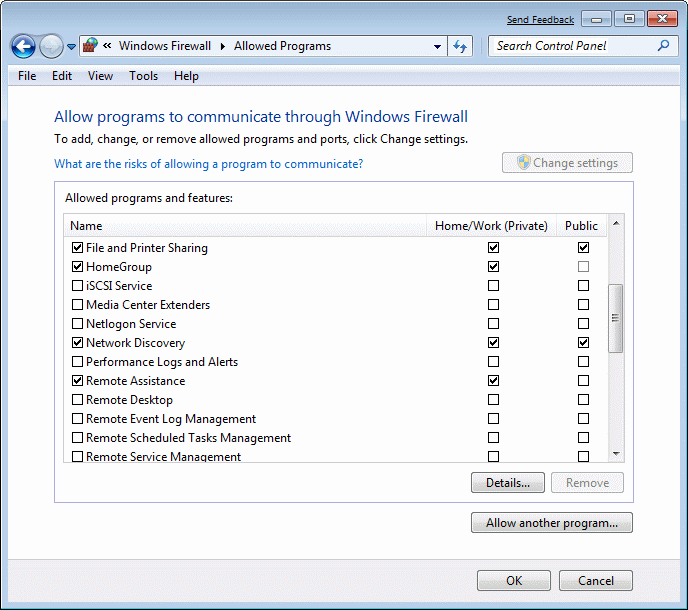
Average user will rely in the main on the queries put to him regarding the firewall leaks or marking off traffic for an application for public and private networks. Therefore it will not basically use selection /Advanced settings/ image with 4.5.38, but the selection /Allow a program or feature through Windows Firewall/ is shown below.
|
| Figure 4.5.105 Configure Firewall for software in the home and public network. |
From the example shows that in a very simple way of putting 'checkmark' to traffic in the home or public network, and that is extremely easy to join some kind of list of executable files, which means to allow both incoming and outgoing traffic for the network where the 'checkmark' is set. For ordinary users typically you set this enough. If the computer is in a private network (SOHO), NAT router mechanism does not allow does not allow outside review of the network and no connection to the computer can not be established if the computer itself is not requested within the network while leaving the Internet. This in itself is already one effective protection. Streamlined SOHO devices have been implemented inside the firewall can filter traffic according to some general principles, prevent 'Port Scan' for example.
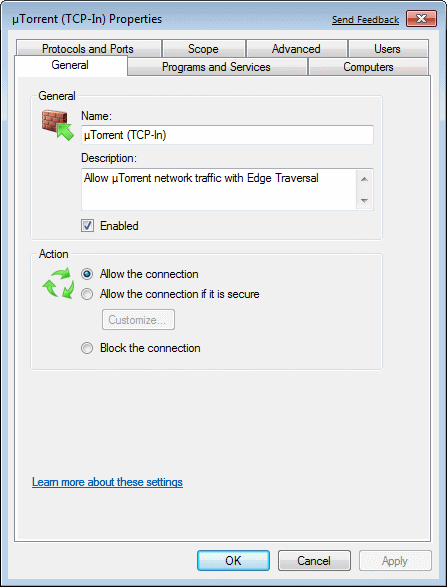
In Figure 4.5.40b shows how the rules for the traffic control is also developed that requires contact with the Internet (uTorrent), and where the firewall settings configured during installation, selection /Properties/ from image provides various setting options of which the most important are shown in the next set of pictures.
|
|
| Figure** 4.5.106-107 Adjusting firewall settings for the installed program support. ( + / - ) | |
Basically, the settings entered in the rules during the installation process needs to be modified, but sometimes there is a need to make further adjustments. Cards ||General|| (Figure 4.5.106a) provides general information about the rule that was added during the installation of software, or a rule that is made for enforceable file (.EXE) selected over cards ||Programs and Services||-|This program|-|Browse| (Figure 4.5.106b) using sites related WE. Every rule in the card ||General|| assigned name that identifies it, a description of what the rule should work, and choice |Enable| which enables or disables the rule, as shown in Figure 4.5.40b seen as green or gray circle with the name of the rule . Permit or block traffic in the connections gives more options. |Allow the connection| miss all the TCP / IP packets that meet all the criteria rules |Allow the connection if it is secure| protected only allows packets IPSec rules, and select |Block the connection| stops all packets that meet all the criteria of the rules.
If in the card ||Programs and Services|| select |All programs that meet the specified conditions|| allows you to send and receive packets from any program on the system that just is not wise unless you want to test the functionality of undefended connection, and the choice |This program| refers to only one selected .EXE file, be it active or not, when the choice |Services| allowing the rule to apply to all processes and services to support the operation of the program (most common choice), only the services or just specific services. So, the first option is the most strict.
Card ||Computers|| is active only if the selected option ||General||-|Allow the connection if it is secure| that defines a set of rules of IPSec activity. Then the choice that allows your computer to be accessed by following the rules and the rules that computers do not apply. This applies to computers and groups that are defined in the 'Active Directory', a technology that allows the operation of the system based on the information and settings from the control center database that is being edited with MMC. Similar to boiling and the card ||Users||. These two cards are shown in Figure 4.5.106c as animation. Typically, these settings are not used in the home environment.
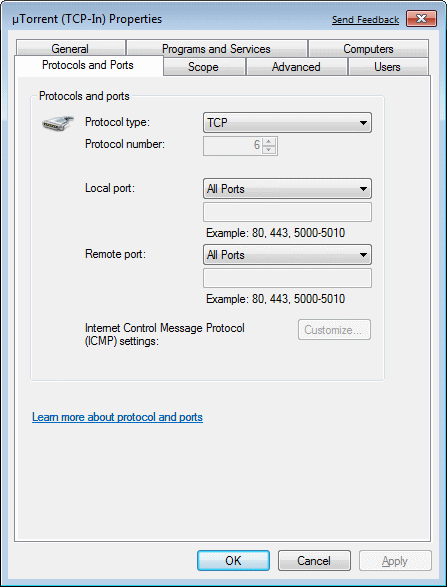
Card ||Protocols and Ports|| (Figure 4.5.107a) and animated shows that all protocols can be monitored, and the chosen protocol rules will apply. But that's not all the protocols. If we choose |Custom| type protocol option is available |Protocol number| that allows you to select any number of protocols, which is defined by the IANA (Internet Assigned Numbers Authority). If using TCP or UDP protocol type available is a choice of local or destination port to be used, any (all ports) or a specific. How to use this card implies a complete knowledge of TCP / IP stack, this chapter will mainly use professionals, and ICMP (Internet Control Message Protocol).
Card ||Scope|| (Figure 4.5.107b) defines a range of local and destination IP address to which to apply defined rules. Mechanism for adding addresses in the range in both cases is the same. Common choices are available for the installation of software |Any IP address| which means that the rules defined in the firewall for all valid IP addresses from which the PC communicates with the Internet. This option is generally more powerful than the election |These IP addresses| which lets you enter a range of IP addresses to which the rule applies, by the definition of a single IP address to define all IP addresses on the network or subnet, or a range of defining the start and end address in an network, either IPv4 or IPv6 format that can not be mixed. How to format defining the range of IP addresses used in the example shown illustrates the card. The rule can be very useful if, for example, for one application, as well as anti-virus, only defines the address of the server where it will take on new definitions, and taking up with other IP ban. IP addresses that should be allowed as 'acceptable' for the computer are: the default output (default gateway), DNS server, DHCP server, WINS server and local area network (subnet) in which the computer is a member of the public in respect of access to available resources.
Card ||Advanced|| (Figure 4.5.107c) the possibility that the rule is applied to the desired types (profile) network: business domain and / or home network (private), and / or a public environment like a coffee shop or pub (public). Besides the above, we can define the kind of devices for network connectivity (Interface types) by the same rules. Image is animated and the final section shows a possible choice for delimiting (Edge Traversal), and marking off or leaks 'irresponsible' traffic which failed network device that provides NAT. Thus, a distinction only applies to incoming traffic and misses such traffic to the Web server in the network is secured NAT. Stated, if not a necessity, it's not good to allow the computer, but it's good to miss this traffic router (router) to the Web server. In a home network, this is of no importance, but in the SOHO environment with a 'public' server on this should be taken into account.
SUMMARY:
These descriptions provide a brief insight into the capabilities of firewall, which are far more powerful than the description that belong Figure 4.4.41. It requires users complete knowledge of the progress of Internet traffic between your computer and the Internet, and is therefore better for the average user that all firewall settings leave as they took advantage of some software during installation. What the average user can do is to support a particular program, which used the firewall to communicate with his headquarters, prohibiting any traffic that does not go his automatic updates or notices about the new version of the product, or some kind of annoying advertising, etc. (for 'Adobe' or 'Roxio', for example), as if out of nowhere :-). But professionals will appreciate its capabilities.
Firewall is necessary to join the antivirus support, because the operating system manufacturer has not implemented. Since the firewall is implemented in the system is good enough basically the user does not need a special Internet solutions, but was sufficient and learn about all sort of software as 'Avira' recognizable icon with painted umbrella in the previous examples. In the business environment, the protection of servers caring, professional antivirus support that from your server continuously monitors network computers and professional network devices and their services. After all, at home (SOHO) and business (LAN) environment, but is common to all the computers and other network devices and computers 'hidden' behind it, in a private computer network, one of the essential conditions for achieving effective protection.
New Trends for security control to the point that if it is determined that the computer does not have an updated anti-virus or other protection, contact the operating system switches the computer connected to the terminal and the outdated computer only allows traffic to the IP address of the server that provides the software upgrade support. Aspects of security firm defines itself by its systematic policy, which can be very restrictive (allows connection to the Internet just a computer network administrator and one that is not on the local network) or very liberal (anyone can use it at the sole discretion). In another case, the administration is very difficult and involves educated users.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |