User Account, Parental Control and CardSpace |
The user on the system identified by its name, but the name does not identify the system. Its true identification system identified by their identification number (ID) that he assigns a random process when creating. The system can not exist with the same user ID. Figure further illustrates everything that belongs to the user on the system.
|
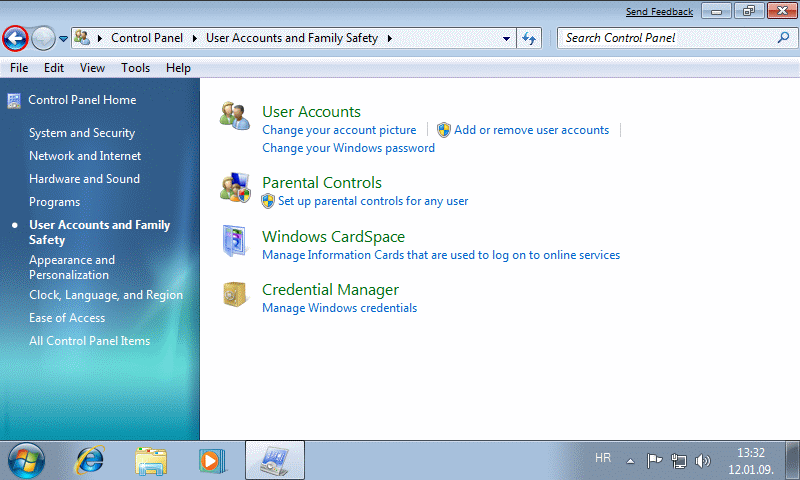
| Figure 4.5.60 Settings of user account. |
Blue button with an arrow to the left and is mapped to the links of the page to descriptions of system configurations.
User Accounts
The initial account is achieved by creating a user name and password in the process of installing the operating system. Each user belongs to one of the possible groups, based on which it depends powers to work with the computer. User 'Administrator' has the greatest authority on the system, and users belonging to the administrators also have very large powers, but not all the powers as user 'Administrator'. Users and groups are explained in the description of the picture 4.5.31.
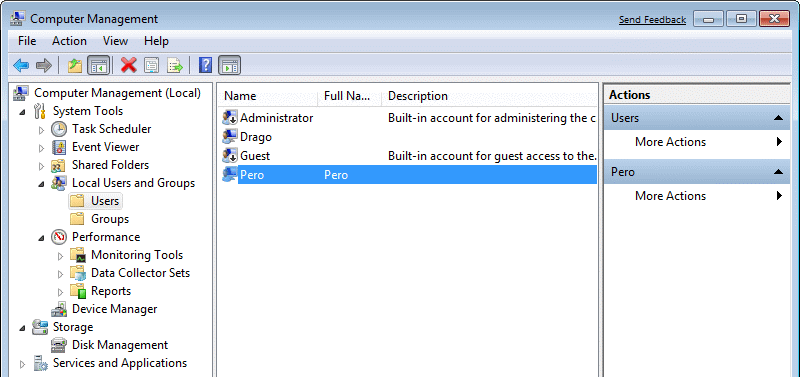
This means that when a user is deleted, a new user with the same name will have a second ID. If, for example, the system creates a user 'Pero' as shown below 4.5.61a, who joined the directory titled as shown in Figure 4.5.61b. If users 'Pero' is removed from the system, the specified directory is not automatically deleted from the system, but should be erased by the WE after the user removes. Quoted in full can be done only 'Administrator'.
|
| Figure*** 4.5.61 Peculiarities of account - Identification. ( + / - ) |
However, if a user contents that belong to the 'Pero' are not removed after its deletion from the list of beneficiaries, and re-creating the users 'Pero', will get a new ID, and the working directory is already existing names changed as shown in Figure 4.5.61c. So, when you delete the user must be erased his directory by WE. The user can change the name to 'Haso', for example, but it does not change the ID, and that the working directory associated with the ID he still remains the accompanying directory called 'Pero'. Furthermore, changes in the user's name, as shown in Figure 4.5.61d, do not change the name of the directory user. In Figure 4.5.62 shows the user 'Haso' where the working directory still has the name 'Pero'. With the changes the user's name, erasing them and creating new users really need to be careful, because it can easily get to the mess that is difficult to discern. Therefore, if some changes are made in the above sense on a computer, the first thing you should do is to 'capture' a real situation, and only then decide what to do and how.
Parental Controls
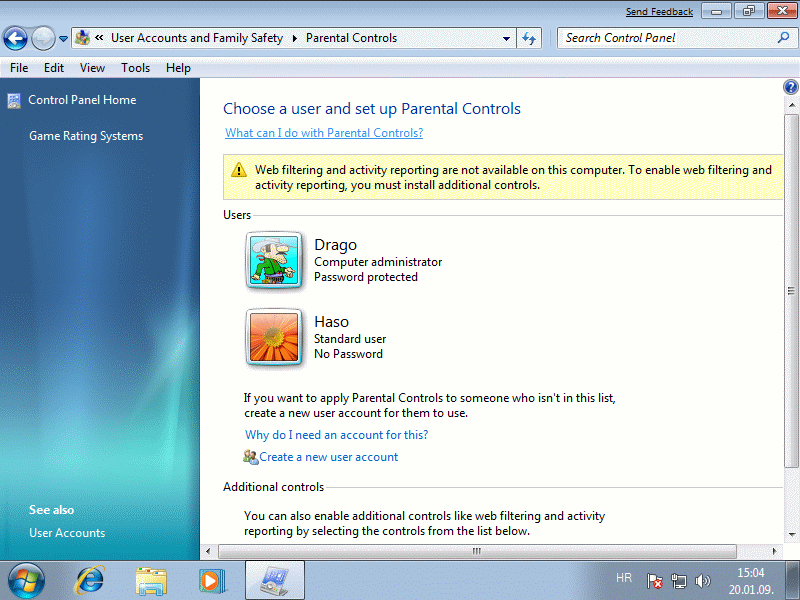
Each of the users can join him akin to the user, which is the property of his master user can limit the powers, such as children. Parental Controls.
|
| Figure 4.5.62 Setting relatedness of accounts. |
It is a centralized monitoring of existing users, such as users 'Drago' can monitor users 'Haso' on his way to say, at different times, limit or interfere with the work on specific applications; ban certain games during the afternoon in time for study. But with this control should address the parents of small children :-).
Windows CardSpace
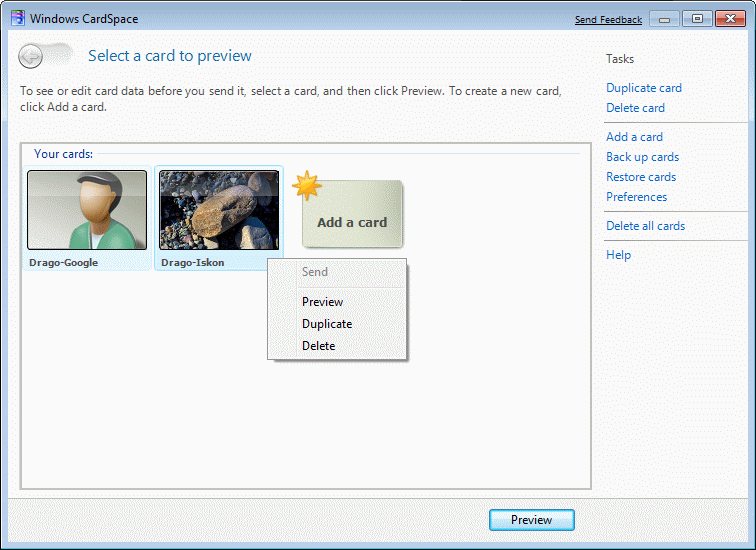
The cards are used for storing user data or the person with whom you communicate around the world. It's kind of directory of contacts that are on the system is kept encrypted. Personal cards can change the data. Cards that are included in the collection obtained from persons or firms with whom contact can only change the name.
|
| Figure 4.5.63 The contact card of person. |
These cards should allow better communication with the user's business environment. Not necessarily all data entered in the ID of user card, they can indeed be used to create more of them each contain only those data that are necessary for individual contacts. For added protection, identity card user can assign a PIN (Personal Identification Number) or password. So, the cards represent unique digital identity. How will these cards be used in practice for the Croats, time will tell.
Credential Manager
Credentials would basically should serve to simply log on to the Internet, or some service. Opening the choice /Windows Credentials/ open a window in which you should enter the resource (an arbitrary name for whom valid credentials, the name of your ISP, for example), the login user_name and password to the resource, as shown in Figure 4.5.64b. Figure 4.5.64a shows a created credentials.
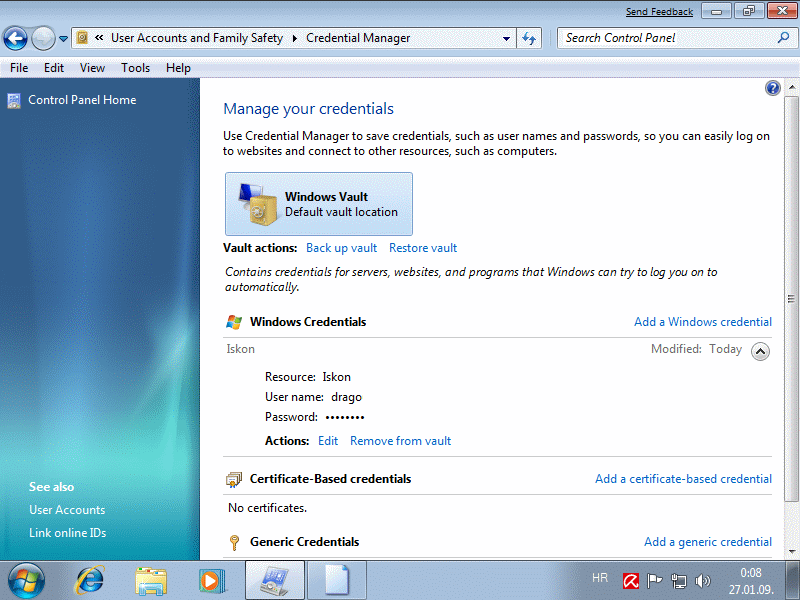
|
| Figure* 4.5.64 Creating credentials. ( + / - ) |
Since the encrypted credentials are good for any communication that is possible to help him use it.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |