5.1.4. Basic commands of operating system
|
 |
 |
 |
 |
According to the already mentioned, a user who has an account you can login to the system. If you use the console or terminal-emulator for system administration offered work through the shell - COMMAND INTERPRETER, by default shell is BASH, allows command task to the system. General command is the process that is to be executed and that the execution of orders received over the input and gives a result in one of the exits, according to the following picture.
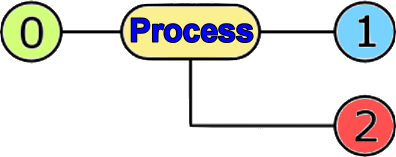 |
0 - standard input (stdin)
1 - standard output (stdout)
2 - standard error (stderr)
|
|
Figure 5.1.9 The process and its basic input / output characteristics. |
The usual standard input is the keyboard, or the keyword listed options and arguments. With pressing <Enter> shell allows the process to take the order, comply with his treatment and if all went as expected result of the process passes to standard output, and if not forward it to the standard error. Based on such understanding process activity leads to the conclusion that one of the outputs can be input into another process and exit from it in the next entry - CHAINING.
Either way, there are a lot of commands, more or less complex and with more or less options. All this has a lot and so it is constantly consulted help pages or literature. The execution of a command is a process, that when it comes to red for thors doing their share, is expected to accept data input (stdin) - read operation from either the keyboard or the contents of a file or the output from another process, and as a result has properly processed data at the output (stdout) - write operations, or an error message if the treatment failed or interrupted (stderr) - error messages. All activities of the process are recorded in the corresponding files to monitor his work, so LOG file in the [/var/log] directory.
During operation, the user has a need to 'cleanse' display to clearly read the result of the next command. The command ' clear ' serves for this purpose. Commands that were previously shown, as well as contents of a directory in which they are located, are the most fundamental part of the operating system, resulting in installing the operating system over the network without requiring any additional program support that is shown in Figure 5.5c.
All commands are available to users. If you want to execute some special actions, particularly changes in the configuration file directory [/etc] or upgrade the system itself, a user must have the authority of supervisors, which is identified by the username ' root '. Apart from the console, there is no other way to directly use the username ' root '. The powers of a system administrator can be achieved through the terminal command ' su ' as follows:
drago@voda:~$ (users 'drago' positioned in its working directory)
drago@voda:~$ su - (command to obtain the status SUPERVISOR (root);
following query type the password for the 'root'
user with the transfer of environment variables)
voda:~# (working directory of the user 'root')
voda:~# cd /
voda:/# (root directory of the system)
Administrator privileges may be restricted only to the target group of users, so if the system is to be used under strict supervision, provides the root user only from the console. Way of getting the root authority is shown in Figure 5.1.2a. In addition there is a brief description of the main commands of the system, which are located in directories [/bin], [/sbin] and [/usr/bin]. For efficient use of commands before that should always read the instructions that describe them in detail, particularly with regard to a multitude of options. The basic syntax of the command is described in specific terms of IT, Chapter 5.1.1.
Fundamental commands
A number of them in the examples so far used include, but here most of the controls and relevant Key Words (KW). Further shows commands to read instructions for key words and basic file system commands.
- man X KW - Instructions for command to the section where X belongs. Reviewed, page by page until the end when the view automatically. Exit is the key ' q '.
- info KW - Instructions for the command in the format similar to the hyper-text. Exit is the key ' q '.
- help KW - Instructions that refer only to commands built into BASH shell.
- pwd - Shows the position as the directory of the system in which user is currently located.
- cd [/directory_1/directory_2/... .../directory_N] - Moving to the directory [directory_N]. If the option is not directory path to the task the user is directed to your starting (home) directory. The command ' cd .. ' moves the user to the parent directory, and the command ' cd / ' sets the user to the root of filesystem.
- mkdir new_directory_name - Creating a new directory, where it is recommended that in the name of directory is used ' _ ' instead of a space character.
- mv source_directory/file destination_directory/file - Moving original content to the new location, erasing the original location. Also a way to change the name (rename) directory/file.
- cp source_directory/file destination_directory/file - Copy the contents to the new destination. With the appropriate option (-P) transferred the rights to the content.
- rm file - Irreversibly removes (deletes) file. In Windows operating system deletes only the first letter of the file name and the eventual repair is possible, while in the operating system to place deleted files recorded zero. Therefore, with this command should be careful because there is no turning back. Especially be careful with this command if used recursively through directories.
- rmdir directory - Irreversibly removes (deletes) directory. Directory for security can not be deleted if not deleted all previous files in it.
- chmod - Change the value for the record '_rwxrwxrwx' in order to provide appropriate rights owner of the file, group of users or all users, the term 'all users' thoughts on users from other computers accessing the computer. The basic syntax using the command, without options, is: ' chmod octal_number name_of_file/directory '. Each ' rwx ' combination may be ' ___ ', ' __x ', ' _wx ', ' r__ ' and remains. Character ' _ ' Character '_' is associated with a zero, and other indications of units. On the basis of the associated unit to zero and octal number system, a combination of characters corresponding to the value 0, 1, 2, 3, 4, 5, 6 and 7. By entering the command, e.g. ' chmod 755 name_of_file/directory ', file gets the right ' _rwxr_xr_x ', which favors the rights of directory and files for reading web content. Moreover the directory will not be specifically mentioned, if no special needs, because in Linux everything is a file.
- chown - Change owner of file / directory. It might just be one of the beneficiaries of the system. Users of the system can be a normal user, supervisor (root) and services (mail, bind, sshd ...). The basic syntax is: ' chown user_name name_of_file/directory '.
- chgrp - Change the user group file / directory belongs. Group can be user_name file owner or some other in which a consolidated with several of users, as a group ' www-data ' which refers to Web content. The basic syntax using of the command is: ' chgrp group_name name_of_file/directory '. When needed in the file [/etc/group] can be defined any group name and assign it to users to be able to use its files.
- ls - Command to view the directory. In previous examples shown in several places, mainly with the option ' ls -alh '. Counterpart of this command is the command ' dir '. For other options (sort by date of origin, for example) should refer to the help pages or literature. Files can not be recognized by their names but by the unique identifier (UID) that with the name of the file contains information such as its other attributes, access times, size and so on. The file system can accept only as many files as you can write a UID. So it can happen that a seemingly blank disc can not 'receive' more new files, because the list is filled with many small files.
- pico file - Simple and affordable editor for editing text files.
- vi file - A powerful editor to edit any kind of file, very useful for administrator and developers.
Manage file system
Linux file system is based on a unique original location (the root), which is simply denoted with a ' / ', which are connected to all the files and directories associated with their directories and files and so further to FSSTND hierarchical structure. The basic feature of this concept is that for any directory in the structure can 'hook' the new structure set up by the same principle. Commands for working with the file system are:
- df - Report on the availability of disk devices. The most commonly used with the options ' df -kh ', in order to obtain the human readable and understandable display.
- mkfs - Creating a file system, of which the most common ext3.
- mount - Connect the device or directory system as well as drive, stick or optical devices, as in 'Example III'.
- umount - Unbinding device of the system, as in 'Example III'.
File
Commands that follow refer to the file, whether it is related to the physical device, the executable (binary) and directories, as well as text files. The commands used for its retrieval and browsing. The purpose is to obtain usable although in view of their misuse can in the worst case, make that everything on the screen illegible.
- cat - Command to view the text (txt) files without keeping the display until the end of the file contents. The basic syntax is: ' cat name_of_txt_file '.
- more - Command which has a purpose with chaining ( | ), as with the previous example, to obtain the ability to view one screen display on display until the end of the file. The basic syntax is: ' cat name_of_txt_file | more '.
- less - Command greater features of the ' more '. Provides an overview of the file contents to help along the vertical arrows. The basic syntax is: ' less name_of_txt_file '. Interrupt the display performed via the ' q '.
- head - Default command which allows you to view the first 10 lines of the file. Options, this number may change. The basic syntax is: ' head name_of_txt_file '.
- tail - Default command which allows you to view the last 10 lines of the file. Options, this number may change and allow dynamic changes to the end of the file (option ' -f ') to be in operation complements its contents. It is very suitable for monitoring the contents of the LOG file. The basic syntax is: ' tail name_of_txt_file '.
- od - Command to view binary (bin) files where its composition is displayed in groups of octal numbers. Option can get hex display, and display obvious character instead of numbers. The basic syntax is: ' od name_of_bin_file '.
- dd - Is used to copy data between files, or files associated device.
- find - Used to locate the file in the file structure. No beneficial effect without options ' / ' to the market from the root tree structure. Thus, the syntax is: ' computer_name:~# find / -name file_name '. To find a file, regardless of its associated libraries and instruction, can be used and built command ' type ' by the syntax: ' type file_name '.
- xargs - It is used to display the result of the command in the understandable parts, most commonly used with the command ' find '.
- grep - The simplest application is to look for a term in a file by syntax ' grep term file_name '. By chaining commands extracts the desired term from the list of files, for example, by the syntax: ' ls -al | grep term ', It is also used for finding files that contain the desired term by syntax ' grep term * ', so with the use of 'Joker', and does it in the directory where it is activated. If the option to use recursion (-R) search for files through all subdirectories of where is the default.
- file - Shows you what is kind of file. The syntax is: ' file file_name ' if the command executed where the file is to be reviewed, or otherwise to indicate the path to the file ' file /directory_1/.. ../directory_N/file_name '.
- whereis - Easier search where the file is located and all its components (libraries, user ...) according to the syntax: ' whereis file_name '.
- touch - In the area which is the default creates an empty file size 0 B. Command Syntax is: ' touch /directory_1/directory_2/.. ../directory_N/file_name '. If the cursor is in the desired directory syntax is much simpler: ' touch file_name '.
Display control
When the display during operation shows 'junk', or by pressing the arrow button to receive some unimportant character, one may serve to save the commands in this chapter.
- tput clear - The command ' tput ' read sequential database with data for the terminal and the base sequence translates into a sequence of control characters to the screen and sends the characters to the screen. Then ' clear ' clears the screen and sets the screen prompt and the cursor in the upper left corner.
- tput rmacs - The combination ' tput ' with ' rmacs ' switches to an alternate set of characters. This command is used to stop the on-screen display 'rubbish' about graphics and signs and displays the correct corresponding text.
- stty - Control communication between VDU - Visual Display Unit (Monitor) and PC.
- clear - Deletes the contents of the entire screen, and if the command successfully executed, at the top of the screen shows only the prompt and cursor. It is used when the image on the screen wants to 'cleanse' in normal operation.
Compressed files
In order to save space on your hard drive, a lot of files that are used are compressed. Programmes such as 'gzip' or 'compress' substantially reduce their size, often more than three times. In the era of disks with large capacity stated it more relevant, but it was as a rule. Compressed files can not be read directly, but first be unzipped. Some software, as well as the ' GNU Midnight Commander ' - ' mc ', has an integrated mechanism for extracting the file to a temporary file in the directory [/tmp] and read its contents.
- gunzip - Command syntax is: ' gunzip compressed_file_name.suffix '. Suffix is commonly .gz or .z. By decompressing the file is written to the original name and delete the original default zipped file.
- zcat - Allows you to view the contents of compressed files using temporary decompressed file. Use the command syntax is: ' zcat compressed_file_name.suffix '. So extensive capabilities of command ' cat '.
- zmore - The syntax for this command is: ' zmore compressed_file_name.suffix '. Expanded capabilities command ' more ' with the use of temporary records decompressed.
- zless - The syntax for this command is: ' zless compressed_file_name.suffix '. Expanded capabilities command ' less ' with the use of temporary records decompressed.
- zgrep - The syntax for this command is: ' zgrep compressed_file_name.suffix '. Expanded capabilities command ' grep ' with the use of temporary records decompressed.
Backup
Regular backups are required, especially if the server is standalone and does not replicate with another in a network, in order to be able to recover the system and data in case of disaster. To get full access to all the files you need to archive, a full backup must be performed by a superuser. Subsequent programs (commands) are used for making backups of different types:
- tar - This command has many options, from storing data in a file to store the data to tape in its original format or compressed. More detail in Chapter 5.1.7.
- cpio - Used for backing up individual files. Prepare a list of files that are sent to chaining the standard input of command ' cpio '. How to use these command to archive [home] directory on the SCSI tape device is: ' find home -print | cpio -ovBH newc > /dev/st0 '. Archived data are read from tape with chaining commands: ' cpio -itBH newc < /dev/st0 '.
- afio - Command is similar to the previous but allows the compression of data before writing to tape: ' find home -print | afio -ovZ > /dev/st0 '.
Control over events
The events are a series of events between applications on your computer system and check-out from your computer system. Be aware that by signing up to the user to gain administrative rights, can do great harm to the system just plain wrong typing commands. Especially if no command has recursive properties.
- login - Log in to the system via terminals or applications from one computer to another on which she also has an account over SSH as program support, or registration supervisor in the name of a user account on the computer that is currently maintains in order to take over his identity. This is done in more detail command: ' voda:/# login USER ', which becomes the supervisor: ' USER@voda:~$ '. From the above it is clear that the supervisor must be a highly moral person.
- exit (logout) - The command to leave the shells, the observed current user or in general, check out some process or system.
- script - The execution of the script, as discussed in Chapter 5.1.6.
- tty - Shows that the terminal is currently being used. It has been said that through the console user can log over six non-graphic and one graphic terminals. The same can be done through the terminal-emulator.
- ps - Overview of the processes that are set up and run on your computer. Each process is described parameters as in the following example, which is obtained by the command ' ps -el ' get a description of the state of the process at the moment of giving command to the next display.
voda:~# ps -el
F S UID PID PPID C PRI NI ADDR SZ WCHAN TTY TIME CMD
4 S 0 1 0 0 80 0 - 525 - ? 00:00:00 init
5 S 0 2 0 0 75 -5 - 0 - ? 00:00:00 kthreadd
1 S 0 3 2 0 -40 - - 0 - ? 00:00:00 migration/0
1 S 0 4 2 0 75 -5 - 0 - ? 00:00:00 ksoftirqd/0
5 S 0 5 2 0 -40 - - 0 - ? 00:00:00 watchdog/0
:
4 S 0 1794 1 0 80 0 - 656 - tty1 00:00:00 login
:
4 S 0 1852 1794 0 80 0 - 1054 - tty1 00:00:00 bash
:
0 S 1000 2112 2111 0 78 -2 - 1176 - pts/0 00:00:00 bash
4 S 0 2117 2112 0 78 -2 - 942 - pts/0 00:00:00 su
0 S 0 2118 2117 0 78 -2 - 1045 - pts/0 00:00:00 bash
4 R 0 2141 2118 0 78 -2 - 872 - pts/0 00:00:00 ps
voda:~#
The processes are grouped in a sequence by activating and describes them: flag (F), status code (S), numeric identifiers UID (User ID), PID (Process ID) and PPID (Parent Process ID), CPU occupancy (C), priority performance (P) and other indicators. PPID is the parent process of the process PID and PPID if the process is stopped, it should disappear and the PID process. But it happens to PID process remains active and does a task that does not serve anyone - zombie process. If the process starts when you turn on and never stops called DAEMON or service, as well as e-mail, DNS and DHCP services and the like.
The second column is interesting because it describes the state of the process at the time of their examination.
D Uninterruptible sleep - Continuously sleep
R Running - Is conducted
S Interruptible sleep - Sleep and wait for some event to activate
T Stopped - Had done and stopped
X Dead - Turned off
Z Zombie - Running unattended, forgotten, without superior process
'Zombie' process is certainly not useful to always have it when reviewing the state of the process to 'kill', especially if it needlessly consumes resources (RAM).
- top - Shows how the tasks are performed on the operating system. The display changes periodically, e.g. every three seconds.
top - 01:28:47 up 9:36, 2 users, load average: 0.00, 0.00, 0.00
Tasks: 41 total, 1 running, 40 sleeping, 0 stopped, 0 zombie
Cpu(s): 0.0%us, 0.0%sy, 0.0%ni,100.0%id, 0.0%wa, 0.0%hi, 0.0%si, 0.0%st
Mem: 126448k total, 58304k used, 68144k free, 13192k buffers
Swap: 361420k total, 0k used, 361420k free, 21228k cached
PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND
1 root 20 0 2100 688 588 S 0.0 0.5 0:00.76 init
2 root 15 -5 0 0 0 S 0.0 0.0 0:00.00 kthreadd
:
2112 drago 18 -2 4704 1928 1348 S 0.0 1.5 0:00.00 bash
Most important to review the status of CPU utilization and working memory and presence of 'zombie' processes.
- kill - If the process has become a 'zombie' needs to be 'kill', and if he started acting weird and can be re-run in a way that sends the appropriate signal. First, perform the command ' kill -KILL PID ', and the second command ' kill -HUP PID '. Useful command.
- init - Command that with the numeric value to change the modes described in Chapter 5.1.1. So command ' init 0 ' turn-off the computer, and command ' init 6 ' performs a restart with proper shutdown procedure and then restart the computer without physically turning off - REBOOT the computer. Services to stop and start again, using a script - RESTART service. The violent extinguishing computer can corrupt the file system.
Users and computer
Commands that relate to the user's identity and the identity of the computer are:
- adduser - Command to be used only by supervisor syntax: ' adduser user_name '. Then seeks to enter the names of users, password, and some more information and then create a user account confirmation.
- deluser - Command to be used only by supervisor syntax: ' deluser user_name '. Since the user can create directories in several places in the file system, usually in [/home/user_name] and [/var/mail/user_name] and sometimes if something is subsequently added. Linked useful commands: ' cd / ls -alR | grep user_name | more ', check if with the username deleted something else is rest.
- su - Assign to admin (superuser) authority to the example at the top of this page, shown in Figure 5.1.2a, and the example in Chapter 5.1.7.
- whoami - Gives the name of the user who is currently using an active shell.
- passwd - Replacing password of user by syntax: ' passwd user_name ' by which follows request to enter a new password and re-enter the query as to its confirmation. If both inputs matching password change is accepted. When entering the password on the screen does not show anything, no stars as at Windows. Password can only be changed by supervisor, and it can happen that if you enter the correct user name that will be executed supervis password change without notice. Stated is a bit inconvenient, you should be careful.
- id - Provides information about the current user: UID, GID, etc., in short all that he along with his identity.
- who - Displays all users who logged on to the system and method for applying: Console (pts) or terminal-emulator (tty). The command is almost pointless since fewer people used the terminal-emulator, especially console.
- users - Gives only the names of registered users.
- date - Reports the current date and time.
Described controls are not all that are in directories [/bin], [/sbin] and [/usr/bin], but are the most important for successful host configuration, monitoring its operation and resolving business problems. In addition is shown only the basic part, without the many other options that can be joined to each command.
Citing of this page:
Radic, Drago. " Informatics Alphabet " Split-Croatia.
{Date of access}; https://informatics.buzdo.com/file.
Copyright © by Drago Radic. All rights reserved. | Disclaimer
|
