7.6.1. SpeedTouch - Basic Configuration |
When a user decides to use ADSL devices to access the Internet, it must be one of the ways to ensure a PPP connection (Point-to-Point Protocol) according to ISP, and as a complement to the PPP protocol regarding the authorization of users commonly use a PPPoA (PPP over ATM) or PPPoE (PPP over Ethernet) protocol and both require authentication by user_name and password. PPPoA resembles the classic dial-up connection without dialing and is used with a modem designed as PCI or USB devices, while the PPPoE requires additional program support (DSL client) that is in Windows XP/Vista/7 operating system implemented and allows access the modem from a conventional Ethernet card. Through the embedded device to bypass traffic and switches in the modem can simultaneously connect multiple users to the Internet, and authorization is done via the settings entered in the router / modem or computer, depending on the mode of operation of this device. This DSL client for older operating systems to be installed.
The following figure shows the contents of /Start/-/Network Connections/ where are the elections for the 'Broadband'' and 'LAN' connection when the device is in 'Bridge mode'. If the device uses a 'Router mode' access ISP is achieved by a user_name and password entered into the device (this is usually done and monitored ISP). Then, simply 3Com network card, according to the example in the following figure, connect the device to the DHCP settings of the computer Figure 7.6.4 deliver the necessary information. There is no icon for the 'Broadband' connection at the 'router mode'.
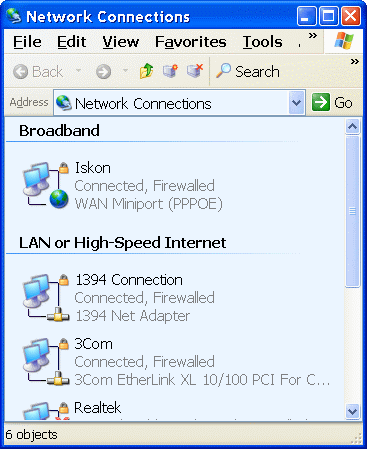
|
|
| Figure** 7.6.3 Network Configure & Authorization. ( + / - ) |
If on the other hand uses the 'Bridge mode', it should establish a connection with the authorization through the computer. 'Broadband' connection is realized by choosing /Network Connection/-/Network Tasks/-||Create a new connection||, where the triggers 'wizard' in which sequence to make a choice |Connect to the Internet|-|Setup my connection manually|-|Connect using a brodband connection that requires a user name and password|-|Enter an arbitrary name for the ISP|-|Enter the user_name and password supplied by your ISP|-|Enable placing shortcuts on the desktop| and then will appear icon 'broadband' connections as shown in Figure 7.6.3a, which has options as shown in Figure 7.6.3b. Settings for the TCP / IP should be as shown in Figure 7.6.4. |Virtual Machine Network service| is an additional option that installs the free software 'Microsoft Virtual PC'. To allow other users-computer local area network access to the Internet, the computer on which the authorization shall be set up that allows forwarding traffic as shown in Figure 7.6.3c.
From the previous chapters can be suggest that kind of OS is not important to take advantage of this device and can be used with computers that have the Microsoft Windows OS (98, 98SE, ME, 2000, XP, Vista or 7), Mac OS X or any other operating system that provides IP connectivity. The only significant difference is the USB driver for the specific operating systems. Of course, you can also connect multiple computers, and if they are to each other 'see' all the computers in the network, connected to 'Thomson gateway' either wired or wireless, must have different names and belong to the same group. If you need to adjust the firewall. How 'Thomson Gateway' has implemented DNS and DHCP support for the computer system it is not a problem to set the network settings on your computer, as shown in the next image should all be set to automatically adjust.
 |
| Figure 7.6.4 Set-up TCP / IP settings of computer. |
IP addresses can be assigned according to the examples in Chapter 4.5.5, but the network settings need not exactly correspond to the models because the ISP can be defined according to their needs, but regardless of the scheme utilized all computers belong to a private ' C ' class.
It is not good to leave the device with all functions available if you really will not use. For example, it is good to take advantage of any firewall, but to completely disable WLAN communication if the same is not used or rarely used, especially if the service is paid to its turnover and not to use an unlimited (flat rate), it will be a great expense if someone unauthorized 'attach'. Safety whatever it was, was not perfect. Therefore, it is necessary to know how to configure the device. SOHO device SpeedTouch 780WL, is that no router, switch, and so a good deal because it combines the functions of active network devices, can be accessed in different ways with different purposes as shown in table below.
| Approach | Purpose |
| Web browser |
Configure the device using HTTP or HTTPS protocol and the web interface with the factory default IP address of 192.168.1.254 (private ' C ' class). If the IP address is changed to use the new IP address entered. Device is accessed with the default USER_NAME and PASS as directed. These data necessary can be changed. |
| C L I Command Line Interface |
Detail adjustment devices using TELNET (or similar) program support, using the set IP address. For detailed instructions on how to use CLI commands should be consulted manual 'SpeedTouch ™ CLI Reference Guide' is available on the Internet. Device is accessed using USER_NAME and PASSWORD. |
| F T P File Transfer Protocol |
OS service that is used by the 'Command Prompt' (Windows XP/Vista/7) It is used to store copies of the protective device settings in a file or to return the same to the device, or to complement the existing settings, using the IP address of the device during the communication with the device. By establishing an FTP session may be necessary to use CLI commands. |
| Remote Assistance |
Permit remote user to be able to configure the device. The device settings then this procedure should allow for remote user to define USER_NAME and PASSWORD. Remote user setup is done through the web interface. |
WEB interface - accessed via http or https protocol specifying in the address line of a web browser's IP address or name that was entered in its DNS table; https://192.168.1.254/ or https://192.168.1.254/ or https://speedtouch.lan/ or https://speedtouch.lan/. The address given in the example belongs to the ' C ' class of network devices and the Internet service provider - ISP, as ISKON or AMIS in Croatia, for example, can be changed according to their needs, and then differ from the factory settings. Address 'https://speedtouch.lan/cgi/b/ic/connect/success/' allows it to be from the local network, the Internet by typing in its view, reset switch on the device without losing configuration settings (RESET).

|
| Figure** 7.6.5 Initial Web interface to configure the device. ( + / - ) |
To the name registered in DNS can be reached by the command 'nslookup 192.168.1.254' in the 'Command Prompt'. The figure above shows the usual interface that provides the user 'Administrator'. The first Figure 7.6.5a shows that earned all three networking device that allows (broadband connection). The second Figure 7.6.5b, which is actually the continuation of image 7.6.5a, shows that the wireless network is currently disabled, the USB communication is not used and that the switch is connected to a computer named 'msi'. Available are two phone lines (VoIP). Underlined names indicate that these joints under subsequent configuration pages. At the top of the display shows that the current user is using a web interface 'Administrator'. In contrast to the usual notion of user 'Administrator', with this device specified user does not have the greatest powers in the work with your device. Potential customers are by definition operating system devices are:
| User | P o w e r s |
| root | The main account without any exceptions or limitations. |
| SuperUser |
A user who can manage services through any access channel from any location. |
| TechnicalSupport |
A user who can manage services but only for WAN environments (ISP's network). |
| Administrator |
A user who can manage services but only for LAN environments (SOHO local network), and can not change the settings for authorization by your ISP. |
| LAN_Admin |
User who can only manage a LAN services through any access channel from any location. |
| Poweruser |
A user who has full GUI (graphical web interface) access via http or https only from the LAN environment. |
| WAN_Admin | Can monitor WAN settings, where does. |
| User |
A user who has a GUI (graphical web interface) access via http or https only for LAN environments and for review only. |
| Guest | User without authorization. |
ISP usually provides its users 'Administrator' which again can impose some restrictions, so you can not for example execute extension program support, Telnet or FTP connection, add the user 'Guest' and the like. What is allowed is quite enough to effectively manage local SOHO network, without having a thorough knowledge of 'Administrator' on the device. This means that you will not be able to use all the features described in the PDF manual of the device, but only what enable the user to the ISP, and that's more than enough.
When the device is turned on, along with a brief agreement between the service and the ISP, all traffic is automatically set and no need of the user for some specific interventions for common use of the network, which implies the use of World Wide Web, e-mail and VoIP services. From the factory manual shows the device is possible Telnet and FTP communication with the device it is for safety reasons by the ISP disabled. Telnet and FTP allow the use of the CLI (Command Line Interface), commands are entered by typing the keywords such as: adsl info, connection info, firewall list, and still many others that can be fine 'tune' the device. ISP, as ISKON in Croatia, the usual unit leased, which is convenient for the user who does not need to care about his repairs or replace or maintain.
FTP, Telnet, and especially in the world of communications networks usually are prohibited and shall be allowed, if necessary, use SSH (Secure SHell) software and support for one another service because then all traffic encrypted. As most users are generally sloppy ISP stated the only way to protect yourself and them. When the computer is connected to 'Thomson gateway' from the command window can read the settings of network communication known IPConfig /ALL.
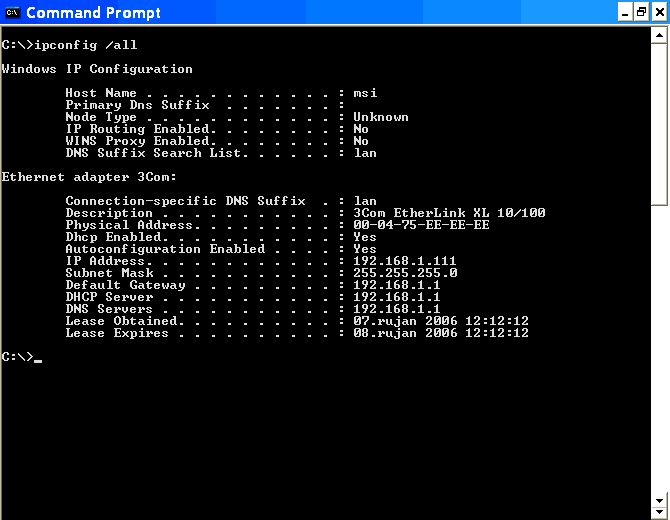
|
| Figure* 7.6.6 Network settings in 'router mode' & 'bridge mode' operation. ( + / - ) |
Of course, this is a Windows XP/Vista/7 operating system and its 'Command Prompt' window. The text is written command of mixed upper and lower case in the example shown in Figure lowercase. Stated deliberately done to warn the reader that the Windows OS detects commands written and upper and lower case and that there is no real difference. The difference is made in cases where it is necessary, when the definition of passwords for example. And that means a small lineup after 'C:\>' at pictures? If you are unsure see Figure 4.3.3 and read the chapter on DOS. Address for 'Default Gateway' is nothing more than an access device address, which often have a web-based interface for parameter setting, which is not as efficient as set via the command line. Unfortunately setting via command line ISP gladly off.
Display in the command window indicates that the DHCP service is enabled it follows auto-configuration and automatic assignment of IP addresses of the computer, its associated subnet mask, default gateway IP address, and the address of the DHCP and DNS server (Thomson Gateway) and time settings using the forwarded address computer. Indicated an acceptable solution if you do not need to exchange data between computers. For an bookkeeping service, where they will be offered one computer to other computers in the network database of some sort, it is better to their computers to assign a STATIC IP address, this device allows the truth via the DHCP service, but the outstanding feature is activated |Always use the same address:| in the configuration of the connected computers. Configuration with pictures 7.6.6a is a possible example of the network settings when connecting to the network when the device is operating in a 'router mode', and the configuration with images 7.6.6b is a possible example of the network settings when connecting to the network when the device is in 'bridge mode'. In the first case regarding the authentication settings are written into the 'router' - a network device, and in the second case are defined in the settings of 'broadband' network connection in the configuration of the computer where the network device behaves similarly to the modem.
As in the two-mode devices outside the network parameters monitored ISP, and that they are not relevant to the internal market, the device settings for internal circulation are adjusted according to the rules for private ' C ' class networks. When connecting two or more computers in the local network must comply with the principles described in Chapter 4.4.4 or 4.5.5. An example of networking devices is shown in Figure 7.4.16.
|
Citing of this page: Radic, Drago. " Informatics Alphabet " Split-Croatia. {Date of access}; https://informatics.buzdo.com/file. Copyright © by Drago Radic. All rights reserved. | Disclaimer |